Overview of Web Proxy Service Configuration
Setting Up Web Proxy Users
Controlling Web Proxy User Access to Internet Sites
Setting Up Caching of Internet Objects
Logging Web Proxy Service Activity
After you have installed Microsoft Proxy Server, you will usually perform the following steps to configure the Web Proxy service:
These steps are described in this chapter.
Selecting the Client Authentication Method
Granting Permissions to Proxy Users
There are three types of client authentication methods that can be used by the Web Proxy service:
For a discussion of each of these authentication methods, see “Security.”
The client authentication method used by the Web Proxy service is actually set in the WWW service of Microsoft Internet Information Server (IIS).
In Internet Service Manager, double-click the server name next to the WWW service.
The WWW Service Properties dialog box appears. Make sure that the Service tab is selected.
Under Password Authentication, select one or more authentication methods.
Windows NT Challenge/Response
Click OK.
This procedure sets the authentication method for one server. If your network has more than one server running the Web Proxy service, repeat the procedure for each server.
For more information about the client authentication methods, see “Security.” Also see your documentation for Microsoft Internet Information Server.
When Microsoft Proxy Server is first installed, by default there are no Proxy permissions granted.
If you have enabled Anonymous authentication in the WWW service, all users (on the private network) will have access and you do not need to grant Proxy permissions.
Note Users will not be able to gain access to the Msp\Clients share folder before Proxy permissions are granted.
Proxy Permissions determine which users or groups of users can access the Internet by using a particular protocol through the Web Proxy service on a server. Permissions are granted separately for each protocol. The available Web Proxy service protocols are:
FTP Read File Transfer Protocol. Use this protocol to download files through your browser.
Gopher Access through your browser to links and files on Gopher servers.
WWW HTTP and HTTPS (secure HTTP) protocols for the World Wide Web. Use WWW for browser access to the Web.
Secure Allows various Secure Socket Layer (SSL) connections. By default this includes SNEWS, but other protocols can be configured using the Windows NT registry.
Before assigning Proxy permissions, it is a good idea to use User Manager for Domains to create user groups containing the user accounts of users who need access to a particular protocol or sets of protocols. Then you can apply permissions to groups, rather than to individual users. For more information about user groups and about User Manager for Domains, see “Server Administration.” Also see your documentation for Windows NT.
From Internet Service Manager, double-click the server name next to the Web Proxy service.
From the Web Proxy Service Properties window, click the Permissions tab.
Select the Enable Access Control check box.
When the Enable Access Control check box is selected, Web Proxy service security is enabled. When this check box is cleared, the Web Proxy service will not attempt to validate connections from clients.
Note The authentication options used by the Web Proxy service (anonymous, basic, and Windows NT challenge/response) are set in the WWW service of Internet Information Server.
Review the current permissions. Select a protocol from the Protocol box and review the users and groups granted the right to use that protocol to access the Internet through the Web Proxy service on this server.
When you select a protocol from the Protocol list, the Grant Access To box displays the users and groups that are already granted permissions for that protocol.
To grant a user or group the right to use a protocol to access the Internet through the Web Proxy service on this server, select the protocol from the list in the Protocol box, choose Add, and complete the Add Users and Groups dialog box that appears.
To remove a user or group from the list of those granted the right use a protocol to access the Internet through the Web Proxy service on the server, select the protocol from the Protocol box, select the user or group from the box below, and choose Remove.
When permissions are set appropriately for the selected protocol, select another protocol from the list, and grant or remove permissions as necessary.
When all protocols have their permissions set appropriately, click OK.
This procedure sets permissions for one server. If your network has more than one server running the Web Proxy service, repeat the procedure for each server.
You can allow or prevent client access to specific Internet sites. This is called filtering, and it is accomplished on per-server basis. It applies to all users who access the Internet using either service (Web Proxy or WinSock Proxy) on that server.
You can allow or prevent access to a single computer, a group of computers, or an Internet domain. You can control access by IP address, subnet mask, and domain name.
In Internet Service Manager, open the Web Proxy Service Properties window for the server to be administered, and click the Filters tab.
Select the Enable Filtering option.
Select the filtering mode. You set an overall policy first, then specify exceptions to that policy.
To deny users access to specific Internet sites, first select Granted.
To deny users access to specific Internet sites, add those sites to the Except to those listed below list. Users will be allowed access to all other Internet sites.
To allow access to specific Internet sites, first select Denied.
To allow users access to specific Internet sites, add those sites to the Except to those listed below list. Users will be denied access to all other Internet sites.
To create a new filter, click Add and complete the dialog box that appears.
Select Single Computer to filter a single computer. If you select this option, you must also enter that computer’s IP address in the IP Address box.
