Coopers & Lybrand, L.L.P., Information Technology Security Services
April 1997
This case study presents the results of tests designed to evaluate Microsoft® Proxy Server security. Interconnectivity security issues and the Microsoft Proxy Server features designed to address these issues are presented. The approach used to evaluate Microsoft Proxy Server security is discussed, and definitions of multiple test cases covering Microsoft Proxy Server installation, configuration, function, and penetration are provided. The configuration of the testing laboratory and its equipment used to evaluate this product is described, and a security checklist and baseline security configuration is presented.
What Is Microsoft Proxy Server?
Interconnectivity Security Issues and Microsoft Proxy Server Security Features
Installation Test Case Results Summary
Configuration Test Case Results Summary
Function Test Case Results Summary
Penetration Test Case Results Summary
Appendix B—Test Lab Network Diagrams
Appendix C—Server Security Checklist
Appendix D—Output of ISS SafeSuite Scans (Abbreviated)
Appendix E—Suggested Baseline Security Configuration
Appendix F1—Detailed Installation Test Case Results
Appendix F2—Detailed Configuration Test Case Results
Appendix F3—Detailed Functional Test Case Results
Appendix F4—Detailed Penetration Test Case Results
Report of Independent Accountants
In the fast-growing market for Internet related products and services, new offerings are made available on an increasingly frequent basis, often without extensive field use or review. This document represents an attempt to provide an additional level of evaluation of Microsoft Proxy Server and presents the results of a series of tests designed to evaluate the product’s security capabilities. The exercises conducted provide information regarding the security functionality of the product and should be used in conjunction with vendor literature, along with your own critical evaluation, to determine its effectiveness and appropriateness for your environment. This document is one of several sources that can be referenced when attempting to make decisions regarding the relative strength of security measures your organization would like to implement when establishing Internet connectivity.
It is critical to note that there is no one right answer to the question of what constitutes enough security. The answer is often a custom solution that depends on your needs for control and flexibility. Adopting a practical business approach when addressing the level of security an organization requires should be fundamental to all security decisions.
Based on our analysis, it appears that Microsoft Proxy Server can be used to satisfy the security needs of many organizations as they establish and maintain Internet-based systems and applications.
In our assessment of Microsoft Proxy Server, we completed a four-phase evaluation program:
Coopers & Lybrand’s (C&L) intent in constructing this four-phase approach was to emulate, as closely as possible, the life cycle of product deployment in commercial environments. The approach was designed to unearth security vulnerabilities that would have a major impact on the overall security of private networks. C&L employed generally recognized techniques for testing security controls in networked environments of this kind.
Throughout the evaluation, Microsoft Proxy Server withstood the testing of well known and well documented tools, such as the public domain tools Internet Security Scanner and Satan, that exploit vulnerabilities in TCP/IP networks. In addition, Microsoft Proxy Server did not reveal any easily exploitable vulnerabilities that would place private networks at significant risk when communicating via the Internet.
Obtaining an in-depth understanding of the contents of this document requires a fundamental understanding of internetworking architecture, the TCP/IP protocol, and general security vulnerabilities in Internet technology. It should be noted that without careful installation, monitoring, and observation, any computing product or system may be vulnerable to exploitation in current and future configurations. Please see the Bibliography later in this document for additional information regarding these issues.
One must note Microsoft Proxy Server relies on Microsoft Windows NT® Server version 4.0 as its operating system and for certain security features. In some scenarios and configurations, the IP forwarding feature of the Microsoft Windows NT Server version 4.0 operating system may present routing vulnerabilities. This feature is not enabled when Microsoft Windows NT Server version 4.0 is installed, but since this feature is not automatically disabled when Microsoft Proxy Server is installed, it is important to disable it. In addition, Microsoft Windows NT Server version 4.0’s TCP/IP allows initial connections to some IP ports, which can be detected via the Internet. This may entice vandals to attempt further attack scenarios and encourage organizations interested in the highest level of security to employ additional firewall components (such as a packet filtering router or other commercial firewall product) between the proxy server and the public Internet. This paper explains how proper configuration can help you avoid these risks. Finally, since a major component of security depends on good monitoring, all organizations that utilize the Microsoft Proxy Server, which does include an adequate auditing mechanism but no automatic alert mechanism, should make the commitment to allocate proper personnel resources for continuous system monitoring.
In summary, it appears that Microsoft Proxy Server, when properly installed, configured, maintained, and monitored, can provide a reasonable and practical level of security for a wide variety of computing environments.
Recent technical developments provide fast efficient communication among individuals and businesses. Currently, one of the most publicized forms of modern communication is the computer network, specifically the Internet. As this communication technology becomes increasingly a necessity, the concern for its security and control also increases. Resulting from this concern, organizations have developed additional technology to counter these control and security issues.
Microsoft Proxy Server is one such technology created to address the security and control of communications conducted through a computer network.
The primary objectives of this white paper are to:
While this document addresses the security controls of the Microsoft Proxy Server, it does not address all of the security controls of the Microsoft Windows NT Server version 4.0 operating system or the Microsoft Internet Information Server products, both of which are prerequisites for the Microsoft Proxy Server operation. This evaluation is not intended to be a conclusive examination of Microsoft Windows NT Server version 4.0 or IIS.
Microsoft Proxy Server is a secure, high performance, cost-effective gateway to the Internet. Microsoft Proxy Server has two services: Web Proxy and WinSock Proxy.
Web Proxy is fully compliant with the CERN proxy standard, and offers proxy service for FTP Read, Gopher, and WWW for computers on your private network running TCP/IP. Web Proxy supports the popular web browsers, including Microsoft Internet Explorer 3.0, Netscape Navigator 3.0, and PointCast Network. Web Proxy also supports multiple platforms including Windows NT Server, Windows NT Workstation, Windows® 95, Windows for Workgroups, Windows 3.1, UNIX, and Macintosh®. Web Proxy also supports SSL Tunneling, which provides an encrypted connection between the client and Web Server through the proxy.
WinSock Proxy proxies virtually all Windows Sockets 1.1 compatible applications and protocols by intercepting Windows Sockets Application Programming Interface (API) network calls, with support for TCP/IP and IPX/SPX net protocols. This service is transparent to the application, therefore virtually all applications can be proxied. Examples of remote capable applications are TELNET, FTP, RealAudio, SMTP, and VDOLive.
Microsoft Proxy Server offers an extensive array of supporting features.
Feature Summary
| Feature | Description |
| Single IP Address | Microsoft Proxy Server presents one IP address to computers on the Internet. This enables one point of connection between many internal computers and external computers. The internal network addresses are not presented to the external computers. |
| Supports Dual-Homed Adapters | Microsoft Proxy Server supports two network adapter cards with different addresses that do not use IP-Forwarding. This feature separates the internal addresses topology from the external. |
| Local Address Table | Microsoft Proxy Server enables the specification of the IP address range(s) of all internal computers when IP is used as one of the internal protocols. This enables local clients to determine whether they must connect through the Proxy Server to access an external IP address. This feature also blocks processing of external client requests to internal servers. |
| Internet/Intranet Applicable | The single IP address, support for two network adapter cards, and Local Address Table make Microsoft Proxy Server suitable for securing internal networks from the Internet or from other internal networks. |
| Site Filtering | Microsoft Proxy Server enables certain Internet sites to be filtered from internal clients. |
| Access Control | Microsoft Proxy Server enables user and group permission lists to be established for each protocol. |
| Proxy Request Logging | Microsoft Proxy Server enables logging of system usage and access. Logs can be saved to text files or to a database (such as SQL Server™) using ODBC. |
| Remote Administration | Microsoft Proxy Server can be administered from remote intranet (within corporate network) locations using the Internet Service Manager tool. |
| Tight Integration with Windows NT Server Version 4.0 | Microsoft Proxy Server tightly integrates with Microsoft Internet Information Server and the Windows NT Server Version 4.0 network operating system, therefore allowing central administration through the Windows NT administrative environment and single logon for Proxy Server users. |
| Multiple Network Compatible | Microsoft Proxy Server supports both TCP/IP and IPX/SPX protocols and it can be used with existing networks, therefore allowing migration to a pure TCP/IP based network at a self-defined pace. |
| Ease of Use | Microsoft Proxy Server runs on the Windows NT Server Version 4.0 network operating system and presents a user-friendly interface. |
| Demand Dial | Microsoft Proxy Server contains an autodial feature, which automatically connects the Proxy Server to the Internet Service Provider whenever data is required and not stored in the cache. The autodial disconnects from the service provider when the data is retrieved or when a time out expires. |
| Protocol Support | Microsoft Proxy Server supports all Internet protocols, including streaming audio and video, Internet Relay Chat, TELNET, HTTP, FTP, SMTP, NTP, and more. |
| Caching | Microsoft Proxy Server offers active, intelligent caching of frequently visited sites to reduce network costs and bandwidth consumption. Caching is scaleable through Windows NT and hardware. |
| Integration With SNMP | Microsoft Proxy Server integrates with SNMP services, which enables the status of a Proxy Server to be viewed from across the network. |
| Extensibility | Microsoft Proxy Server supports the multi-vendor ISAPI Filter specification enabling third parties to write value-enhancing add-ons to the Proxy Server. Examples of current extensions include virus scanning and site filtering. |
Organizations or individuals that connect to the Internet assume significant security risk. Microsoft Proxy Server and Windows NT Server Version 4.0 have features designed to prevent and/or severely reduce most of the common security issues that are introduced by connecting to the Internet. The following section focuses on those features and the issues and risks eliminated, severely reduced, or generally mitigated by each of those features.
Network Penetration—The most widely discussed set of risks relating to a corporate network is outside users accessing internal resources. This includes external users accessing data on the internal network as well as potentially doing damage to the network itself. As more companies connect to external networks, a variety of tools, including proxy servers, have been developed for the purpose of masking the internal network from the Internet or other external networks in order to prevent snooping on or hacking into the internal network.
Local Address Table (LAT) and Proxy Server—In the network configuration (LAT) dialog box, each address pair in the Internal IP Addresses list identifies a range of addresses that belong to the private network. This information is used to create the Local Address Table (LAT). The LAT is stored in the msplat.txt file, located by default at C:\msp\clients. When a client computer runs the client Setup program, this table is downloaded from the Server to the client. When a WinSock Proxy or Web Proxy client attempts to access a network IP address, the LAT is used to determine whether the address is inside the private network (and can be connected to directly) or is outside on the Internet (and therefore must be connected to through Microsoft Proxy Server).
When a client request is received, it is verified that it came from an internal network interface.
Supports dual-homed environment—The Microsoft Proxy Server can easily be configured as a dual-homed (separate network interface for each side) non-routing (not arbitrarily passing IP packets between connected networks) security device. This method of connection provides the most secure form of network security isolation. This dual-homed environment can be configured to support a different network protocol on the two interfaces, thus providing another security level.
Ability to Disable IP Forwarding in Windows NT Server Version 4.0 TCP/IP—In a dual-homed server, IP forwarding is enabled or disabled under the routing tab of the TCP/IP properties menu. This is found by selecting TCP/IP under the protocol tab of the network icon. The network icon may be accessed through the Control Panel.
