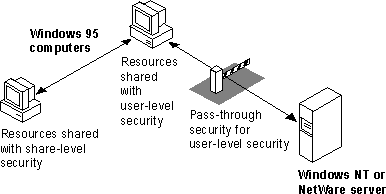
For File and Printer Sharing for Microsoft Networks (but not NetWare), Windows 95 supports share-level security similar to the security provided with Windows for Workgroups. This level of security associates a password with a shared disk directory or printer. Share-level security for peer resource sharing can be implemented in a Windows 95-only peer-to-peer network or on a network supported by Windows NT or other Microsoft Windows network-compatible servers.
For File and Printer Sharing services on both Windows NT and NetWare networks, Windows 95 supports user-level security by linking a peer server directly to another server for user account validation. For network administrators, the user account list is centrally controlled at the Windows NT domain controller or NetWare server; on a Windows NT network, the user account list on a single server can also be used for validation. The resources on the Windows 95 peer server can be accessed only by users with accounts in the central database. Users can also be assigned specified access rights in Windows 95 for particular resources. For information about using and managing security, see Chapter 14, "Security."

The 32-bit, protected mode network client and the File and Printer Sharing service are separate network processes, but they share connection information and pass requests to each other when validating a user-level security request.
For user-level security on a computer running either version of File and Printer Sharing service, you specify the server that contains the database of user accounts that are allowed to connect to this peer resource sharing server. You can do the following to customize access to a shared resource:
When a user requests access to a shared resource under user-level security, Windows 95 checks for the user's logon name against the list of user accounts maintained on the server. If this is a valid user logon name, Windows 95 then checks whether this user has access privileges for this resource. If the user has access privileges, then the requested operation is allowed.
For an example of how pass-through validation works with peer resource sharing, see Chapter 14, "Security."