Select Group of Computers to filter a group of computers. If you select this option you must enter an IP address in the IP Address box, and a subnet mask in the Subnet Mask box.
Select Domain to filter a domain. If you select this option, enter a domain name in the Domain box.
When you have completed dialog box, click OK. The Filters property sheet returns, with the new filter added to the Except to those listed below list.
Repeat step 4 until all needed filters are defined for this server.
To alter a listed filter, select it from the list, click Edit, and modify the settings in the dialog box that appears.
To remove a filter from the list, select the item and click Remove.
Click OK.
Note Only the selected mode, Granted or Denied, is in effect. When you switch between modes, filters created for the deselected mode are retained, but are not in effect.
This procedure sets up filtering for one server. If your network has more than one server running Microsoft Proxy Server, repeat the procedure for each server.
Basic Cache Configuration
Setting the Advanced Options for the Cache
Changing the Drives and Space Allocated to the Cache
Turning Off the Cache
Cache-Only Implementation
From Internet Service Manager, open the Web Proxy Service Properties window for the server to be administered, and click the Caching tab.
Make sure the Enable Caching check box is selected.
Use the Cache Expiration Policy to set the freshness of objects in the cache. Move the slider toward Always Request Updates to maintain the freshest cache data and increase the amount of Internet traffic that the server generates. Move the slider toward Fewest Internet Requests to allow objects in the cache to be used for the maximum Time-To-Live (TTL), which reduces Internet traffic.
Freshness is a measure of how long a local copy of an object in the cache is used in place of the remote object from the original Web site. TTL is the time in seconds that an object remains in the cache before reaches its expiration. At that time the object will no longer be used in place of the original object on an Internet site (in the case of passive caching) or be updated by Microsoft Proxy Server (in the case of active caching). To generate the least number of Internet requests, move the slider all the way to the right (to Fewest Internet Requests).
Set the Enable Active Caching option.
Active caching uses the cache to proactively ensure the freshness and availability of certain HTTP data. The cache manager creates its own request for an object, without client prompting, when the TTL has expired or is near expiration. Web objects are subject to active caching on the basis of their popularity relative to their rate of change. Additionally, the active caching algorithm incorporates calculations of current server load in order to process requests to the Internet at times of low usage.
If this option is selected, active caching is enabled. If cleared, active caching is disabled and only passive caching is performed.
If you enable active caching, use the Active Caching Policy slider to specify how frequently objects in the cache are updated. Set the slider toward Most client cache hits to update the cache frequently. Set the slider toward Fewest Internet Requests to minimize the number of times Microsoft Proxy Server makes requests to Internet sites to update objects in the cache.
Review the cache space allocation shown in Total Cache. To change the drives and the amount of disk space allocated to the cache, click the Change Cache Size button and complete the Microsoft Proxy Server Cache Drives dialog box. For more information, see Changing the Drives and Space Allocated to the Cache, later in this chapter.
To specify a maximum size allowed for cached objects, filter cache objects, or return expired objects from the cache when the requested Internet site is unavailable and the cache does not contain an unexpired copy of the requested object, click the Advanced button and complete the Advanced Cache Policy dialog box. For more information see Setting the Advanced Options for the Cache, later in this chapter.
When the cache is configured appropriately for this server, click OK.
This procedure sets up caching for one server. If your network has more than one server running the Web Proxy service, repeat the procedure for each server.
Note The cache cannot be administered during service startup. Each time the Web Proxy service starts, the cache performs an integrity check and other tests. The duration of these startup checks depends on the size of the cache, the number of objects in the cache, and other variables.
In some situations it is possible to start Internet Service Manager, open the Web Proxy Service Properties window, and select the Caching tab before the cache has finished its startup checks. When this occurs an error message will be displayed and you will be unable to administer cache parameters. You can select other Web Proxy service property sheets (such as those for the Service, Permissions, Logging, and Filters) and administer their parameters. However, to administer the cache parameters you will need to close the Web Proxy Service Properties window, return to the main Microsoft Internet Service Manager window, wait until the cache has completed its startup checks, reopen the Web Proxy Service Properties window, and click the Caching tab.
You can use the advanced options to specify a maximum size allowed for cached objects, filter cache objects, or return expired objects from the cache when the requested Internet site is unavailable and the cache does not contain an unexpired copy of the requested object.
In Internet Service Manager, open the Web Proxy Service Properties window for the server to be administered, and click the Caching tab. The Microsoft Proxy Server Cache Drives property sheet appears.
Click the Advanced button. The Advanced Cache Policy dialog box appears.
