When a user or a client application attempts to change a directory object or seek information on it, that request is granted or denied according to the permissions the requestor has on the object. These permissions are stored in the discretionary access control list (DACL) of that object.
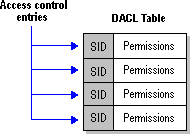
Every object in the directory information tree (DIT) has an attribute called a security descriptor. This security descriptor is a binary value that contains the discretionary access control list (DACL) for that object. The DACL consists of a list of security identifiers (SIDs) and the specific permissions for each SID. The SID is a value generated for every new Windows NT user account for security and identification purposes. Microsoft Exchange Server uses the SID to identify the account for directory security.
Each DACL is a table, structured as shown in the following diagram.

Structure of a DACL
The permissions stored in an objectís DACL can be viewed through the Administrator program by looking at the objectís Permissions property page.
An access control entry is added to an objectís DACL when an administrator or a process assigns a role or individual access permission to a user for a given object. For example, when a mailbox is created and its primary Windows NT user account is assigned, an access control entry indicating the role of Mailbox Owner is created for the owner and stored in the DACL of the mailbox.
You can also add or change access control entries by using directory access functions such as BatchImport and DAPIWrite. These functions use several pseudo-attributes to convey information that will eventually be stored as directory attributes. The Obj-Admins pseudo-attribute specifies the names of accounts that have administrator permissions on the object. The Obj-Users pseudo-attribute specifies the names of Windows NT user accounts that have user permissions on the object. For more information, see Using Directory Access Pseudo-Attributes.