Support for IPX protocol—Since many corporate networks do not run the TCP/IP protocol, but support the IPX protocol, the Microsoft Proxy Server will function in that network environment. The Proxy Server will operate in a dual-homed network with the internal network running IPX and the external network running TCP/IP. Some system administrators believe this provides better security on the private network. The IPX protocol is configured in Windows NT server using the network icon’s protocols tab. Once configured, Microsoft Proxy Server will automatically utilize the protocol.
IP Spoofing—IP spoofing or masquerading is a technique used in a network or system attack in which the attacking computer assumes the identity of a computer already in the internal network. The attacking computer spoofs or imitates the IP address of the internal computer to either send data as if they were on the internal network or to receive data intended for the machine being spoofed.
Local Address Table (LAT) and Web Proxy—The Microsoft Proxy Server is designed to prevent any IP packets with destination addresses not found in the LAT from entering through the public Internet-connected interface and attempting to access computers on the internal network. This feature plays a major role in preventing spoofing (IP address masquerading) attacks from the Internet.
External Publication of Internal Data—Prevention of internal data, used on an internal network or an Intranet, from being visible on any external network.
Enable/Disable Internet Web Publishing—The Internet Information Server (IIS) may be installed when Windows NT Server Version 4.0 is installed. All three IIS publishing services (WWW, Gopher, and FTP) are started by default when the Windows NT Server is started. These services, when configured, are then advertised both on the internal and on the external network. When the Microsoft Proxy Server is installed, WWW publishing (http protocol, port 80) on the external network is disabled, effectively hiding the internal http data from the outside. This feature may be manually enabled by selecting the check box to allow outside access to the inside data.
Access to Unauthorized or Undesirable Internet Sites—Internet browser software will allow access to any site on the Internet. Many corporate entities find that certain sites are unacceptable in their content or will want to limit access to only business-related sites. These organizations prefer to restrict access not only by written policy, but also by enforcing an actual restriction to those sites that they deem unacceptable. Lack of site access restrictions and a policy regarding site access may be interpreted to mean that access to all sites is acceptable. Appropriate use and legal liability are risks associated with internal users accessing outside resources. This risk can be mitigated through controls such as filtering for certain sites identified as inappropriate, issuance of a policy regarding site access, and monitoring site access.
Site/Domain Filtering—The Microsoft Proxy Server gives an administrator the capability to limit which Internet sites can be accessed by the internal client user population. This feature can be configured to grant or deny access to all sites except those listed in the proxy filtering database. Filtering can be assigned by providing specific, individual network addresses, network address ranges and subnet masks, or Internet domain names. This feature may be used to limit a corporation’s exposure to non-authorized Internet access.
This feature is disabled by default and must be enabled to use. Access may be controlled on a granted or denied list. All access is granted except to sites listed or all access is denied except to sites listed. The system administrator may override filtering by using the Unlimited protocol of the WinSock Proxy.
Auditablility—The ability to gather information about the use of the Microsoft Proxy Server is important to overall system security—the administrator’s knowledge of what users are accessing and what information is being moved over the network helps avoid problems. Without such information, the network administrator knows nothing about the activity on the proxy server, neither the types of access nor the locations visited.
Weak or nonexistent monitoring controls increases the risk associated with not interrupting or noticing any attacks on your network or servers.
Logging—The Microsoft Proxy Server enables administrators to activate one of two levels of activity/security logging functionality (regular or verbose). With each level of logging a trade-off takes place between amount of detail available versus performance and storage requirements. The regular level of logging provides sufficient information to gain a comfortable level of security monitoring for most network applications, while the verbose level provides all of the information regarding a connection or event.
Logging provides the system administrator the ability to track system usage and access. Without logging the ability to prevent unauthorized activity is severely limited. Operating the Microsoft Proxy Server without logging enabled should be considered insecure.
The logging feature records the following information and stores it in the listed directories:
Web proxy: %SYSTEMROOT%\w3plogs
Winsock proxy: %SYSTEMROOT%\wsplogs
Unauthorized Users—Most corporations desire to control access to the Internet. Authentication of users connecting to this medium will provide some comfort level that the appropriate persons are using the access facility. Poor or no authentication may lead to a loss of accountability in the use of the private and public network.
User-Level Authentication—This feature is implemented and operates differently within the Web Proxy Server and the WinSock Proxy Servers.
Use of an anonymous logon, between client and proxy server, is the most common access method to the Internet. Use of this method assumes that the connection is coming through the internal network and is essentially trusted. There is no security involved with this connection, other than assuring that the client is on the internal network. Microsoft Proxy Server offers two kinds of user-level authentication.
Using either of the authenticated connection processes enhances security by forcing the proxy server to authenticate each connection before allowing the request to pass through the proxy. The user has to be revalidated for each connection through the proxy server. This requires some level of account management either on the proxy server itself or on the domain controller for the domain that contains the proxy server machine or on a domain controller in a trusted domain, as each user must have a valid account on the proxy server.
Authentication between a private network client and the Web Proxy Server is configured in the WWW Service tab of the Internet Information Server (IIS) and in the Web Proxy Permissions tab of the Proxy Server. In addition to anonymous authentication, the Proxy Server allows two other authentication methods—Basic Authentication with Clear Text and Windows NT Challenge/Response Authentication.
The Web Proxy Server allows access control to be enabled or disabled. If disabled, all users get access to the Web Proxy and the settings in the WWW Service tab are not used. If enabled, then user-level authentication takes place based on the settings in the WWW Service. When access control is enabled, using the anonymous login feature will not work, unless the IUSR_machinename account is given protocol permission on the Web Proxy’s Permissions tab. If anonymous login is the only authentication choice selected in the WWW service of IIS, then no access control at the Web Proxy is active. If any other authentication method is chosen in the WWW service of IIS, then access control is available in the Web Proxy.
With Basic authentication enabled, a username and password are passed to the Microsoft Proxy Server in the uuencoded format. Uuencoding means that the text is scrambled, but normal ASCII characters are visible, so the username Murray might come out as Nvttbz. To the casual viewer this may seem unusable, but encoded text is easily unscrambled by certain programs.
Windows NT Challenge/Response (NTCR) authentication is Windows NT’s highest level of security. NTCR is typically run in a networked environment that includes Windows NT servers and Windows NT workstations. Windows 95 workstations can also use NTCR to provide secure client authentication. Windows for Workgroups and Windows 3.1 cannot utilize this method by default, but may be upgraded to do so.
Using NTCR authentication is one of many requirements to be met if you want your network to be C2 compliant. NTCR requires that you run an NTCR-compatible application such as Internet Explorer 3.0 with the Web Proxy.
The WinSock Proxy provides access control similar to that of the Web Proxy. When access control is enabled, the WinSock Proxy authenticates all users with the Windows NT Challenge/Response method. When access control is disabled, the WinSock Proxy allows anonymous access.
In the WinSock Proxy, if access control is disabled, then all users have access. This is the equivalent of disabling access control in the Web Proxy. If access control is enabled, then only those granted permission to the specific protocols may access the Proxy Server.
Unauthorized Access to Services—Administrators and managers may wish to limit user access to specific Internet protocols and specific network ports. These limitations may vary based on individual user profiles or group membership.
The Microsoft Proxy Server has the capability of securing both out-bound and in-bound Internet access down to specific individuals or groups of individuals for the specific protocols. This can be enforced using the Proxy Server’s Properties and Permissions function for either WinSock Proxy or Web Proxy. This makes it possible to limit particular proxy services to as fine a degree as an organization feels is appropriate.
User Level: Access Control—This feature is controlled in the Permissions Property Sheet for both the Web Proxy and the WinSock Proxy. Individual users or groups of users may be granted permissions to use any individual protocol within the Proxy Server. Users who are not explicitly given access to a protocol are not permitted to access that protocol.
Global Level: Disable Port/Protocol—The WinSock Proxy permits an entire protocol to be disabled from access. Protocols not listed in the Protocol Description Property Sheet are automatically disabled from any access. Protocols listed in the property sheet are available unless the individual ports listed within the protocol are disabled. Protocols may disabled by denying user access to them or by removing their definition from the WinSock Proxy’s protocols tab.
The WinSock Proxy provides an additional protocol known as Unlimited. This protocol provides those granted access with unlimited access to all protocols defined for the WinSock Proxy. Unlimited access also provides an override to any filters that may be in place.
Visibility of Internal Network Addresses to the Internet—Providing transparent access from an internal or private network to the public or external network while masking or protecting the internal network.
Proxy Architecture—The Proxy Server provides IP address aggregation. This means that for every client request it receives, the Proxy Server issues that request to the external network using its external IP address, thus concealing the internal network addresses from the outside. When services are proxied by the Microsoft Proxy Server, the source IP address of each service request is re-mapped to that of the Proxy Server external network adapter. This ensures that the external services and/or any unauthorized party cannot determine the internal network addresses of client stations and later attempt to penetrate those stations through some other open access point (for example, a non-authenticating terminal server or a passive routing device that may be open).
Unauthorized Access to Cached Data—Data from the World Wide Web, such as sites visited and information viewed, is sometimes stored for faster access by other users. These data could contain sensitive information and need to be protected from inadvertent or unauthorized viewing.
The Microsoft Proxy Server provides caching for http resources accessed on the Internet from internal network computers. The Proxy Server cache is checked prior to all Internet data requests to see if the requested data resides in the cache.
SSL Not Cached—A security feature of this caching is that no http pages are ever cached. This prevents one user from inadvertently viewing data that was issued to another user while in a secure mode.
NTFS Support—The Windows NT File System (NTFS) provides security and access control for your data files. By using NTFS, you can limit access to portions of your file system for specific users and services. This will help block access to cached data, as individual users need no access to the cache directory.
User Authentication Resources Not Cached—Any authenticated resources are not stored in cache at any time. This prevents any access to user account and password information. This feature is enabled by default.
System Detection and Probing—Certain TCP/IP network protocol ports, if active, may be used by hackers to gather information about a network or as a possible penetration point to a network. Information is gathered about listening network ports through the use of the freely available network scanning tools.
Disabling of Specific Network Ports—The Windows NT Server that hosts the Microsoft Proxy Server implementation listens for network connections on various ports depending on which services are active in the Web Proxy and the WinSock Proxy. Certain other ports such as 47, 135, 137, 138, and 139, are active and may be disabled through the Windows NT Server’s registry and by changing the bindings on the network interface card. Bindings are modified under the Bindings tab of the network icon. This icon is available through the control panel. More information on how to disable these ports is found in the Appendices of this document.
Denial of Service Attacks—The “Denial of Service Attack” uses automated tools to flood the port(s) of the system providing access to the network with requests for connection, which will be denied. Flooding the entry ports exploits the fact that a single point of control can also be a single point of failure. These attacks cause a server to become so occupied with the attack that it either crashes or only responds to the attack scenario preventing any legitimate uses of the server.