To limit the size of cached objects, select the Limit Size of Cached Objects to check box and type a value (in kilobytes) in the adjacent KB box. Objects larger than the specified size will not be cached.
Note that 0 is not a valid value. If you enter 0 (or if you do not enter a value), when you click OK to exit this dialog box the Limit Size of Cached Objects to check box will be cleared.
By default, this box is cleared and there is no limit to the size of a cached object.
To specify that cached objects will be sent to the client when the object is in the cache and the Internet server is unavailable, select the Return expired objects when site is unavailable check box. Objects in the cache will be used even if they are expired. By default, this option is selected.
If you clear this option, when the Internet server is unavailable and the object in the cache is expired, the expired cached object will not be returned to the client.
Review and if necessary modify the Cache Filters list, which contains the currently configured cache filters. The URL column displays the URL that will be filtered, and the Status column shows whether that URL will always be cached or will never be cached.
To remove a filter, select it from the Cache Filters list and click Remove.
For information about completing the Cache Filters Properties dialog box, see the procedure that follows.
When the advanced options are set appropriately, click OK in the Advanced Cache Policy dialog box, and when the Caching property sheet reappears, click OK again.
Usually, Microsoft Proxy Server determines which Internet objects will be cached. Optionally, you can create cache filters, which specify URLs that will always be cached or will never be cached.
When a URL is configured to never be cached, its objects will not be stored in the cache. When a URL is configured to always be cached, objects from that URL will be selected for caching (subject to other caching rules). This can be useful if, for example, you want to specify a wildcard filter to deny caching of all Internet objects from a specific site, and then create another filter to re-enable caching of objects from a particular sub-tree of that site.
Open the Cache Filter Properties dialog box, as described in the previous procedure.
In the URL box, type the URL that will be filtered.
For information about URL filter syntax, see the discussion following this procedure.
Select Always cache or Never cache.
Select Always cache to always cache Internet objects returned from the URL listed in the URL box. Use this option when you have already specified a wildcard filter to deny caching of all Internet objects from a site, and want to re-enable caching of objects from a particular sub-tree of the site.
Select Never cache to prevent caching of Internet objects returned from the URL entered in the URL box. This is the default selection.
When the filter is configured appropriately, click OK. The Advanced Cache Policy dialog box returns.
When creating a filter, type the URL using one of the following formats. Note the use of the asterisk (*) wildcard character.
For example, www.microsoft.com/intdev specifies only the intdev page.
For example, www.microsoft.com/intdev* specifies the intdev page and all pages below.
For example, *.mydomain.com/beta specifies www.mydomain.com/beta, ftp.mydomain.com/beta, gopher.mydomain.com/beta, and so on.
For example, *.mydomain.com/* specifies all pages in mydomain.com.
You must include at least one forward slash (/) in the URL.
The cache should always be located on one or more hard drives installed on the computer running Microsoft Proxy Server. (You cannot use network drives to store cached data.) You should choose a hard disk of sufficient size to make the cache as large as possible. Using multiple drives is a good idea, because breaking a very large cache into several smaller caches can sometimes provide faster access to objects. To help prevent a disk from filling up, it is a good idea to store the logs and the cache on different volumes.
When configuring the cache drives you must, at a minimum, allocate at least one drive and 5 MB for caching. However, the recommended minimum allocation is higher. It is suggested you allocate at least 100 MB plus 0.5 MB for each Web Proxy service client (and round up to the nearest full megabyte). For example, if a server will be servicing 79 Web Proxy service clients, it is recommended you allocate 140 MB or more to the cache. For each server the optimal cache allocation will vary depending on load and configuration, but in general, increasing the disk space allocation benefits the cache.
Allocate space from a drive to the cache in increments of 5 MB. If you assign a number to the cache that cannot be evenly divided by 5, the allocation is rounded down to the next lowest 5-MB increment. For example, if you assign 194 MB to the C: drive, 190 MB is actually allocated from that drive to the cache.
Note It is strongly recommended that you use only NTFS volumes for caching. Also, do not assign a read-only drive (for example, a CD-ROM drive) to the cache.
From Internet Service Manager, open the Web Proxy Service Properties window for the server to be administered, and click the Caching tab. The Microsoft Proxy Server Cache Drives dialog box appears.
Review the existing drive and cache size configurations.
The list under Drive displays all the local drives installed on the server, identified by drive letter and file system type.
If a drive is configured to cache, the amount of allocated space is shown in the Maximum Size (MB) column. If a drive is not configured to cache, this column is empty.
The total disk space, in megabytes, allocated to the cache is shown at the bottom of the dialog box, in Total Cache Size for All Drives (MB). This value is the sum of all entries in the Maximum Size (MB) column.
