
Contents
Index
Topic Contents
Previous Topic: Glossary
Next Topic: Packaging ActiveX Controls
 | ||
| ||
| ||
Appendix A: Required Files
To use Authenticode, a set of client files, publishing tools, and a signing DLL are required.
Client files are installed in the \WinNT\System32 directory on Microsoft(r) Windows NT(r), or in the \Windows\System directory on Microsoft Windows(r) 95, and include the following:
- Wintrust.dll
- Softpub.dll
- Mssip32.dll
- Vsrevoke.dll
- Crypt32.dll
Publishing tools and the signing DLL are installed in the \INetSDK\Bin directory and include the following:
- MakeCert.exe (creates an X.509 certificate for testing purposes only)
- Cert2SPC.exe (creates an SPC for testing purposes only)
- SignCode.exe (signs and timestamps a file)
- ChkTrust.exe (checks the validity of the file)
- MakeCTL.exe (creates a certificate trust list)
- CertMgr.exe (manages certificates, CTLs, and CRLs)
- SetReg.exe (sets registry keys controlling certificate verification)
- Signer.dll (performs signing)
Appendix B: The X.509 Certificate
The X.509 protocols include a structure for public-key certificates. A CA assigns a unique name to each user and issues a signed certificate containing this name and the user's public key. The following diagram shows an X.509 certificate.
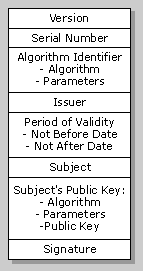
These are the meanings for each field.
Field Meaning Version Identifies the certificate format. Serial Number A value unique to the CA. Algorithm Identifier Identifies the algorithm used to sign the certificate, together with any necessary parameters. Issuer The name of the CA. Period of Validity A pair of dates. The certificate is valid during the time period between the two. Subject The name of the user. Subject's Public Key Contains the public key algorithm name, any necessary parameters, and the public key. Signature The CA's signature. Appendix C: Suggested Reading
The topic of digital signing is discussed more fully in the following documents.
CCITT, Recommendation X.509, The Directory-Authentication Framework, Consultation Committee, International Telephone and Telegraph, International Telecommunications Union, Geneva, 1989.
Microsoft Cryptographic Service Provider Programmer's Guide, Microsoft, 1995.
Microsoft Application Programmer's Guide, Microsoft, 1995
RSA Laboratories, PKCS #7: Cryptographic Message Syntax Standard. Version 1.5, November, 1993.
Schneier, Bruce, Applied Cryptography, 2d ed. New York: John Wiley & Sons, 1996.
http://www.microsoft.com/security
Top of Page
© 1997 Microsoft Corporation. All rights reserved. Terms of Use.