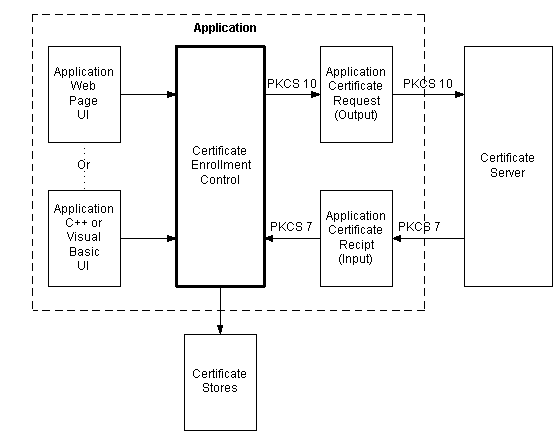
The CEC is designed to make it easier to develop an application that must request that a certificate be issued to a named subject. It is designed to accept data, in the form of a binary string (BSTR), from a web page, or from either a Microsoft® Visual Basic® or C++ user interface. The output from the CEC is a PKCS #10 certificate request, that can be sent on to a Certification Authority (CA) or a certificate server as shown in the following illustration.

Necessary information about the user (certificate subject) is collected by the User Interface (application), and is provided as a BSTR input to the CEC. The CEC generates the appropriate (signature or key exchange) key pair, and then generates and signs a PKCS #10 certificate request, using the generated private key. The CEC then stores the keys with the certificate request for later use. Next, the application sends the PKCS #10 to a certificate server or certification authority.
When the requested certificate is returned from the certificate server, the application passes the PKCS #7 message back to the CEC, where the certificate (or chain of certificates) is pulled from the PKCS #7 message. The user's public key (previously stored with the certificate request) is added to the newly received certificate, and the certificate is stored in a certificate store, as are any other certificates in the chain of trust. Any certificate-aware application can now access this certificate from the store.