Feature Summary
Web Proxy Service Features
WinSock Proxy Service Features
Microsoft Proxy Server provides:
Extensive protocol support. Microsoft Proxy Server is compatible with most Internet protocols and Windows Sockets-based applications. On your private network it supports both Internet Packet Exchange/Sequenced Packet Exchange (IPX/SPX) and Transport Control Protocol/Internet Protocol (TCP/IP).
Security. It prevents unauthorized external access to your private network, and eliminates the need to connect clients directly to the Internet. It provides user-level security and Windows NT Challenge/Response authentication. Data encryption is supported by means of Secure Sockets Layer (SSL) tunneling.
Access control. Access can be managed by user, service, port, and Internet domain, for both inbound and outbound connections.
Ease of use. Microsoft Proxy Server is easy to install, manage, and monitor.
Integration with Windows NT Server. Microsoft Proxy Server integrates with the networking, security, and administrative interface of the operating system.
Performance. Microsoft Proxy server is extensively engineered to take advantage of the performance and scaleability offered by the Windows NT Server operating system. Additional features provided by Microsoft Proxy Server, such as caching, offer improved client performance and lower network costs.
With Microsoft Proxy Server, clients can access the Internet through the Web Proxy service or the WinSock Proxy service.
The Web Proxy service:
The WinSock Proxy service:
Web Proxy Basics
Client Authentication
Domain Filtering
Caching
Proxy is defined in general terms as “authority or power to act for another.” In the context of network computing, a proxy service is a service provided by a computer that assumes authority and power to act for computers to which it is connected. Such a service is useful in situations that require computers on networks that are not directly connected to each other to exchange information. A proxy service allows information exchange while maintaining security for individual computers.
Proxy services are particularly appropriate for today’s environment, in which the popularity and growth of the Internet has created a need for corporations, organizations, and schools to allow Internet access from client computers on their private network. At the same time, these entities need to isolate their private network from the Internet for a variety of reasons, including security, private addressing, and transport incompatibility. A proxy service reconciles these potentially incompatible needs.
A proxy service runs on a computer with at least two network adapter cards, one for each network to which it is connected. Typically, this computer is the only computer to which both networks are connected. The computer running the proxy service thus serves as a gateway computer between the two networks. Larger networks may have multiple gateway computers, each running the proxy service. The following figure shows a common scenario implemented using Microsoft Proxy Server. The Web Proxy service provides a private network client with access to the Internet.
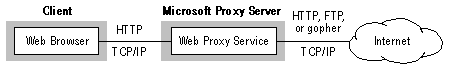
With Microsoft Proxy Server, if both networks are running Transmission Control Protocol over Internet Protocol (TCP/IP) you should disable routing by clearing the Enable IP Routing check box in the Windows NT Server TCP/IP Advanced Configuration dialog box. Disabling this feature means that there can be no direct routing between the two networks: All information must pass through the proxy service.
The Web Proxy service supports proxy requests from any browser that is compatible with the standard CERN proxy protocol, such as Microsoft Internet Explorer or Netscape Navigator. The browser can be on a computer running any operating system platform, such as Windows, Windows NT, Macintosh, or UNIX. The browsers must be configured to use the proxy server, but the Web Proxy service requires no client-side components (because all client support needed for this standard protocol is built into most popular browsers).
The Web Proxy service includes such features as domain filtering, Internet resource caching, and client authentication. The Secure Sockets Layer (SSL) tunneling protocol is also supported. SSL Tunneling allows a client to create a connection to a server through the proxy for sending and receiving encrypted data that cannot be interpreted by the proxy. This is used for SSL with the HTTPS protocol, and the secure news protocol, SNEWS.
The Web Proxy service has built-in request logging that allows log records to be written to a flat file or to a database by using Open Database Connectivity (ODBC). This logging is separate from the logging built into the WWW service of Internet Information Service (IIS) and includes proxy-specific information.
Microsoft Proxy Server can be configured to allow anonymous requests by users, or to require users to be authenticated (validated) by the server. Once users are authenticated, access control configuration determines which protocols (Web, FTP, or Gopher) are accessible for each user. Users can be granted access to selected protocols.
Access control is integrated into Windows NT security and administration. The user accounts used for logon, or authentication, are created with User Manager, the standard User Account administration tool. Each Internet protocol (Web, FTP, Gopher) is represented within Microsoft Proxy Server by an object on which Access Control Entries (ACEs) can be applied, indicating which users have access to the protocol, and which users do not. Assignment of Access Control Entries is done in Internet Service Manager.
A convenient way to configure user-level access control is with Local Groups. With User Manager, an administrator can create groups, and add user accounts to these groups. Within Internet Service Manager, the site would assign Access Control to each group, as appropriate. For example, one group may have HTTP access only, and no FTP access. When a user joins or leaves, no changes would be necessary in Internet Service Manager; the user account can be added or removed from a group by using User Manager.
