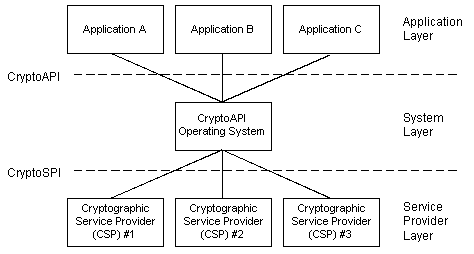
As the following illustration shows, applications don't communicate with CSPs directly, but instead make calls to the CryptoAPI (exposed by the operating system's Advapi32.dll file). The operating system filters these function calls, and passes them on to the appropriate CSP through the CryptoSPI.

Applications refer to data objects within the CSP via handles. Some examples are key containers, hash objects, session key objects, and public/private key pair objects. It is important to realize that these handles are opaque from both sides. That is, the handle that the application sees is not the same one that the CSP exports. For various reasons, the operating system layer performs indirection on all data object handles.