Many features of the UNIX operating system that could be used in denial of service attacks are functions that are not available in a standard Windows NT Server installation. These features include server services for finger, rexec, rlogin, and so on. In addition, telnet attempts to an open port produced a successful packet acknowledgment preventing the “SYN” attack.
Data Privacy—Ensuring that data transmitted between the Proxy Server and the clients is secure and unreadable.
SSL Tunneling—The tunneling of the Secure Sockets Layer (SSL) protocol is enabled by default within the Proxy Server when a user is granted access to the Web Proxy. This feature provides for an SSL session between the server and the client computer. This is supported in a browser like Internet Explorer 3.0.
For information on securing Microsoft Proxy Server, refer to Appendix C—Microsoft Proxy Server Security Checklist and Appendix E—Suggested Baseline Security Configuration.
C&L evaluated Microsoft Proxy Server by creating a test environment, developing an objective test case approach, executing the test cases, and interpreting test case results.
The most significant component of the approach is the test cases, which focus on four test areas: Installation, Configuration, Function, and Penetration. Each test area contains tests designed to satisfy test area objectives. This section describes the test areas and objectives.
A total of 15 test cases were run, in the four areas described below, during the testing of the Microsoft Proxy Server. These test cases show that Microsoft Proxy Server can be easily configured to a maximum level of security; however, creating the most secure Microsoft Proxy Server configuration requires thought and planning, as with any product installation. In addition, the penetration test cases using standard tools showed no vulnerabilities, but some unexpected TCP/IP ports were visible and would need to be disabled.
In summary, the results of the following test cases show that the Microsoft Proxy Server can provide a reasonable and practical level of security for a wide variety of installations.
The objective of the installation test is to identify any security-related installation options, and evaluate the security implications of the installation options and overall installation procedure.
The objective of the configuration test area is to identify any security-related configuration options, and to evaluate security when Microsoft Proxy Server is configured with default, minimum, or maximum security settings.
The objective of the function test area is to evaluate Microsoft Proxy Server’s ability to provide proxy services and disallow traffic when certain security features are activated, and evaluate the logging functionality.
The objective of the penetration test area is to evaluate Microsoft Proxy Server’s external vulnerabilities. The penetration tests were designed to use a combination of standard Internet tools that determine vulnerabilities of common Internet-connected servers, in addition to special C&L methods and tools designed to exploit specific Internet vulnerabilities and Microsoft Proxy Server specific vulnerabilities (based on our understanding of how it was designed).
Appendix D—Output of ISS Safesuite Scans contains the actual output from one of the automated tools used during these tests.
The Interconnectivity Security Issues and Microsoft Proxy Server Security Features section of this document provides additional information along with the implications of the issues addressed in the Test Case Results sections.
Assess security implications of Microsoft Proxy Server installation procedure and installation options.
The Microsoft Proxy Server installation procedure did not appear to reveal any serious security issues.
Issue
Careful configuration of the LAT is necessary for maximum security.
Description
The LAT is configured in the Local Address Table (“LAT”) Configuration window. This option requires basic knowledge of the internal network’s addresses. It is important to configure the LAT correctly because an address range greater than the internal network’s is unnecessary for Microsoft Proxy Server functionality and could produce security openings in the Proxy Server. Refer to the Interconnectivity Security Issues and Microsoft Proxy Server Security Features section of this document for additional information and the implications of this feature.
How Microsoft Proxy Server addresses this issue
The LAT can be constructed automatically using the addresses of the Proxy Server’s routing table or the standard private address ranges. This is accessible through the Construct Local Address Table window. Refer to Appendix E—Baseline Security Configuration for the recommended baseline implementation of this feature.
Issue
Accessibility of cached data to users on the internal network.
Description
Microsoft Proxy Server provides caching for HTTP resources accessed on the Internet from internal client stations. The Proxy Server cache is checked prior to all Internet data requests. Cached data is stored on disk. Certain users have access to the disk where the cache resides.
How Microsoft Proxy Server addresses this issue
A security feature of this caching is that HTTP-S pages and user-authenticated objects are not cached. This prevents one user from inadvertently viewing data that was issued to another user while in a secure mode. In addition, the cached data should be stored on a Windows NT NTFS partition, which will utilize Windows NT file security.
Identify and assess Microsoft Proxy Server default security configuration and assess security implications.
Issue
Internet Information Server Services may be running.
Description
One should also note that Internet Information Server (IIS) is installed when Windows NT Server Version 4.0 is installed. All IIS services (WWW, Gopher, and FTP) are started by default.
How Microsoft Proxy Server addresses this issue
The WWW IIS services are configured to prevent publishing to the Internet. For maximum security, the FTP and Gopher IIS services should be stopped. The Microsoft-provided Appendix C—Server Security Checklist discusses services.
Assess Microsoft Proxy Server configuration options security when set to a minimal (as close to none as possible) level of security.
Microsoft Proxy Server can be configured to a minimal level of security. Although not recommended, this level of security may be adequate for certain environments.
Issue
Microsoft Proxy Server can easily be configured to a minimal level of security.
Description
A minimal level of configurable security may include user-level access control disabled, logging disabled, and Internet Web publishing enabled. As noted in Test Case PROX-C-1, Microsoft Proxy Server does not configure to this minimal level of security by default. The administrator must configure Microsoft Proxy Server to these settings.
How Microsoft Proxy Server addresses this issue
The minimally secure configuration can easily be avoided through proper planning and completely understanding the features. The Microsoft provided Appendix C—Server Security Checklist and Appendix E—Baseline Security Configuration along with hard copy documentation and on-line help descriptions of the security features, are tools that can be used to plan and understand the features. The converse to this scenario is presented in Test Case PROX-C-3.
Assess Microsoft Proxy Server configuration options security when set to a maximum level of security.
Issue
Microsoft Proxy Server can be easily configured to a maximum level of security; however creating the most secure Microsoft Proxy Server configuration requires thought and planning.
Description
A maximum level of configurable security may include access control, verbose logging to files that are automatically created and saved on a daily basis, and Internet Web publishing disabled. As noted in Test Case PROX-C-1, Microsoft Proxy Server does not configure to this maximum level of security by default. The administrator must configure access control and logging.
How Microsoft Proxy Server addresses this issue
The Administrator must select the correct level of access without denying needed services. The maximum secure configuration can be accomplished through proper planning and completely understanding the features. The Microsoft-provided Appendix C—Server Security Checklist and Appendix E—Baseline Security Configuration along with hard copy documentation and on-line help descriptions of the security features, are tools that can be used to plan and understand the features. The converse to this scenario is presented in Test Case PROX-C-2.
Issue
It is possible to configure Microsoft Proxy Server to forward IP traffic between its two network interface cards.
Description
The IP Forwarding function becomes active when the IP Forwarding checkbox is selected before or after the Microsoft Proxy Server installation. When Microsoft Proxy Server is installed, there is no warning indicating IP Forwarding is active. Risk is incurred for administrators who may select IP Forwarding with Microsoft Proxy Server installed without understanding the consequences.
How Microsoft Proxy Server addresses this issue
This issue can be addressed procedurally. The administrator must be attentive to the status of the IP Forwarding checkbox.
Determine the security impact of configuring the internal (private) network for addresses that are being used on the external (public) network. This is the basis for a spoofing attack if Microsoft Proxy Server does not respond properly in such a configuration.
Test the level of access between internal and external networks when the internal client does not have Microsoft Proxy Server client software installed or if both the external and internal machines run a non-Microsoft Proxy Server–supported operating system.
Microsoft Proxy Server successfully prevented non-proxy clients from using services beyond the Proxy Server.
Test the functionality of Microsoft Proxy Server’s logging mechanism.
Issue
Configuration of the logging feature.
Description
The logging processes gather a significant amount of information about any connected process. This makes the logging facility a valuable tool for tracking system usage and monitoring individual user activity. Without logging, the ability of the system administrator to track the system usage and to prevent unauthorized activity is severely limited. Operating the Microsoft Proxy Server without logging should be considered insecure.
How Microsoft Proxy Server addresses this issue
As indicated in Test Case PROX-C-1, regular logging to a new file on a daily basis is selected by default. This configuration may be adequate for certain environments. Test Case PROX-C-3 and Appendix E—Baseline Security Configuration provide information on the recommended settings for the logging feature.
To determine which IP addresses respond to an ICMP echo (ping) request on the various sub-nets where the Microsoft Proxy Server is attached. The primary objective is to determine which IP addresses answer to untrusted systems connected to the external network.
Issue
The internal adapter of machine PROXY-1 (the dual-homed Proxy Server) unexpectedly answered the echo request from an external system.
Description
When an echo request is sent to a Microsoft Proxy Server with a destination address of the internal network adapter, the internal adapter will respond. If the response of the internal adapter address is detected by an outside entity, it could aid in designing a more focused attack on the internal network. Although designing a more focused attack may not be directly possible through the Microsoft Proxy Server, the information could be used if another entry point was also identified (i.e., a non-secured dial-in SLIP or PPP line), and later used to penetrate the network.
How Microsoft Proxy Server addresses this issue
Microsoft Proxy Server does not currently address this issue. However, Microsoft Proxy Server prevents visibility and access to the other systems connected to that adapter’s internal network.
To determine which TCP/IP ports a Windows NT Server will answer to when running the Microsoft Proxy Server using the default configuration options.
Issue
The strobe utility detected seven TCP ports answering to external network connections. Three of these were expected: FTP, HTTP, and Gopher. Four of these were unexpected: NI FTP (port 47), Location Server (port 135), NetBIOS (port 139), and Port 1028.
Description
Each of the TCP/IP service ports identified by “Strobe” represents a possible avenue of external attack by other TCP/IP service-specific penetration tools and techniques. In the penetration test cases that follow this test, each of the significant responding ports are further tested for security vulnerabilities.
How Microsoft Proxy Server addresses this issue
This issue can be addressed procedurally. Many of the identified ports can be disabled. The Microsoft-provided Appendix C—Server Security Checklist provides guidance on disabling ports 47, 139, and 1028 on the external adapter of a Windows NT Server running Microsoft Proxy Server. FTP port 21 and gopher port 70 can be disabled using the Internet Information Server management tool. Port 135 cannot currently be disabled. The RPC service will unconditionally listen on port 135 on all interfaces, and relies on Windows NT RPC authentication for security; however, our testing did not show any vulnerability related specifically to this issue.
To determine if the Microsoft Proxy Server is susceptible to any of the common Internet weaknesses identified by the Internet Security Scanner (ISS) public domain security analyzer/tool.
The ISS utility will analyze all target systems for the following Internet risks and/or vulnerabilities:
To determine if the Microsoft Proxy Server is susceptible to any of the common Internet weaknesses identified by the Satan public domain security analyzer/tool.
The Satan utility will analyze all target systems for the following additional (over ISS) Internet risks and/or vulnerabilities:
Issue
The only issue reported by the Satan utility was its ability to identify that the Proxy Server was offering an Anonymous FTP service.
Description
The Anonymous FTP service is an optional part of the Windows NT Server that was configured by default prior to the installation of the Proxy Server. The FTP service is installed as part of the Internet Information Server. The presence of Anonymous FTP service represents a possible avenue of external attack if misconfigured. Test Case PROX-P-5 tests this for security vulnerabilities within the FTP service.