To store cached data on a drive, select the drive from the list, type a number in the Maximum Size (MB) box, and click Set.
The number you type will become the maximum amount of space, in megabytes, that the cache can use on that drive. The number you type must be less than the value shown next to Space Available (MB).
To stop storing cached data on a drive, select the drive from the list, type 0 in the Maximum Size (MB) box, and click Set.
All cached data on that drive will be lost.
To change the amount of space allocated from a drive to the cache, select the drive from the list, type a new value in the Maximum Size (MB) box, and click Set.
If you modify an existing cache drive and reduce the Maximum Size (MB) value, some cached data on that drive might be lost.
If you increase the Cache Size (MB) value, the new setting takes effect immediately. There is no effect on the data already cached on that drive.
When
the drives and space allocations are set appropriately,
click OK in the Microsoft Proxy
Server Cache Drives dialog box, and when the Caching
property sheet reappears, click OK
again.
Some users may be more interested in using Microsoft Proxy Server for its powerful caching features than for its security functions. Typical examples include Internet Service Providers (ISPs) and customers who already have other firewalls in place to screen HTTP traffic.
In these situations, Microsoft Proxy Server can be configured to use any or all of its network adapter cards both for requests from clients and for requests to the Internet. In this scenario, client computers would connect to Microsoft Proxy Server, Microsoft Proxy Server would connect to a router or firewall, and through it to the Internet.
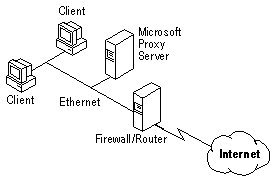
To configure this scenario, the Local Address Table (LAT) for Microsoft Proxy Server must include all IP addresses and subnets that will be allowed to use the Web Proxy service cache. If inbound client requests are permitted, then the LAT should have the address range from 0.0.0.0 to 255.255.255.255.
Microsoft Proxy Server can log information about all Internet requests made by Web Proxy service clients. It can log to a text file or to a table in an ODBC-compliant database (such as Microsoft Access or Microsoft SQL Server).
By default, Web Proxy service information is logged to a text file. After installing Microsoft Proxy Server, you can set the configuration parameters for text file logging, or you can set up logging to an ODBC-compliant database.
From Internet Service Manager, open the Web Proxy Service Properties window for the server to be administered, and click the Logging tab.
Make sure the Enable Logging option is selected.
Select either Regular Logging or Verbose Logging.
Regular Logging records only a subset of all available information for each Internet access. This option reduces the disk space needed for a log file. Verbose Logging records all available information for each Internet access.
Make sure the Log to File option is selected.
Select or clear the Automatically open new log option.
Select this option to periodically create a new Web Proxy service log file, using the interval specified by the Daily, Weekly, Monthly, or When File Size Reaches options. When a new log file is started, the old log file is closed (and can be archived on other storage media).
Clear this option to use the same Proxy log file continuously.
If you select the Automatically open new log option, specify the interval used to open a new log file. Select Daily, Weekly, Monthly, or When File Size Reaches. If you select When File Size Reaches, also enter a value in the MB box.
Review and if appropriate change the log file directory.
To change this location, type a new path in the Log File Directory box, or click Browse and complete the dialog box that appears. It is possible to log to a local or remote drive, but in general it is recommended that you store your Proxy log file on a local disk.
Note To help prevent the disk from filling up, it is a good idea to store the logs and the cache on different volumes.
Click OK.
The log settings are saved.
For more information about logging to a text file, including detailed information about the data that is logged and the difference between regular and verbose logging, see “Monitoring.”
The following procedure shows you the basic steps you will perform to log Web Proxy service information to an ODBC-compliant database. For detailed instructions about how to accomplish each of these steps, see “Monitoring.”
Install the database.
The database can be installed on the local computer or a remote computer.
Create a table in the database, creating the fields necessary to support Web Proxy service log data.
The required fields are described in detail in “Monitoring.”
Install the ODBC driver for the database you are using.
Create a System Data Source Name (system DSN) for the database that will receive the logging.
In Internet Service Manager, open the Logging tab of the Web Proxy Service Properties window. Make sure the Enable Logging option is selected, select the Log to SQL/ODBC Database option, and configure the logging options.
Detailed instructions are provided in “Monitoring.”
Tip Turn off Internet Information Server (IIS) logging when Web Proxy service logging is enabled. The IIS log is a subset of the information stored in the Web Proxy service log. Since the information is duplicated, you can improve performance by turning off IIS logging. To turn off IIS logging, use Internet Service Manager to open the Logging property sheet for the WWW service. Clear the Enable Logging check box.
© 1996 by Microsoft Corporation. All rights reserved.