Secure Socket Layer (SSL) and Private Communication Technology (PCT) are public-key-based security protocols implemented by the Secure Channel (Schannel) security provider. These security protocols are used today by Internet browsers and servers for mutual authentication, message integrity, and confidentiality. Authentication of the Internet server is performed by Internet Explorer (the client) when the server's certificate is presented as part of the SSL/PCT secure channel establishment. The client program accepts the server's certificate by verifying the cryptographic signatures on the certificate, and any intermediate CA certificates, to a one of a few known or configured root CAs.
Client authentication is also supported by SSL 3.0 and PCT 1.0. Client authentication using public-key certificates is completed as part of the secure channel session establishment.
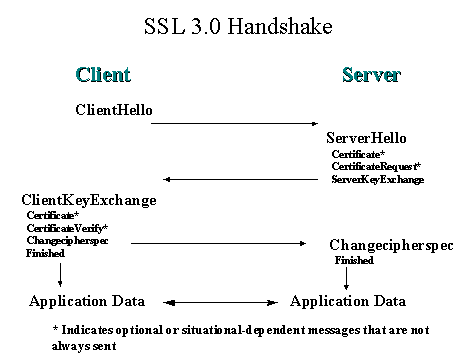
The diagram below shows the SSL 3.0 handshake messages between the client and server for secure connection establishment.

Figure 7: SSL 3.0 Handshake
Authentication of the client by the server is accomplished by the same process as server authentication. The server verifies the cryptographic signatures on the client's certificate, and any intermediate CA certificates to a known or trusted root CA. However, once the identity of the client is verified through certificate verification (client authentication), the application server needs to establish a security context with appropriate access rights defined for the client. The access control information determines what resources the client is allowed to use on this server. In the Windows NT security architecture, access control is defined by the group memberships and privileges in the security access token.
Public-key client authentication uses the information in the client's certificate to map to local access control information. This mapping determines what authorization the client has to access resources on the server system. Initial support for client authentication by Microsoft's Internet Information Server (IIS) will be available by managing an authorization database to map certificate subject or issuer information to existing Windows NT accounts. The authorization database can be as simple or complicated as needed to meet the application requirements.
The next release of Windows NT will provide broader support for client authentication by implementing a security service that uses the Windows NT Directory Service to map certificate information to existing Windows NT accounts. The mapping can be performed using a lookup of the certificate subject name in the Windows NT Directory, or searching for directory properties that identify the client certificate.
Windows NT support for client authentication integrates public-key certificates with the Windows NT security architecture. No separate database is required to define the access rights associated with public-key certificates. The access control information is maintained by the group membership stored in the Windows NT Directory. Common Windows NT Directory Service administration tools are used for granting access rights by adding Windows NT users to groups.