How Microsoft Proxy Server addresses this issue
This issue can be addressed procedurally. FTP port 21 can be disabled using the Internet Information Server management tool.
To attempt manual anonymous FTP penetration attempts.
Issue
The FTP Server allowed the external system to gain a successful anonymous login.
Description
The Anonymous FTP service is an optional part of the Windows NT Server that was configured by default prior to the installation of the Proxy Server. The FTP service is installed as part of the Internet Information Server. The presence of Anonymous FTP service represents a possible avenue of external attack.
How Microsoft Proxy Server addresses this issue
The coexistence of a properly configured (which is the default) FTP server in the same system with the Microsoft Proxy Server does not appear to present any additional vulnerabilities to the proxy service, Windows NT operating system, or the internal network behind the server. The FTP server allowed the external system to gain a successful anonymous login. The default-configured FTP server could not be compromised through standard manual penetration techniques as listed in this test case. In addition, if not required, FTP port 21 can be disabled.
To attempt to exploit the fact that the Microsoft Proxy Server allows connections to the unused TCP/IP port 47 (as a previous run of strobe detected). C&L focused on this port because it is the only additional port that started accepting TCP/IP connection requests after the Proxy Server was installed and is identified by Microsoft as a port that can be used to administrate the Proxy Server.
Issue
Microsoft Proxy Server allows connections to port 47.
Description
The ability to connect to port 47 represents a possible avenue of external attack by more service-specific penetration tools and techniques.
How Microsoft Proxy Server addresses this issue
This issue can be addressed procedurally. Port 47 can be disabled. The Microsoft-provided Appendix C—Server Security Checklist provides guidance on disabling port 47 on the external adapter of a Windows NT server running Microsoft Proxy Server. In addition, there seem to be no security implications in Microsoft Proxy Server’s allowing connections to port 47. A denial of service attack does not appear to be effective against this open port.
Note The above two tests do not apply to any of the services offered by or answered to by Microsoft Proxy Server. Therefore, their exclusion should have no impact on the overall test results.
Issue
The only issue raised by the ISS tool was that the Proxy Server allowed trace routing packets to be passed between its two network interfaces.
Description
Trace routing is when a router allows packet routing information to be echoed through to both attached networks. This information can be helpful to attackers in determining internal network addressing schemes when looking to exploit weaknesses on other systems connected to the internal network. This issue was also identified in Test Case PROX-P-1 when the Proxy Server allowed its internal network adapter to respond to a general echo (ping) request. This issue was noted because the Proxy Server’s internal network adapter answered.
How Microsoft Proxy Server addresses this issue
Microsoft Proxy Server does not currently address this issue. However, as noted in Test Case PROX-P-1, Microsoft Proxy Server prevents visibility and access to the other systems connected to the internal adapter’s network. This seems to have no apparent security implication.
The following table presents the test lab equipment specification and configuration(s):
Test Lab SPEC-1
| Computer Name Workgroup | Network Protocol |
Operating System and Hardware Configuration |
| PROXY-1 PROXY-0 |
TCP/IP | Windows NT Server version 4.0 Microsoft Proxy Server Intel® Pentium class CPU (133 -> 166 MHz) 32 megabytes of RAM One 1.2 gigabyte hard drive Two Ethernet adapters (Windows NT compatible) Internal 0x300, IRQ 10, 10 base T External 0x270, IRQ 7, 10 base T Dual/quad speed CD-ROM Drive 3.5" floppy drive 15" SVGA color monitor |
| IR-1 WG-1 |
NetBEUI TCP/IP |
Windows NT Workstation 4.0 Windows95 SCO UNIX Microsoft Proxy Server client Intel Pentium class CPU (133 -> 166 MHz) 32 megabytes of RAM Two 1.2 gigabyte hard drive One Ethernet adapter (Windows NT and Win3.1/Windows 95 compatible) 28.8 Kbps modem Dual/quad speed CD-ROM drive 3.5" floppy drive 15" SVGA color monitor |
| PPTP-1 ROUTE-0 |
NetBEUI TCP/IP |
Windows NT Server version 4.0 Microsoft Proxy Server client Intel Pentium class CPU (133 -> 166 MHz) 32 megabytes of RAM One 1.2 gigabyte hard drive Two Ethernet adapters (Windows NT Compatible) 28.8 Kbps modem Dual/quad speed CD-ROM drive 3.5" floppy drive 15" SVGA color monitor |
| ER-1 WG-2 |
NetBEUI TCP/IP |
Windows NT Server version 4.0 Intel Pentium class CPU (133 -> 166 MHz) 32 megabytes of RAM One 1.2 gigabyte hard drive partitioned One Ethernet adapters (Windows NT and SCO UNIX compatible) Dual/quad speed CD-ROM drive 3.5" floppy drive 15" SVGA color monitor |
| NT3.51-BOX TEST |
TCP/IP | Windows NT Server 3.51 Microsoft Proxy Server client Intel 486 class CPU (66 MHz) 32 megabytes of RAM One 1.2 gigabyte hard drive One Ethernet adapters (Windows NT Compatible) Dual/quad speed CD-ROM drive 3.5" floppy drive 15" SVGA color monitor |
| AIX-BOX | TCP/IP | IBM RS/6000 model 530 32 megabytes of RAM One 1.2 gigabyte hard drive One Ethernet adapter CD-ROM drive 3.5" floppy drive 19" SVGA color monitor AIX v3.2.5 |
The following diagrams present the multiple test lab configurations used for testing. These diagrams detail computer names, IP addresses, default gateways, subnet masks, peripheral equipment, and network connections:
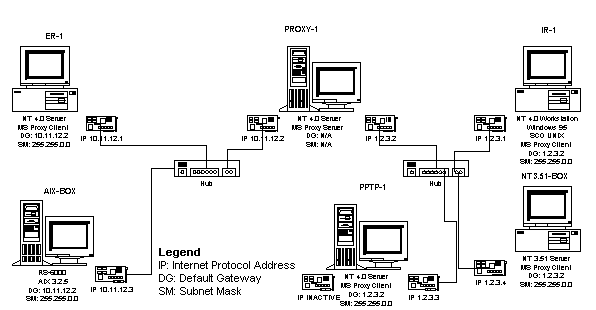
Test Lab DIAG-1

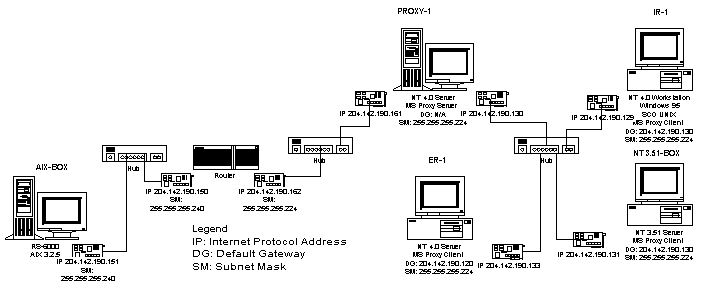
Test Lab DIAG-2
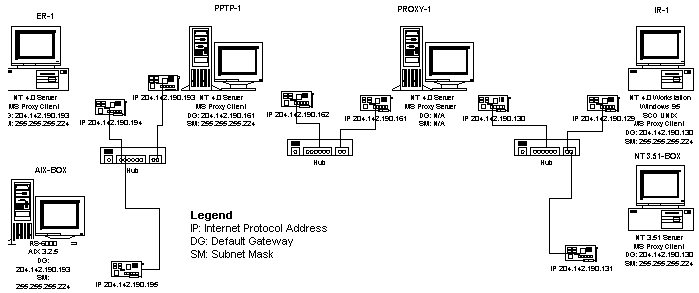
Test Lab DIAG-3
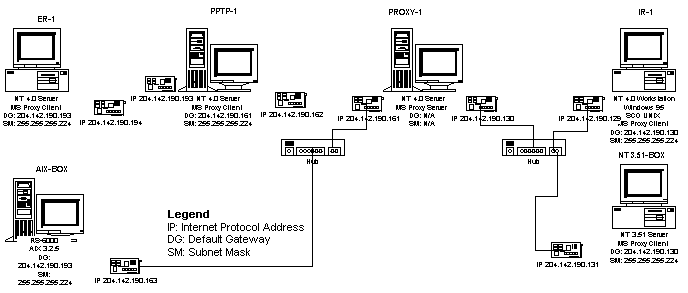
Test Lab DIAG-4
Connecting computers to the Internet provides for some very powerful and useful scenarios. It becomes possible to communicate with millions of people and computers worldwide using the TCP/IP protocols. This broad flexibility imposes a degree of risk: Not only can you communicate with people and systems using the protocols that you choose, but it is also possible for users to attempt to initiate communication with your systems.
The following list should be reviewed to learn how to reduce security risks.
Clearing the Enable IP Forwarding check box prevents unauthorized IP packets from infiltrating your network. The Enable IP Forwarding check box is located in the Microsoft TCP/IP Properties dialog box. Access this through the Network application in Control Panel.
To disable IP forwarding on Windows NT Server version 4.0:
Warning If the Windows NT Remote Access Service (RAS) is installed on your gateway after Microsoft Proxy Server is installed, IP forwarding will be enabled. You must disable IP forwarding after installing RAS.
The Windows NT File System (NTFS) provides security and access control for your data files. By using NTFS, you can limit access to portions of your file system for specific users and services.
The fewer services you are running on your system, the less likely it is that a mistake will be made in administration that could be exploited. Use the Services application in Control Panel to disable any services not absolutely necessary on your system.
Use the Bindings feature in the Network application in Control Panel to unbind any unnecessary services from any network adapter cards connected to the Internet.
For example, you might use the Server service to upload new images and documents from computers in your internal network, but you might not want users to have direct access to the Server service from the Internet. If you need to use the Server service on your private network, the Server service binding to any network adapter cards connected to the Internet should be disabled.
You can use the Windows NT Server service over the Internet; however, you should fully understand the security implications and comply with Windows NT Server licensing requirements. (When you are using the Windows NT Server service you are using Microsoft networking—that is, the Server Message Block [SMB] protocol—and all Windows NT Server licensing requirements still apply.)
The FTP Server service included with Windows NT should also be disabled or configured to ensure adequate security.
If you are running the Server service on your Internet adapter cards, be sure to double-check the permissions set on the shares you have created on the system. It is also wise to double-check the permissions set on the files contained in the shares’ directories to ensure that you have set them appropriately.
You can enable auditing of NTFS files and directories on Windows NT Server. This is done using Windows Explorer and is a useful mechanism to ensure that you have set the appropriate permissions on your shares.
By limiting the members of the Administrator group, you limit the number of users who might choose bad passwords.
User Manager for Domains provides configuration options called security policies, such as one that allows a system administrator to specify how quickly account passwords expire (forcing users to regularly change passwords), and another that determines how many bad logon attempts will be tolerated before a user is locked out. Use the User Manager for Domains security policies to configure the Server against exhaustive or random password attacks.
