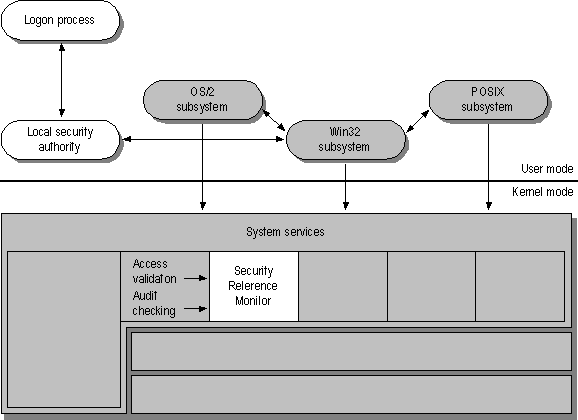
The Security Reference Monitor component plus two others — the Logon Process and Security protected subsystems — form the Windows NT security model. In a multitasking operating system such as Windows NT, applications share a variety of system resources including the computer's memory, I/O devices, files, and system processor(s). Windows NT includes a set of security components (shown in Figure 1.9) that ensure that applications cannot access these resources without authorization.

Figure 1.9 Windows NT Security Components
The Security Reference Monitor is responsible for enforcing the access-validation and audit-generation policy defined by the local Security subsystem. The Reference Monitor provides services to both kernel and user mode for validating access to objects, checking user privileges, and generating audit messages. The Reference Monitor, like other parts of the Executive, runs in kernel mode.
The user-mode Logon Process and Security protected subsystems are the other two components of the Windows NT security model. The Security subsystem is known as an integral subsystem rather than an environment subsystem because it affects the entire Windows NT operating system. (Environment subsystems are discussed later in this chapter.)
The Windows NT Kernel and Executive are based on an object-oriented model that allows for a consistent and uniform view of security, right down to the fundamental entities that make up the base operating system. This means that Windows NT uses the same routines for access validation and audit checks for all protected objects. That is, whether someone is trying to access a file on the disk or a process in memory, there is one component in the system that is required to perform access checks, regardless of the object type.
The Windows NT Logon Process provides for mandatory logon to identify users. Each user must have an account and must supply a password to access that account. Figure 1.10 illustrates the interaction among Windows NT components during logon.
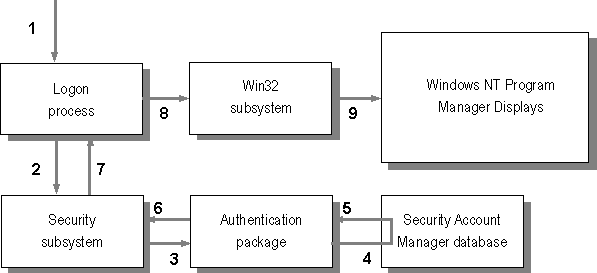
Figure 1.10 Logon Security Process
Before a user can access any resource on a Windows NT computer, they must logon through the Logon Process so that the Security subsystem can authenticate the person's username and password. After successful authentication, whenever the user tries to access a protected object, the Security Reference Monitor runs an access-validation routine against the user's security information to ensure the user has permission to access the object.
The security model also provides for discretionary access control so that the owner of a resource can specify which users or groups can access resources and what types of access they're allowed (such as read, write, and delete).
Resource protection is another feature provided by the security model. Tasks can't access each others' resources, such as memory, except through specific sharing mechanisms. This feature helps enforce object hiding.
Windows NT also provides for auditing so that administrators can keep an audit trail of which users perform what actions.
By providing these features, the Windows NT security model prevents applications from gaining unauthorized access to the resources of other applications or the operating system either intentionally or unintentionally.
For a complete description of how the security model works, see Chapter 2, "Windows NT Security Model."
In addition to the protected subsystems — Logon Process and Security — Windows NT includes a number of other user-mode components called environment subsystems. The next section describes each of the Windows NT environment subsystems.