Multiple Security Protocols
Windows NT supports multiple network security protocols because each protocol provides either compatibility for existing clients, stronger, more effective security mechanisms, or interoperability features for heterogeneous networks like the Internet. There are many authentication protocols in use today in corporate networks, (perhaps more than we would all like to see), and the Windows NT architecture does not limit what protocols can be supported. One security protocol to fit all needs would be simpler, but network configurations from small office networks to large-scale Internet Content Providers do not share the same security requirements. Customers need to have choices for how to integrate new security technology, such as dynamic passwords or public-key cryptography into their computing environment.
Windows NT is designed to support multiple security protocols, which is essential for today's distributed computing environment. Using general purpose Win32® security, APIs supported by applications are isolated from the details of different security protocols available. Higher-level application interfaces provided by Authenticated RPC and DCOM provide abstractions to use security services based on interface parameters.
The next version of the Windows NT security infrastructure will support three primary security protocols:
- Windows NT LAN Manager (NTLM) authentication protocol is used by Windows NT 4.0 and previous versions of Windows NT. NTLM will continue to be supported and used for pass-through network authentication, remote file access, and authenticated RPC connections to earlier versions of Windows NT.
- The Kerberos Version 5 authentication protocol replaces NTLM as the primary security protocol for access to resources within or across Windows NT Domains. The Kerberos authentication protocol is a mature industry standard that has advantages for Windows NT network authentication. Some of the benefits of Kerberos protocol are mutual authentication of both client and server, reduced server load during connection establishment, and support for delegation of authorization from clients to servers through the use of proxy mechanisms.
- Distributed Password Authentication (DPA) is the shared secret authentication protocol used by some of the largest Internet membership organizations, such as MSN™ and CompuServe. This authentication protocol is part of Microsoft's Membership System and is specifically designed for users to use the same Internet membership password to connect to any number of Internet sites that are part of the same membership organization. The Internet content servers use the Microsoft Membership System authentication service as a backend Internet service, and users can connect to multiple sites without re-entering their password.
- Public-key-based protocols provide privacy and reliability over the Internet. SSL is the de facto standard today for connections between Internet Browsers and Internet Information Servers. (An IETF standard protocol definition based on SSL3 is forthcoming and is currently known as the Transport Layer Security Protocol [TLS]) These protocols use public-key certificates to authenticate clients and servers and depend on a public-key infrastructure for wide-spread use. Windows NT 4.0 provides secure channel security services that implement the SSL/PCT protocols. The next version of Windows NT security will have more enhanced feature support for public-key protocols that are described a later.
Enterprise security depends on having the flexibility to use the right security mechanisms where necessary. Enterprise computing will continue to depend on a wide range of network services provided by remote file and print servers, business application and data servers, and data warehouse and transaction processing environments. Support for multiple network security protocols allows Windows NT Workstation and Windows NT Server to host a variety of network services, in addition to Internet-based technologies.
The following diagram shows the architecture support for multiple security protocols implemented in Windows NT using the Security Support Provider Interface (SSPI).
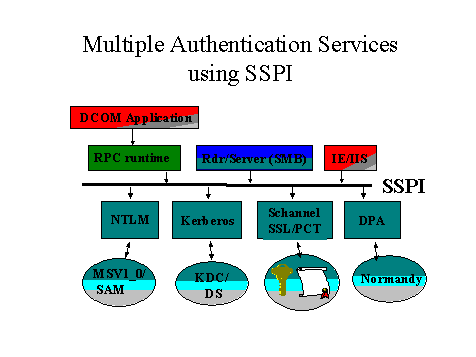
Figure 4. Architecture for Multiple Authentication Services
The Security Support Provider Interface is a Win32 system API used by many applications and system services, such as Microsoft Internet Explorer (IE) and Internet Information Server (IIS) to isolate application-level protocols from security protocols used for network authentication. Security providers use different credentials to authenticate the user, either shared-secret or public-key certificates. The security protocols interact with different authentication services and account information stores.
- NTLM security provider uses the "MSV1_0" authentication service and NetLogon service on a Domain Controller for client authentication and authorization information.
- The Kerberos security provider connects to an online Key Distribution Center (KDC) and the Directory Service account store for session tickets.
- DPA uses the Microsoft Membership System security services for membership authentication and server-specific access information.
- Secure channel services are based on public-key certificates issued by trusted Certificate Authorities—they do not require an online authentication server.