Although this may seem obvious, a stolen or easily guessed password is the best opportunity for someone to gain access to your system. Make sure that all users on the system, especially those with administrative rights, have difficult-to-guess passwords. In particular make sure to select a good administrator password (long, mixed-case, alphanumeric password) and set the appropriate account policies. Passwords can be set using Windows NT User Manager for Domains.
Certain listening ports such as 47, 137, 138, 139, and 1028 can be disabled. The following procedures can be used to disable these ports.
Disabling port 47
This port is used by the Proxy Server administrator’s tool (over TCP/IP with RPC calls).
Procedure:
Implications:
None
Disabling ports 137 through 139
This procedure is used to disable Windows NT TCP/IP from listening on ports 137, 138, 139:
Procedure:
Implications:
NetBIOS will not be accessible on the external (Internet) network interface.
Disabling port 102x
Ports 1024 through 1029 are allocated by Windows NT for RPC listen TCP/IP services. This procedure allows it to be configured to listen only on the internal IP interface, and as a result, these ports will no longer be visible to the Internet.
Procedure:
Implications:
RPC will only bind to the adapters listed in the HKEY_LOCAL_MACHINE\System\CurrentControlSet\Services\Rpc\Linkage\Bind.
All service packs for Windows NT Server version 4.0 and Microsoft Proxy Server should be installed. This will assure that security-related enhancements are incorporated in Microsoft Proxy Server.
Internet Security Scanner ©1994–1996
ISS SafeSuite V4.0.3
By Internet Security Systems, Inc.
Analysis Report
Summary Information
Hosts Scanned: 1
Hosts Active: 1
Hosts Inactive: 0
Start Time: Thu Oct. 3 12:27:53 1996
End Time: Thu Oct. 3 12:33:10 1996
Total Time: 5 minutes 17 seconds
Scan Completed Normally
Total Number of Vulnerability Risks: 1
Average Number of Vulnerability Risks per Active Hosts: 1.00
Maximum License Number Reached: 0
Out of Range: 0
Open Ports via Socks Service [High Risk]: 0
Open Defaults found through Telnet [High Risk]: 0
Open Defaults found through Rexec [High Risk]: 0
Open Defaults found through FTP [High Risk]: 0
Open Defaults found through POP3 [High Risk]: 0
Accounts accessible through Rsh [High Risk]: NA
X Check [High Risk]: NA
Uudecode Alias in Sendmail [High Risk]: 0
Remote Execution Hole in Sendmail [High Risk]: 0
Wizard Backdoor in Sendmail [High Risk]: 0
Remote Execution Hole through Identd [High Risk]: 0
FTP Site Exec Vulnerable [High Risk]: 0
Rlogin-froot Vulnerability [High Risk]: 0
Rsh Vulnerable in hosts.equiv [High Risk]: 0
Rexd [High Risk]: 0
HTTP (WWW server) port active [High Risk]: 0
Rsh Vulnerable through TCP Seq Prediction Spoofing [High Risk]: NA
Rsh Null Vulnerable [High Risk]: 0
Rlogin Vulnerable through TCP Seq Prediction Spoofing: 0
Admind [High Risk]: 0
Mountable [High Risk]: 0
Mountable via Portmapper [High Risk]: 0
NFS Mountable via Ultrix Remount Bug [High Risk]: 0
NFS Writable [High Risk]: 0
NFS UID Vulnerability [High Risk]: 0
NFS CD Vulnerability [High Risk]: 0
NFS MKNOD Vulnerability [High Risk]: 0
NFS Guess Vulnerability [High Risk]: 0
NFS Access Files [Medium Risk]: 0
Dynamic Linker Telnet Vulnerability [High Risk]: 0
Netbios SMB Easy Password [High Risk]: 0
Open Defaults found on Cisco device [High Risk]: 0
Open Administrative Account found on Cisco device [High Risk]: 0
Remote Execution Hole through Syslog Buffer Overflow [High Risk]: 0
RPC Statd file creation and removal vulnerability [High Risk]: 0
HTTP Proxy Penetrated [High Risk]: 0
FTP Proxy Penetrated [High Risk]: NA
HTTP (WWW server) port active [High Risk]: 0
Exploit of phf program in /cgi-bin executed an arbitrary command [High Risk]: 0
Server indicated presence of potentially exploitable program in /cgi-bin [High Risk]: 0
A CGI program executed an arbitrary command [High Risk]: 0
Server allowed exploit of .bat and .cmd bug [High Risk]: 0
A password-protected WWW resource was accessed by brute force [High Risk]: 0
Server returned a file listing for a directory that had no index [High Risk]: 0
Open Defaults found through Telnet on TIS firewall [High Risk]: 0
Open Defaults found through Telnet on Checkpoint Firewall [High Risk]: 0
Open Defaults found through FTP on Catapult [High Risk]: 0
Open Defaults found through Telnet on Raptor firewall [High Risk]: 0
Files Obtained [Medium Risk]: 0
Routed service active [Medium Risk]: 0
UUCP available [Medium Risk]: 0
Host susceptible to UDP bomb packet [Medium Risk]: 0
Finger Bomb [Medium Risk]: 0
TCP Sequence Predictable [Medium Risk]: 0
Anonymous FTP with writable directories [Medium Risk]: 0
Wall Daemon [Medium Risk]: 0
Selection_Svc Vulnerable [Medium Risk]: 0
TFTP [Medium Risk]: 0
TFTP Output [Medium Risk]: 0
NIS passwd via TCP [Medium Risk]: 0
NIS passwd via UDP [Medium Risk]: 0
Domain names and NIS Server [Medium Risk]: 0
NIS Maps [Low Risk]: 0
Anonymous FTP [Low Risk]: 0
Netbios SMB Root Share [Medium Risk]: 0
Netbios SMB Dot Dot Bug [Medium Risk]: 0
Netbios SMB NT Dot Dot Bug [Medium Risk]: 0
Chargen Service [Medium Risk]: 0
Echo Service [Medium Risk]: 0
Windows 95 Password Cache Files [Medium Risk]: 0
RIP tables modified [Medium Risk]: 0
Sync Storm [Medium Risk]: 0
Syslog Flood [Medium Risk]: 0
Data Flood [Medium Risk]: 0
Exploit of test-cgi script returned listing of /cgi-bin [Medium Risk]: 0
WWW server returned a listing of the directory above ServerRoot [Medium Risk]: 0
Netstat [Low Risk]: 0
Sysstat [Low Risk]: 0
Bootparam [Low Risk]: 0
BootparamDom [Low Risk]: 0
Finger [Low Risk]: 0
Rusers Output [Low Risk]: 0
Finger Output [Low Risk]: 0
SNMP Public Information [Low Risk]: 0
Verify Account Information about Users with Sendmail [Low Risk]: 0
Expand Account Information about Users with Sendmail [Low Risk]: 0
NNTP Daemon [Low Risk]: 0
Trace Routing of Packets: 1
Open/Close Connection Flood [Low Risk]: 0
DNS Open Connection Flood [Low Risk]: 0
RWHO Daemon Overflow [Low Risk]: 0
========== End of Report ==========
Internet Security Scanner ©1994-1996
ISS SafeSuite V4.0.3
By Internet Security Systems, Inc.
Analysis Report
Hosts Scanned: 1
Hosts Active: 1
Hosts Inactive: 0
Start Time: Thu Oct. 3 12:27:53 1996
End Time : Thu Oct. 3 12:33:10 1996
Total Time: 5 minutes 17 seconds
Scan Completed Normally
IP Address: 204.142.190.161
Hostname: proxy1e
Host is Active
Host Types:
Services:
Open Port
Port 19 not accessible
Port 139 ("netbios-ssn" service) opened.
Port 70 ("gopher" service) opened.
Port 21 ("ftp" service) opened.
Port 80 ("httpd" service) opened.
Netbios Name Table
Dump of netbios names that were found during scanning
PROXY1 (type=0x0) <ACTIVE> B
INet~Services (type=0x1c) <ACTIVE> <GROUP> B
IS~PROXY1 (type=0x0) <ACTIVE> B
WORKGROUP (type=0x0) <ACTIVE> <GROUP> B
PROXY1 (type=0x20) <ACTIVE> B
PROXY1 (type=0x3) <ACTIVE> B
WORKGROUP (type=0x1e) <ACTIVE> <GROUP> B
WORKGROUP (type=0x1d) <ACTIVE> B
____MSBROWSE___ (type=0x1) <ACTIVE> <GROUP> B
PROXY1¿¿¿¿¿¿¿¿¿ (type=0xbf) <ACTIVE> B
Master Browser Name: WORKGROUP
Station Name: PROXY1
SMB Service Name: PROXY1
Vulnerabilities:
Trace Routing of Packets
Traceroute allows you to determine the path a packet takes
between two hosts. This information allows someone to
determine network topology and routers on the network.
204.142.190.161
Hosts Trusted by scanned Hosts
No trusted hosts found.
The following tables present a suggested baseline security configuration for WinSock and Web Proxy Services.
WinSock Proxy Service Suggested Baseline Security Configuration
| Window/Configuration Option | Baseline Security Configuration |
| Service Tab | Limit the configure of the LAT to the range of addresses in the internal network. |
| Permissions Tab | Enable access control. Grant access to protocols necessary for operating your business. |
| Logging Tab | Logging enabled. Regular logging selected. Log to File selected. Automatically open new log (Daily) selected. |
| Filtering Tab | If your company has a filtering policy, it can be applied through the Properties/Filtering feature. |
Web Proxy Service Suggested Baseline Security Configuration
| Window/Configuration Option | Baseline Security Configuration |
| Service Tab | Limit the configure of the LAT to the range of addresses in the internal network. Internet publishing not enabled unless necessary. |
| Permissions Tab | Access control enabled for all protocols. Access granted to selected users for all protocols. |
| Logging Tab | Logging enabled. Regular logging selected. Log to File selected. Automatically open new log (Daily) selected. |
| Filtering Tab | If your company has a filtering policy, it can be applied through the Properties/Filtering feature |
Note Microsoft Proxy Server and all files should be installed on a secured NTFS partition separate from the Windows NT Server Version 4.0 operating system.
Assess security implications of Microsoft Proxy Server installation procedure and installation options.
The Microsoft Proxy Server installation procedure did not appear to reveal any serious security issues.
Issue
Careful configuration of the LAT is necessary for maximum security.
Description
The LAT is configured in the Local Address Table (“LAT”) Configuration window. This option requires basic knowledge of the internal network’s addresses. It is important to configure the LAT correctly because an address range greater than the internal network’s is unnecessary for Microsoft Proxy Server functionality and could cause security openings in the Proxy Server. Refer to the Interconnectivity Security Issues and Microsoft Proxy Server Security Features section of this document for additional information and the implications of this feature.
How Microsoft Proxy Server addresses this issue
The LAT can be constructed automatically using the addresses of the Proxy Server’s routing table or the standard private address ranges. This is accessible through the Construct Local Address Table window. Refer to Appendix E—Baseline Security Configuration for the recommended baseline implementation of this feature.
