Within large organizations that are composed of small, multiple units, the need for each unit to manage their own resources on the corporate intranet is commonplace. Each unit must enforce the policies under which approval is granted to requesters to gain access to their intranet resources.
Providing these units the ability to set policies and issue certificates themselves can be accomplished by allowing them to become certifying authorities, each with their own Certificate Authority (CA) server. Proliferation of multiple CAs within an intranet should be monitored closely by the parent organization so no misuse of authority occurs.
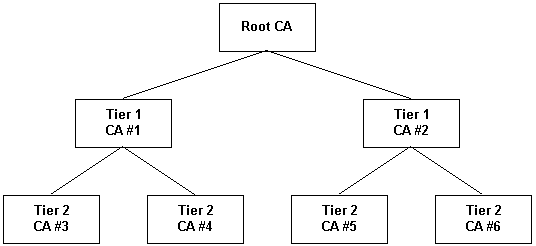
Misuse of authority is addressed through use of a Certificate Authority (CA) hierarchy. The CA hierarchy begins with an ultimate certifying authority called root. The root authority certifies CA servers within the parent organization to enforce security and control throughout the entire system. In large organizations, there may be multiple tiers of CA servers so the hierarchy can be deployed throughout all the units in the parent organization. For example, a first-tier CA would be certified by the root CA, and would then certify a second-tier CA, as shown in the following diagram.

The use of a CA hierarchy provides large organizations with the flexibility needed to manage policies and grant certificates throughout a certification system composed of multiple certificate authorities. A CA hierarchy enables a certification system to be managed from a single control point. For example, the root authority could employ hardware-based key management so a specific, subordinate CA is certified under the greatest possible security.
When a certificate issued by a Tier-1 or Tier-2 CA is transmitted on a network, the recipient must verify that the issuing CA has been certified by the level above it, and that the one at that level has been certified by the one above it, until a chain of authority exists between the lower-level CA and the Root CA. For example, in the preceding diagram, it could be verified that CA #4 was certified by CA #1 and that CA #1 was certified by Root CA.
If for some reason a lower-level CA mismanages the issuance of certificates, the relevant server certificate can be revoked by the root authority. This effectively invalidates certificates issued by the lower-level CA without affecting any other certificates issued within the parent organization.