Glossary
The IME module on Windows fits into a larger mechanism for passing user input to applications, and this section briefly describes this overall framework. Unless you are writing an IME package or customizing your IME user interface, you don't need to worry about the details behind the other components.
On Windows NT, the Input Method Profiler (IMP) stores information about each IME, such as whether it is currently active. Control Panel calls the IMP API to add, delete, or activate an individual IME. To get an idea of what kind of information the IMP handles, click the IME icon in the Windows NT 3.5 Control Panel. When the user changes the active IME via Control Panel, the IMP sends a WM_IME_REPORT message to all applications, with wParam set to IR_IMESELECT. More than one IME can be installed on the system, although on Windows NT 3.5 only one can be active at a time.
On Windows 95, multiple IMEs are handled by the multilingual API instead of by an Input Method Profiler. (See Chapter 6 for a description of the multilingual API.) Windows stores information about each IME installed on the system in the system registry (in the H_KEY_CURRENT_USER\Control Panel\Input Method section). The user switches IMEs the same way the user switches Western keyboard layouts—by clicking the input language menu on the taskbar or by entering a shortcut-key combination. The change is reflected on the taskbar indicator:
![]()
Switching IMEs generates the same messages as switching other keyboard layouts: WM_INPUTLANGCHANGEREQUEST and WM_INPUTLANGCHANGE. Applications can activate specific IMEs by calling ActivateKeyboardLayout.
The IMM manages communication between IMEs and applications, serving as the go-between. On Windows NT 3.5, the IMM API is called almost exclusively by the system. Applications can call two IMM functions: WINNLSEnableIME, which enables or disables an IME, and WINNLSGetEnableStatus, which returns the enabled or disabled status set by WINNLSEnableIME. On Windows 95, applications can call a number of IMM API functions in order to customize the IME user interface, as described in the section titled "Customized IME Support on Windows 95".
In concept, Input Method Editors are the same as keyboard drivers, but IMEs handle more characters, and Far East systems require some extra code to handle them. On Windows 95, the Input Method Manager is an extension of USER.EXE. Figure 7-17 below illustrates the way in which the IME, the application, and the rest of the system on Windows 95 communicate.
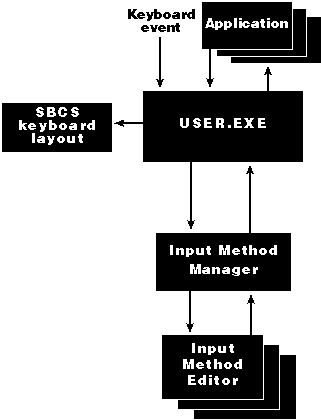
Figure 7-17 Communication between the IME, the application, and the rest of the Windows 95 system.
When the IME program is active, it traps all keyboard events, including the virtual keys listed in Figure 7-18 below. You can see how some of these virtual-key codes correspond to the IME states listed in Figure 7-6 and Figure 7-10. Unless you are writing an IME package or bypassing the IME module to create your own application-specific input mechanism (definitely not recommended!), you don't need to worry about adding code to respond to these virtual keys.
| Virtual Key | Description |
| VK_DBE_ALPHANUMERIC | Changes the mode to alphanumeric |
| VK_DBE_KATAKANA | Changes the mode to katakana |
| VK_DBE_HIRAGANA | Changes the mode to hiragana |
| VK_DBE_SBCSCHAR | Changes the mode to single-byte characters |
| VK_DBE_DBCSCHAR | Changes the mode to double-byte characters |
| VK_DBE_ROMAN | Changes the mode to Roman characters |
| VK_DBE_NOROMAN | Changes the mode to non-Roman characters |
| VK_DBE_CODEINPUT | Changes the mode to code input |
| VK_DBE_NOCODEINPUT | Changes the mode to non-code input |
| VK_DBE_ENTERIMECONFIGMODE | Activates a dialog box for setting up an IME environment |
| VK_DBE_ENTERWORDREGISTERMODE | Activates the word registration dialog box |
| VK_DBE_FLUSHSTRING | Deletes the undetermined string without determining it |
| VK_HANGEUL | Changes the mode to hangul |
| VK_HANJA | Changes the mode to hanja |
| VK_JUNJA | Changes the mode to junja |
| VK_PROCESSKEY (Windows 95) | Tells the application that the IME has processed a virtual key; to retrieve the value of the virtual key, applications can call ImmGetVirtualKey |
Figure 7-18 IME virtual keys.