Issue
Accessibility of cached data to users on the internal network.
Description
Microsoft Proxy Server provides caching for HTTP resources accessed on the Internet from internal client stations. The Proxy Server cache is checked prior to all Internet data requests. Cached data is stored on disk. Certain users have access to the disk where the cache resides.
How Microsoft Proxy Server addresses this issue
A security feature of this caching is that HTTP-S pages and user-authenticated objects are not cached. This prevents one user from inadvertently viewing data that was issued to another user while in a secure mode. In addition, the cached data should be stored on a Windows NT NTFS partition that will utilize Windows NT file security.
Identify and assess Microsoft Proxy Server default security configuration and assess security implications.
All security related settings.
Issue
Microsoft Proxy Server can easily be configured to a minimal level of security.
Description
One should also note that Internet Information Server (IIS) is installed when Windows NT Server version 4.0 is installed. All IIS services (WWW, Gopher, and FTP) are started by default.
How Microsoft Proxy Server addresses this issue
The WWW IIS services are configured to prevent publishing to the Internet. For maximum security, the FTP and Gopher IIS services should be stopped.
The Microsoft-provided Appendix C—Server Security Checklist and Appendix E—Baseline Security Configuration, along with hard copy documentation and on-line help descriptions of the security features, are tools which can be used to plan and understand the features. The converse to this scenario is presented in Test Case PROX-C-3.
Test PROX-C-1 WinSock Proxy Observation Table
| Window/Configuration Option | Security Related Observations |
| Microsoft Internet Service Manager | The WinSock Proxy Service was in the running state by default after installation. |
| WinSock Proxy Services Properties/ Service | The LAT can be accessed and subsequently edited by selecting the “Edit Local Address Table (LAT)” button, by administrators only. |
| WinSock Proxy Service Properties/Permissions | Access control can be enabled through a check box. Access control was enabled for all protocols by default. Access was not granted to anyone for all protocols by default. |
| WinSock Proxy Service Properties/Logging | Logging can be selected via a checkbox. Logging was enabled by default. Regular logging or verbose logging can be selected through a toggle. Regular logging was selected by default. Logging can be to a file or a SQL/ODBC Database. Log to File was selected. The frequency for opening a new log can be set through a toggle to Daily, Weekly, Monthly, or when the file size reaches a specific size. Automatically open new log (Daily) was selected by default. The default log file directory was C:\WINNT\System32\wsplogs. |
Test PROX-C-1 Web Proxy Observation Table
| Window/Configuration Option | Security Related Observations |
| Microsoft Internet Service Manager | The Web Proxy Service was in the running state by default after installation. |
| Web Proxy Services Properties/ Service | Internet publishing can be enabled through this window. Internet publishing is not enabled by default. The LAT can be accessed and subsequently edited by selecting the “Edit Local Address Table (LAT)” button. |
| Web Proxy Service Properties/Permissions | Access control can be enabled through a checkbox. Access control was enabled for all protocols by default. Access was not granted to anyone for all protocols by default. |
| Caching | Caching can be enabled through a checkbox. Caching was enabled by default. Cache options are presented. |
| Web Proxy Service Properties/Logging | Logging can be selected via a checkbox. Logging was enabled by default. Regular logging or verbose logging can be selected through a toggle. Regular logging was selected by default. Logging can be to a file or a SQL/ODBC Database. Log to File was selected. The frequency for opening a new log can be set through a toggle to Daily, Weekly, Monthly, or when the file size reaches a specific size. Automatically open new log (Daily) was selected by default. The default log file directory was C:\WINNT\System32\w3plogs. |
Assess Microsoft Proxy Server configuration options security when set to a minimal (as close to none as possible) level of security.
Microsoft Proxy Server can be configured to a minimal level of security. Although not recommended, this level of security may be adequate for certain environments.
Issue
Microsoft Proxy Server can easily be configured to a minimal level of security.
Description
A minimal level of configurable security may include user-level access control disabled, logging disabled, and Internet Web publishing enabled. As noted in Test Case PROX-C-1, Microsoft Proxy Server does not configure to this minimal level of security by default. The administrator must configure Microsoft Proxy Server to these settings.
How Microsoft Proxy Server addresses this issue
The minimally secure configuration can easily be avoided through proper planning and completely understanding the features. The Microsoft-provided Appendix C—Server Security Checklist and Appendix E—Baseline Security Configuration, along with hard copy documentation and on-line help descriptions of the security features, are tools that can be used to plan and understand the features. The converse to this scenario is presented in Test Case PROX-C-3.
Test PROX-C-2 WinSock Proxy Observation Table
| Window/Configuration Option | Security-Related Observations |
| WinSock Proxy Service Properties/Permissions | Default Setting: Access control enabled for all protocols, no permissions granted. Minimally Secure Setting: Access control not selected. |
| WinSock Proxy Service Properties/Logging | Default Setting: Logging enabled. Regular logging selected. Log to File selected. Automatically open new log (Daily) selected. Minimally Secure Setting: Logging not enabled. |
Test PROX-C-2 Web Proxy Observation Table
| Window/Configuration Option | Security-Related Observations |
| Web Proxy Services Properties/ Service | Default Setting: Internet publishing not enabled. Minimally Secure Setting: Internet publishing enabled. |
| Web Proxy Service Properties/Permissions | Default Setting: Access control enabled for all protocols. Access not granted to anyone for all protocols. Minimally Secure Setting: Access control not selected. |
| Web Proxy Service Properties/Logging | Default Setting: Logging enabled. Regular logging selected. Log to File selected. Automatically open new log (Daily) selected. Minimally Secure Setting: Logging not enabled. |
Assess Microsoft Proxy Server configuration options security when set to a maximum level of security.
Issue
Microsoft Proxy Server can be easily configured to a maximum level of security; however, creating the most secure Microsoft Proxy Server configuration requires thought and planning.
Description
A maximum level of configurable security may include access control, verbose logging to files which are automatically created and saved on a daily basis, and Internet Web publishing disabled. As noted in Test Case PROX-C-1, Microsoft Proxy Server does not configure to this maximum level of security by default. The administrator must configure access control and logging.
How Microsoft Proxy Server addresses this issue
The Administrator must select the correct level of access without denying needed services. The maximum secure configuration can be accomplished through proper planning and completely understanding the features. The Microsoft-provided Appendix C—Server Security Checklist and Appendix E—Baseline Security Configuration, along with hard copy documentation and on-line help descriptions of the security features, are tools that can be used to plan and understand the features. The converse to this scenario is presented in Test Case PROX-C-2.
Test PROX-C-3 WinSock Proxy Observation Table
| Window/Configuration Option | Security-Related Observations |
| WinSock Proxy Service Properties/Permissions | Default Setting: Access control enabled for all protocols. Maximally Secure Setting: Access control selected. Grant access to selective users for each protocol. |
| WinSock Proxy Service Properties/Logging | Default Setting: Logging enabled. Regular logging selected. Log to File selected. Automatically open new log (Daily) selected. Maximally Secure Setting: Logging enabled. Verbose logging selected. Log to File selected. Automatically open new log (Daily) selected. |
Test PROX-C-3 Web Proxy Observation Table
| Window/Configuration Option | Security-Related Observations |
| Web Proxy Services Properties/ Service | Default Setting: Internet publishing not enabled. Maximally Secure Setting: Internet publishing not enabled. |
| Web Proxy Service Properties/Permissions | Default Setting: Access control enabled for all protocols. Access not granted to anyone for all protocols. Maximally Secure Setting: Access control enabled for all protocols. Access granted to selected users for all protocols. |
| Web Proxy Service Properties/Logging | Default Setting: Logging enabled. Regular logging selected. Log to File selected. Automatically open new log (Daily) selected. Maximally Secure Setting: Logging enabled. Verbose logging selected. Log to File selected. Automatically open new log (Daily) selected. |
Issue
It is possible to configure Microsoft Proxy Server to forward IP traffic between its two network interface cards.
Description
The IP Forwarding function becomes active when the IP Forwarding checkbox is selected pre-or post the Microsoft Proxy Server installation. When Microsoft Proxy Server is installed, there is no warning indicating IP Forwarding is active. Risk is incurred for administrators who may select IP Forwarding with Microsoft Proxy Server installed without understanding the consequences.
How Microsoft Proxy Server addresses this issue
This issue can be addressed procedurally. The administrator must be attentive to the status of the IP Forwarding checkbox.
Test PROX-C-4 Observation Table
| PROXY-1 IP Forwarding | From |
To |
Attempt To | Result |
| Disabled | IR-1 | PROXY-1 204.142.190.130 | Ping | Reply |
| Disabled | IR-1 | PROXY-1 204.142.190.161 | Ping | Reply |
| Disabled | IR-1 | PPTP-1 204.142.190.162 | Ping | Reply |
| Disabled | PPTP-1 | PROXY-1 204.142.190.161 | Ping | Reply |
| Disabled | PPTP-1 | PROXY-1 204.142.130 | Ping | Reply |
| Disabled | PPTP-1 | IR-1 204.142.190.129 | Ping | Timed Out |
| Enabled | IR-1 | PROXY-1 204.142.190.130 | Ping | Reply |
| Enabled | IR-1 | PROXY-1 204.142.190.161 | Ping | Reply |
| Enabled | IR-1 | PPTP-1 204.142.190.162 | Ping | Reply |
| Enabled | PPTP-1 | PROXY-1 204.142.190.161 | Ping | Reply |
| Enabled | PPTP-1 | PROXY-1 204.142.130 | Ping | Reply |
| Enabled | PPTP-1 | IR-1 204.142.190.129 | Ping | Reply |
The table above details the results of Ping (ICMP echo protocol) tests between the internal and external networks under different conditions of the IP Forwarding checkbox.
When an echo request is sent to a Microsoft Proxy Server with a destination address of the internal network adapter, the internal adapter will respond. If the response of the internal adapter address is detected by an outside entity, it could aid in designing a more focused attack on the internal network. Although designing a more focused attack may not be directly possible through the Microsoft Proxy Server, the information could be used if another entry point was also identified (for example, a dial-in SLIP or PPP line), and later used to penetrate the network.
Determine the security impact of configuring the internal (private) network for addresses that are being used on the external (public) network. This is the basis for a spoofing attack if Microsoft Proxy Server does not respond properly in such a configuration.
| Sub-net | System | IP Address | Net Mask |
| External | AIX Server | 204.142.190.151 | 255.255.255.240 |
| Router (Ext Adapter) | 204.142.190.150 | 255.255.255.240 | |
| Intermediate | Router (Int Adapter) | 204.142.190.162 | 255.255.255.224 |
| Proxy (Ext Adapter) | 204.142.190.161 | 255.255.255.224 | |
| Internal | Proxy (Int Adapter) | 204.142.190.130 | 255.255.255.224 |
| SCO client | 204.142.190.129 | 255.255.255.224 | |
| Windows NT client | 204.142.190.133 | 255.255.255.224 |
Test the level of access between internal and external networks when the internal client does not have Microsoft Proxy Server client software installed or if both the external and internal machines run a non-Microsoft Proxy Server–supported operating system.