Microsoft Proxy Server supports two forms of user authentication: HTTP Basic authentication, and Windows NT Challenge/Response authentication. When using Basic authentication, the user sends a request by typing in a URL or clicking a hyperlink. The server responds with an “authentication failure” message to the client, and clients typically display a user name/password dialog box in response. The user enters a valid user name and password, and the browser reissues the same request, but this time the header contains user information, which is used by the server to authenticate the user.
In order for basic authentication to work with Microsoft Proxy Server, the browser being used must support the new “proxy-authenticate” HTTP header; Internet Explorer 3.0 supports this. Earlier versions of Internet Explorer do not support this header, and therefore do not support HTTP Basic Authentication through a proxy.
Basic authentication does not encrypt your user name and password before transmission. Basic authentication is encoded only by using UUencode, and can be decoded easily by anyone with access to your network, or to a segment of the Internet that transfers your packets.
Warning If you use Basic authentication, you will send your Windows NT user name and password in clear text (unencrypted) over public networks. Intruders could easily learn user names and passwords.
Windows NT Challenge/Response authentication uses the same secure mechanism for Microsoft Proxy Server logon that is used by clients that log on to a Windows NT-based computer. When this mechanism is used, the user needs to be logged on to the client computer, with a computer or domain user account that is valid on the computer running Microsoft Proxy Server . When the user issues a request, the Windows NT Challenge/Response protocol is used between client and server. Windows NT Challenge/Response authentication requires that the browser support the “proxy-authenticate” HTTP header, as well as HTTP Keep-Alives to a proxy, and NT Challenge/Response. Once a user is authenticated, the user remains authenticated for the life of the TCP connection (by use of the Keep-Alive mechanism). Internet Explorer 3.0 supports these requirements; earlier versions of Internet Explorer do not.
The Microsoft ActiveX™ Software Development Kit (SDK) includes information for third parties on how to support the Windows NT Challenge/Response protocol in Web browsers, whether they directly connect to Web servers or use proxy servers.
Microsoft Proxy Server offers the ability to control which Internet sites are accessible to private network clients. The Web Proxy service can be configured to grant access to all Internet sites except for the ones specified, or it can be configured to deny access to all Internet sites except for the ones specified. In either case, the list of sites applies to all requests issued to the Web Proxy service on that server. It is currently not possible to specify domain filtering on a user-level basis, although different Microsoft Proxy Servers on your network can offer access to different sites and for different users. (Also, the open, documented Internet Server API (ISAPI) provides an extensible means for third parties to provide customized filtering.)
Each entry in the grant/deny list can be an IP address, an IP subnet, or a domain name. A domain name can be a computer name (such as www.microsoft.com), or a domain name that represents multiple computers (such as microsoft.com), in which case the entry applies to all computers in the domain.
If domain filtering is enabled, the Proxy ISAPI application verifies that each WWW, FTP, and Gopher request is directed to an Internet site to which access is permitted, before issuing the request to the site. If access is not permitted, an error message is returned to the client.
If the request specifies a Domain Name System (DNS) site name, the site name is resolved to an Internet Protocol (IP) address, and both the DNS name and IP address are searched for in the domain filtering site list. If a client request is received that specifies an IP address rather than a DNS name, the IP address is searched for in the domain filtering site list, and if at least one entry in the site list contains a domain name, the request’s IP address is converted to a DNS name by doing a DNS reverse resolution, and the domain name is searched for in the site list.
The Web Proxy service uses caching to maintain local copies of Web objects. Subsequent requests for these objects can be serviced from a local disk copy rather than issuing the request over the Internet, which improves user-perceived performance and reduces bandwidth consumption on the site’s Internet connection.
The Web Proxy service caching provides the following features:
Passive caching uses the cache to store all cacheable objects returned to Microsoft Proxy Server by Internet servers. Many objects on the Web have characteristics that make them difficult or impossible to cache properly (for example, they might be dynamically generated, or require authentication for access). For this reason, the caching system only caches appropriate objects. Microsoft Proxy Server calculates a Time-To-Live (TTL) for all objects in the cache. When an object’s TTL has expired, the next request for the object is serviced on the Internet instead of the cache. For more information about caching, see Appendix D, “Architecture.”
Active caching uses the cache to proactively ensure the freshness and availability of popular objects. In this mechanism, the cache manager creates its own request for an object, without client prompting, when the TTL has expired or is near expiration. Web objects are subject to active caching on the basis of their popularity relative to their rate of change. Additionally, the active caching algorithm incorporates calculations of current server load in order to process requests to the Internet at times of low usage.
Returning expired objects when an Internet site is unavailable maintains potentially stale data in the cache. Expired objects can be used to service client requests sent to a remote server when that remote server is temporarily inaccessible.
