Cluster Server relies on the availability of a network path to ensure that the nodes of a cluster can communicate. If one network fails, another network must be able to take its place. Therefore, maintaining accurate information about network topology is critical.
Cluster Server maintains configuration information about network topology not only to store data about all of the networks that are available to the cluster, but also to keep track of the particular network or networks that are currently being used and to properly configure IP Address resources.
Cluster Server views networks as serving one of the following roles:
Internal cluster communication implies cluster control messages. IP Address resources are created on networks that provide clients with access to cluster services.
Cluster Server authenticates all internal communication, but those sites that are particularly concerned about security may wish to restrict internal communication to physically secure networks.
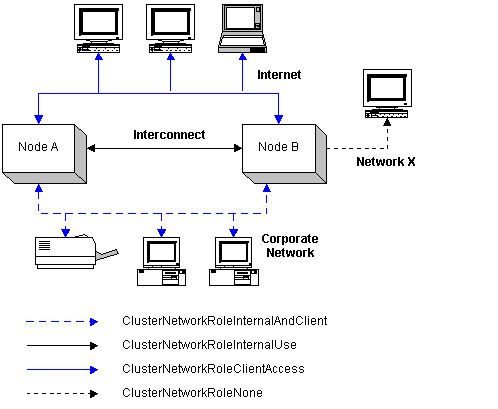
The following diagram provides an example of these four roles. The key below the diagram lists the values that are stored in a network's Role property. The private network, or Interconnect, is used only for internal communication between the cluster nodes. The Internet, due to its widespread usage, is only used to connect client systems to the cluster. The Corporate network is used for both client connections and internal communication. Network X represents a network that, for whatever reason, cannot be used by the cluster.

Typically, Cluster Server attaches to every available network, storing property information for each in the cluster database. However, an administrator can prevent the Cluster Service from attaching to a network by assigning the value ClusterNetworkRoleNone to its Role property. Only the first three roles identify a network as one that should be utilized by the Cluster Service.
Networks used by the Cluster Service expose their behavior through Cluster API functions. One of the functions, ClusterNetworkControl, is used to initiate a variety of operations. The operations are defined by a set of control codes. Several of the operations involve accessing network data stored in the cluster database.