Microsoft Proxy Server successfully prevented non-proxy clients from using services beyond the Proxy Server.
Test PROX-F-2 Observation Table
| PROXY-1 IP Forwarding | From |
To |
Attempt To | Result |
| Enabled | IR-1 | AIX-BOX 204.142.190.195 | Finger | Reply |
| Enabled | IR-1 | AIX-BOX 204.142.190.195 | FTP | Login Connection |
| Enabled | IR-1 | AIX-BOX 204.142.190.195 | Telnet | Login Connection |
| Enabled | AIX-BOX | IR-1 204.142.190.129 | Finger | Reply |
| Enabled | AIX-BOX | IR-1 204.142.190.129 | FTP | Login Connection |
| Enabled | AIX-BOX | IR-1 204.142.190.129 | Telnet | Login Connection |
| Disabled | IR-1 | AIX-BOX 204.142.190.195 | Finger | Timed Out |
| Disabled | IR-1 | AIX-BOX 204.142.190.195 | FTP | Timed Out |
| Disabled | IR-1 | AIX-BOX 204.142.190.195 | Telnet | Timed Out |
| Disabled | AIX-BOX | IR-1 204.142.190.129 | Finger | Timed Out |
| Disabled | AIX-BOX | IR-1 204.142.190.129 | FTP | Timed Out |
| Disabled | AIX-BOX | IR-1 204.142.190.129 | Telnet | Timed Out |
Test the functionality of Microsoft Proxy Server’s logging mechanism.
Issue
Configuration of the logging feature.
Description
The logging processes gather a significant amount of information about any connected process. This makes the logging facility a valuable tool for tracking system usage and monitoring individual user activity. Without logging, the ability of the system administrator to track the system usage and to prevent unauthorized activity is severely limited. Operating the Microsoft Proxy Server without logging should be considered insecure. Refer to the Interconnectivity Security Issues and Microsoft Proxy Server Security Features section of this document for additional information and the implications of this feature.
How Microsoft Proxy Server addresses this issue
As indicated in Test Case PROX-C-1, regular logging to a new file on a daily basis is selected by default. This configuration may be adequate for certain environments. Test Case PROX-C-3 and Appendix E—Baseline Security Configuration provide information on the recommended settings for the logging feature.
Test Case PROX-F-3: Regular and Verbose Logging Observation Table
| Regular logging records the following: | Verbose logging records the following |
| client machine IP address | client machine IP address |
| client user name | client user name |
| Log date | client agent |
| Log time | client platform |
| Service name | Authentication Status |
| Destination name IP address | Log date |
| Destination port | Log time |
| Protocol name (TCP, UDP) | Service name |
| Object name | Proxy name |
| Object Source | Referring Server name |
| Result code | Destination name Destination address Destination port Processing time Bytes received Bytes sent Protocol name Transport Operation Object name Object MIME Object source Result code |
To determine which IP addresses respond to an ICMP echo (ping) request on the various sub-nets where the Microsoft Proxy Server is attached. The primary objective is to determine which IP addresses answer to untrusted systems connected to the external network.
The file /tmp/fping.out will contain the list of IP addresses which answered or did not answer the ICMP echo request (ping).
Issue
The internal adapter of machine PROXY-1 (the dual-homed Proxy Server) unexpectedly answered the echo request from an external system.
Description
When an echo request is sent to a Microsoft Proxy Server with a destination address of the internal network adapter, the internal adapter will respond. If the response of the internal adapter address is detected by an outside entity, it could aid in designing a more focused attacked on the internal network. Although designing a more focused attack may not be directly possible through the Microsoft Proxy Server, the information could be used if another entry point was also identified (for example, a non-secured dial-in SLIP or PPP line), and later used to penetrate the network.
How Microsoft Proxy Server addresses this issue
Microsoft Proxy Server does not currently address this issue. However, Microsoft Proxy Server prevents visibility and access to the other systems connected to that adapter’s internal network.
Test PROX-P-1 Observation Table
| From | To | Result |
| Internal Network | External Subnet | Fping not answered |
| Internal Network | Internal Subnet | 1.2.3.0 1.2.3.1 1.2.3.2 1.2.3.3 1.2.3.4 |
| External Network | Internal Subnet | 1.2.3.2 |
| External Network | External Subnet | 10.11.12.1 10.11.12.2 10.11.12.3 |
To determine which TCP/IP ports a Windows NT Server will answer to when running the Microsoft Proxy Server using the default configuration options.
# ./strobe proxy1 2> /tmp/strobe.outThe file /tmp/strobe.out will contain a complete listing of all of the TCP/IP ports that allowed connections. This file can then be used for further analysis and customization of additional attack scenarios and penetration test cases.
Issue
The strobe utility detected seven TCP ports answering to external network connections. Three of these were expected: FTP, HTTP, and Gopher. Four of these were unexpected: NI FTP (port 47), Location Server (port 135), NetBIOS (port 139), and Port 1028.
Description
Each of the TCP/IP service ports identified by “Strobe” represents a possible avenue of external attack by another TCP/IP service specific penetration tools and techniques. In the penetration test cases that follow this test, each of the significant responding ports are further tested for security vulnerabilities.
How Microsoft Proxy Server addresses this issue
This issue can be addressed procedurally. Many of the identified ports can be disabled. The Microsoft-provided Appendix C—Server Security Checklist provides guidance on disabling ports 47, 139, and 1028 on the external adapter of a Windows NT Server running Microsoft Proxy Server. FTP port 21 and gopher port 70 can be disabled using the Internet Information Server management tool. Port 135 cannot currently be disabled. The RPC service will unconditionally listen on port 135 on all interfaces, and relies on Windows NT RPC authentication for security; however, our testing did not show any vulnerability related specifically to this issue.
Test Case PROX-P-2 Observation Table
| From | To | Result |
| External AIX-BOX | PROXY-1 204.142.190.161 | proxy1eftp21/tcp File Transfer [Control] [96,JBP] proxy1eni-ftp47/tcp NI FTP [134,SK8] proxy1egopher70/tcp Gopher [MXC1] proxy1ewww80/tcp World Wide Web HTTP [TXL] proxy1eloc-srv135/tcp NT RPCSS proxy1enetbios-ssn139/tcp NETBIOS Session Service [JBP] proxy1eunknown1028/tcp unassigned |
| AIX-BOX | PROXY-1 204.142.190.130 | proxy1iftp21/tcp File Transfer [Control] [96,JBP] proxy1ini-ftp47/tcp NI FTP [134,SK8] proxy1igopher70/tcp Gopher [MXC1] proxy1iwww80/tcp World Wide Web HTTP [TXL] proxy1iloc-srv135/tcp Location Service [JXP] proxy1inetbios-ssn139/tcp NETBIOS Session Service [JBP] proxy1iunknown1028/tcp unassigned |
To determine if the Microsoft Proxy Server is susceptible to any of the common Internet weaknesses identified by the Internet Security Scanner public domain security analyzer/tool.
The ISS utility will analyze all target systems for the following Internet risks and/or vulnerabilities:
# ./strobe 204.142.190.193 204.142.190.193# ./strobe 204.142.190.129 204.142.190.130The file ../ISS.log (directory in which ISS was run) will contain a complete listing of all of the ISS utility findings. This file can then be used for further analysis and customization of additional attack scenarios and penetration test cases.
ISS: Run against the external adapter from the external network (without options specified on the command line)
--> Inet Sec Scanner Log by Christopher Klaus ©1993 <--
E-mail: cklaus@hotsun.nersc.gov coup@gnu.ai.mit.edu
ISS: Run against the external adapter from the external network (with the -p command line option specified)
--> Inet Sec Scanner Log by Christopher Klaus ©1993 <--
E-mail: cklaus@hotsun.nersc.gov coup@gnu.ai.mit.edu
==============================================================
Host 10.11.12.2, Port 21 ("ftp" service) opened.
Host 10.11.12.2, Port 47 opened.
Host 10.11.12.2, Port 70 opened.
Host 10.11.12.2, Port 80 opened.
Host 10.11.12.2, Port 135 opened.
Host 10.11.12.2, Port 139 opened.
Host 10.11.12.2, Port 1029 opened.
The ISS utility, in its FreeWare and unmodified release form, did not attempt to perform any of its tests beyond the initial port scan (and this required using the -p command line option).
To determine if the Microsoft Proxy Server is susceptible to any of the common Internet weaknesses identified by the Satan public domain security analyzer/tool.
The Satan utility will analyze all target systems for the following additional (over ISS) Internet risks and/or vulnerabilities:
An attack level of 2 (command line of -a 2)
A proximity descent level of 2 (command line of -A 2 -l 2)
# ./Satan -a 2 -A 2 -l 2 proxy1The file ../results/Satan-data/facts (directory where Satan was run) will contain a complete listing of all of the Satan utility findings. This file can then be used for further analysis and customization of additional attack scenarios and penetration test cases.
Issue
The only issue reported by the Satan utility was its ability to identify the Proxy Server was offering an Anonymous FTP service.
Description
The Anonymous FTP service is an optional part of the Windows NT Server that was configured by default prior to the installation of the Proxy Server. The FTP service is installed as part of the Internet Information Server. The presence of Anonymous FTP service represents a possible avenue of external attack if misconfigured. Test Case PROX-P-5 tests this for security vulnerabilities within the FTP service.
How Microsoft Proxy Server addresses this issue
This issue can be addressed procedurally. FTP port 21 can be disabled using the Internet Information Server management tool.
Satan: Run against the external adapter from the internal network
proxy1i|135:TCP|a|x||||offers 135:TCP
proxy1i|http|a|x|||HTTP/1.0 400 Bad Request\r\nContent-Type: text/html\r\n\r\n<body><h1>HTTP/1.0 400 Bad Request\r\n</h1></body>|offers http
proxy1i|ftp|a|x|||220 proxy1 Microsoft FTP Service (Version 2.0).\r\n221 \r\n|offers ftp
proxy1i|47:TCP|a|x||||offers 47:TCP
proxy1i|ftp|a|x|||ANONYMOUS|offers anon ftp
proxy1i|gopher|a|x|||3 --6 Bad Request. \r\n.\r\n|offers gopher
proxy1i|tcpscan.satan 1-9999|u|||||program timed out
proxy1i||a|||||rpcinfo error #256
proxy1i|udpscan.satan 1-2050,32767-33500|u|||||program timed out
Satan: Run against the external adapter from the external network
proxy1e|ftp|a|x|||220 proxy1 Microsoft FTP Service (Version 2.0).\r\n221 \r\n|offers ftp
proxy1e||a|||||rpcinfo error #256
proxy1e|udpscan.satan 1-2050,32767-33500|u|||||program timed out
proxy1e|47:TCP|a|x||||offers 47:TCP
proxy1e|ftp|a|x|||ANONYMOUS|offers anon ftp
proxy1e|gopher|a|x|||3 --6 Bad Request. \r\n.\r\n|offers gopher
proxy1e|135:TCP|a|x||||offers 135:TCP
proxy1e|tcpscan.satan 1-9999|u|||||program timed out
proxy1e|http|a|x|||HTTP/1.0 400 Bad Request\r\nContent-Type: text/html\r\n\r\n<body><h1>HTTP/1.0 400 Bad Request\r\n</h1></body>|offers http
To attempt manual anonymous FTP penetration attempts.