Windows Sockets is a mechanism for interprocess communication (IPC) between applications running on the same computer, or on different computers connected by a local area network (LAN) or wide area network (WAN). Windows Sockets defines a set of standard APIs that an application uses to communicate with one or more other applications, usually across a network. Windows Sockets supports initiating an outbound connection (for clients), accepting an inbound connection (for servers), sending and receiving data on those connections, and terminating the connection.
WinSock Proxy is a mechanism that makes a Windows Sockets-compatible application running on a private network perform as if it were directly connected to the Internet, when actually there is a gateway computer connecting the two networks. The client application calls Windows Sockets APIs to communicate with an application running on an Internet computer. The WinSock Proxy components redirect the necessary APIs to the gateway computer, thus establishing a communication path from the internal application to the Internet application through the gateway computer. This is totally transparent to the two applications.
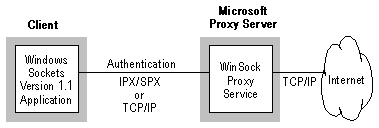
The WinSock Proxy service provides the following features:
WinSock Proxy supports communication over TCP/IP and IPX/SPX on the private network. However, only applications that are written to use Windows Sockets over TCP/IP (Internet applications) can be redirected.
Because Winsock Proxy Supports communication on the private network by use of the IPX/SPX transport protocol, it allows access to Internet sites from Internet applications on IPX/SPX networks by using IPX/SPX communications between the client and Microsoft Proxy Server. It also allows access to internal Web sites from Web browsers on IPX/SPX networks by using IPX/SPX communications between the client and Microsoft Proxy Server, with Microsoft Proxy Server running on the same computer as the Web server.
No application support is needed. The WinSock Proxy service provides Windows NT Challenge/Response authentication (a secure, encrypted logon process) whether or not the client application supports it. You can use Windows NT Challenge/Response authentication between WinSock Proxy clients and the WinSock Proxy service to avoid sending passwords across the internal network. Once authentication is done, the WinSock Proxy service uses the logon user name to verify that the user has permission to do the network operations attempted by the application.
Authentication for an application is done one time only, when the application first links to Windows Sockets. Use of the WinSock Proxy client dynamic-link library (DLL). This avoids the overhead of authentication on each network connection. Authentication is done between the WinSock Proxy service and the WinSock Proxy client DLL on the internal computer, regardless of whether the internal application will be initiating outbound connections to the Internet or receiving inbound connections from the Internet. This means that special support on external (Internet) computers is not needed.
The WinSock Proxy service offers client and server support for most standard and custom Internet applications that communicate by using Windows Sockets. Almost all Windows Sockets 1.1 TCP/IP applications can be redirected.
Access is controlled by port number, protocol, and user or group. Each port can be enabled or disabled for communications by a specific list of users or user groups. The list of users allowed to initiate outbound connections on a port can be a different list than the list of users allowed to listen for inbound connections on the same port. Access for TCP protocols is controlled separately from User Datagram Protocol (UDP) protocols.
You can restrict access to remote Web sites by domain name, IP address, and subnet mask. You can choose to grant access to all Web sites except those listed, or deny access to all Web sites except those listed. The settings are global and affect all users who access the Internet through the Microsoft Proxy Server.
Routing from the Internet to the private network is never allowed. (If your private network runs TCP/IP, the server’s Enable IP Routing check box in the Network application should not be selected. Clear this check box to prevent unauthorized IP packets from infiltrating your network. The Enable IP Routing check box is located in the Advanced Microsoft TCP/IP Configuration dialog box. You can find this dialog box by running the Network application in Control Panel.)
All requests to the Internet are done with the gateway server’s Internet IP address as the source address. This hides internal IP addresses, and allows use of unregistered or private (net 10) addresses.
Each log entry contains the user name of the client and all request information including the time and date of the request, and the size of the requested objects. A new log can be created periodically. This can be daily, weekly, monthly, or when the file size reaches a preset size. The log can be maintained in a text file or in an ODBC-supported database (such as Microsoft SQL Server).
The application running on the private network must be a 16-bit or 32-bit Windows Sockets version 1.1 application running on a computer running Windows 3.1, Windows For Workgroups 3.11, Windows 95, or Windows NT. The application running on the external (Internet) network can be any TCP/IP-based application on any common operating system (such as Windows, UNIX, or Apple Macintosh).
The WinSock Proxy service is administered by using Internet Service Manager, the administrative tool that is installed as part of Microsoft Internet Information Server. Property sheets for the WinSock Proxy service provide a simple, intuitive administrative interface. You can use Internet Service Manager to manage both local and remote computers running Microsoft Proxy Server.
© 1996 by Microsoft Corporation. All rights reserved.