# ftp 201.142.190.161
Name (201.142.190.161:root) anonymous
Password: test@unix.com
ftp> pwd
ftp> ls –l and ftp> dir
The tester should take note of all messages displayed by the FTP utility during the course of this test.
Issue
The FTP Server allowed the external system to gain a successful anonymous login.
Description
The Anonymous FTP service is an optional part of the Windows NT Server that was configured by default prior to the installation of the Proxy Server. The FTP service is installed as part of the Internet Information Server. The presence of Anonymous FTP service represents a possible avenue of external attack.
How Microsoft Proxy Server addresses this issue
The coexistence of a properly configured (which is the default) FTP Server in the same system with the Microsoft Proxy Server does not appear to present any additional vulnerabilities to the proxy service, Windows NT operating system, or the internal network behind the Server. The FTP Server allowed the external system to gain a successful anonymous login. The default configured FTP Server could not be compromised through standard manual penetration techniques as listed in this test case. In addition, if not required, FTP port 21 can be disabled.
To attempt to exploit the fact that the Microsoft Proxy Server allows connections to the unused TCP/IP port 47 (as a previous run of strobe detected). C&L focused on this port because it is the only additional port that started accepting TCP/IP connection requests after the Proxy Server was installed and is identified by Microsoft as a port that can be used to administrate the Proxy Server.
Issue
Microsoft Proxy Server allows connections to port 47.
Description
The ability to connect to port 47 represents a possible avenue of external attack by more service-specific penetration tools and techniques.
How Microsoft Proxy Server addresses this issue
This issue can be addressed procedurally. Port 47 can be disabled. The Microsoft-provided Appendix C—Server Security Checklist provides guidance on disabling port 47 on the external adapter of a Windows NT Server running Microsoft Proxy Server. In addition, Microsoft Proxy Server’s allowing connections to port 47 seems to have no apparent security implication. A denial of service attack does not appear to be effective against this open port.
The commercial ISS SafeSuite utility will analyze all target systems with an intense series of platform and network related vulnerabilities.
Note It will be necessary to obtain and install a key file from ISS which will allow testing of the specific IP address that is being used by the external adapter of the Microsoft Proxy Server.
# ./xissNote The above two tests do not apply to any of the services offered by or answered to by Microsoft Proxy Server. Therefore, their exclusion should have no impact on the overall test results.
Issue
The only issue raised by the ISS tool was that the Proxy Server allowed Trace Routing packets to be passed between its two network interfaces.
Description
Trace Routing is when a router allows packet routing information to be echoed through to both attached networks. This information can be helpful to attackers in determining internal network addressing schemes when looking to exploit weaknesses on other systems connected to the internal network. This issue was also identified in Test Case PROX-P-1 when the Proxy Server allowed its internal network adapter to respond to a general echo (ping) request. This issue was noted because the Proxy Server’s internal network adapter answered.
How Microsoft Proxy Server addresses this issue
Microsoft Proxy Server does not currently address this issue. However, as noted in Test Case PROX-P-1, Microsoft Proxy Server prevents visibility and access to the other systems connected to the internal adapter’s network. This seems to have no apparent security implication.
Microsoft Proxy Server is a software product that provides a gateway to the Internet. Microsoft management represents that the product achieves the following objective:
We have examined management's assertion that the Microsoft Proxy Server, when implemented properly in accordance with Microsoft recommendations, is suitably designed to provide a reasonable and practical level of protection for Internet connections. This assertion was prepared by and is the responsibility of Microsoft management.
Our examination was made in accordance with standards established by the American Institute of Certified Public Accountants and, accordingly, included obtaining an understanding of the internal control structure of the product and such other procedures as we considered necessary in the circumstances. We believe that our examination provides a reasonable basis for our opinion.
Because of limitations inherent in the internal controls incorporated in software products and the impracticability of using all types of penetration tools and techniques, security controls may be breached and not be detected. Also, projections of any evaluation of controls to future periods are subject to the risk that controls may become inadequate because of changes in conditions, such as the introduction of more powerful tools or techniques to compromise information security.
In our opinion, management's assertion that the Microsoft Proxy Server, when implemented properly in accordance with Microsoft recommendations, is suitably designed to provide a reasonable and practical level of security for Internet connections as of December 15, 1996 is fairly stated, in all material respects, based upon the criteria included in the assertion.
This document (the “Evaluation”) presents certain discussions and recommendations concerning Microsoft Proxy Server security. The Evaluation is based on Microsoft Proxy Server (Build 167) running on Windows NT Server version 4.0 RTM (Build 1381), and to a large extent upon technical documentation and other information developed and supplied by Microsoft. Coopers & Lybrand L.L.P. (“C&L”) did not review source code for dormant flaws, and cannot ensure that every potential weakness that might arise in the future has been identified. The Evaluation is based upon a collection of methodologies and tests interacting at a single point in time with an Internet environment that is continually changing and becoming ever more complex. Internet security is continuously being assaulted by increasingly sophisticated and resourceful hackers and other criminals. Just as software virus protection programs are hard put to remain more than a small step ahead of the virus perpetrators, security analyses and recommendations may unexpectedly become outdated. C&L and the individual authors of this report (collectively, the “Authors”) have used methodologies and software they believe to be reliable in evaluating the security issues presented, but the Authors make no representations or warranties concerning either those methodologies and software or the results obtained from their use. While the Authors believe that the material in this Evaluation presents a fair and reasonable picture of Microsoft Proxy Server security controls, nothing herein can substitute for each reader’s own professional and business judgment, independent investigations, and research into the subjects covered. All information presented herein is of a general nature and may not be applicable to any particular situation. Nothing herein constitutes an endorsement of any product by the Authors.
It is important to note that not all types of penetration tools and techniques were utilized or attempted for the Evaluation. The tests executed in the Evaluation utilized penetration testing tools and techniques common to the security industry. Many penetration attempts rely on long periods of time to analyze and understand targets, utilize intermediary nodes and networks, and employ automated techniques that may run unattended for extended periods of time. Such long term testing was beyond the scope of the Evaluation. In addition, penetration tests provide information regarding only very specific security vulnerabilities and should not be viewed as conclusive of Microsoft Proxy Server’s overall security posture.
The results of the Evaluation cannot disclose any weakness that may exist in prior or future versions.
The Evaluation focused on technical controls. There are additional non-technical techniques, such as social engineering, dumpster diving, and others, that have proven to be very effective in circumventing security controls but were not addressed for the Evaluation. Please see the Bibliography for additional information regarding these issues.
Firewalls and Internet Security: Repelling the Wily Hacker, Cheswick and Bellovin (Addison-Wesley Publishing Company, 1994)
Network Security: How to Plan for it and Achieve it, Baker (McGraw-Hill, Inc., 1995)
Computer Communications Security: Principles, Standard Protocols and Techniques, Ford (Prentice-Hall, Inc., 1994)
Complete LAN Security and Control, Davis, (McGraw-Hill, Inc., "Windcrest", 1994)
Coopers & Lybrand L.L.P. is one of the world's leading professional services firms providing audit, tax, management consulting, financial advisory, and human resource advisory services to clients in a broad range of industries on a globally integrated basis in 140 countries. In the United States, the firm has been serving clients since 1898 and today has 17,000 partners and staff working in over 100 offices. Organized along industry lines, the firm seeks to create value for its clients and to bring a competitive advantage to their activities. Its clients include a variety of large and small, publicly and privately held companies, many numbered among the Fortune 500.
Coopers & Lybrand L.L.P. has recognized the risks and threats to information since the early stages of information technology development. Their original approach to auditing computer-based systems included the study and evaluation of controls over the security of information. The firm has since established the Information Technology Security Services (ITSS) national practice dedicated to serving their clients’ needs in addressing security over one of their most important resources—technology generated and resident information. The ITSS professionals are recognized leaders in the fields of information technology, telecommunications, logical and physical security, and auditing. They are knowledgeable in the latest security tools and methods, and in evaluating, analyzing, developing, and implementing security and control solutions.
Services offered by the ITSS practice include Information Security Assessment, Information Security Risk Analysis, Security Plan Development, Internet Connectivity Pre-Implementation Review, Firewall Review, Operating System Security Review, Penetration Testing, Policy and Procedure Development, Business Continuity Planning Review, and Training.
David Rivera is a Senior Technical Manager of C&L's IT Security Services (ITSS) practice and has over 19 years experience in data processing. David leads C&L's technical team for Internet and UNIX Security Services. David's technical capabilities include internal knowledge of UNIX, TCP/IP, and all Internet protocols and services. David also leads focused Internet penetration exercises from C&L’s Internet testing lab in New York. David earned an M.S. degree in Computer Science and a B.S. in Computer Technology from the New York Institute of Technology.
James Jumes is a Manager of C&L’s Business Systems Advisory Services (BSAS) and Security practices and has over ten years of information technology strategy, business system selection and implementation, and security experience. James is one of the principal authors of the book Windows NT 3.5 Guidelines for Security, Audit, and Control and has developed a Windows NT 3.5x security review program and recommendations tool. James earned an M.B.A. from Lehigh University and an M.Ed. and B.A. in Psychology from Boston College.
Neil Cooper is a Technical Manager of C&L’s Information Technology Security Services (ITSS) practice, and has over 16 years experience in data processing. Neil has primary responsibility for leading the Windows NT security service line for C&L and is part of C&L's technical team for UNIX, Windows NT, Netware, and Internet Security Services. Neil's technical capabilities include knowledge of Windows NT, UNIX, TCP/IP, and X-Windows, as well as mid-range systems. Neil earned both a B.S. and M.S. degree in Geology from Penn State University and the University of Delaware.
Christopher O'Hara is a Senior Technical Specialist in C&L’s Information Technology Security Services (ITSS) practice. Chris' technical focus is on a variety of UNIX variants (SunOS, Solaris, IBM AIX, Linux, HP-UX), Internet security (firewalls, topologies, protection strategies), TCP/IP networking, remote access connectivity, and DEC VAX/VMS data security assessments. In this capacity he has reviewed system configurations, network topologies, and network access points, and assessed the appropriateness of the related security controls. Chris earned a B.S. in Computer Information Systems from the University of Scranton.
Bruce Murphy is the National Partner of Coopers & Lybrand's ITSS practice based out of the New York region. He has over eleven years of experience implementing access control mechanisms, from a management, technical, and procedural perspective, across PC, LAN, mid-range, and mainframe computing platforms. Bruce lectures frequently on many areas of information security, including Electronic Commerce, Multi-Platform Network Architectures, Local Area Networks, Toll Fraud, and Advanced Authentication Techniques. Bruce earned a B.A. in English from Muhlenberg College, is President of the New Jersey ISSA chapter, and is designated a Certified Information Systems Security Professional.