As described earlier, you can track several categories of security events. This section provides examples for most of these categories. This set of examples does not constitute a strategy for using the auditing capabilities of Windows NT; they merely serve as an introduction to help you interpret these events when you enable auditing for your Windows NT system.
In this example, auditing is enabled as follows (assuming you are logged on as an administrator):
From File Manager, the user double-clicks the .TXT file (which is associated with Notepad) and then writes some data to the file, saves it, and closes the file.
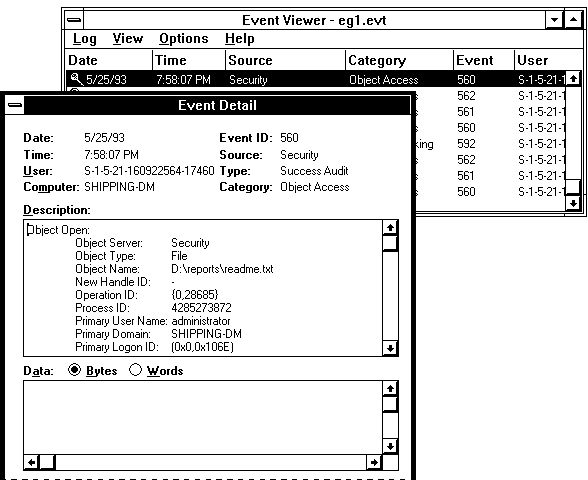
This results in audit events, as shown below:

From this view of the security log, you get a quick summary of security-related events that occurred. Double-click the first event to examine the details. (For example, details of this first event are shown in the Event Detail box.)
The data that needs to be interpreted is listed in the Description list box. The following table summarizes the audited events for this example, in the order they occurred.
Table 2.1 Security Events for File Access Example
Event ID and description | Analysis |
Event 560: Object Open | In this sequence of events, Windows NT is doing some internal checks, such as checking to see if the file exists and checking to see that there is no sharing violation. |
Event 592: A New Process Has Been Created | In this series of events, a new process is created for NOTEPAD.EXE. This process opens the .TXT file for reading. Next, the process allocates, then closes, a handle to the file. Note that from the security log it is clear that Notepad does not keep an open handle to the file; it simply keeps a copy of the file in memory. |
Event 560: Object Open | The process opens the file for reading and writing, and since the event is a successful audit, new data is written to the file. Next, the handle is allocated for the open file, then closed. |
Event 593: A Process Has Exited | This event indicates that the process, whose process ID relates to NOTEPAD.EXE, has ended. |
In this example, auditing is enabled by using User Manager to enable auditing for Success and Failure of Use of User Rights.
When the user tries to change the system time, only one event is generated, as shown below.
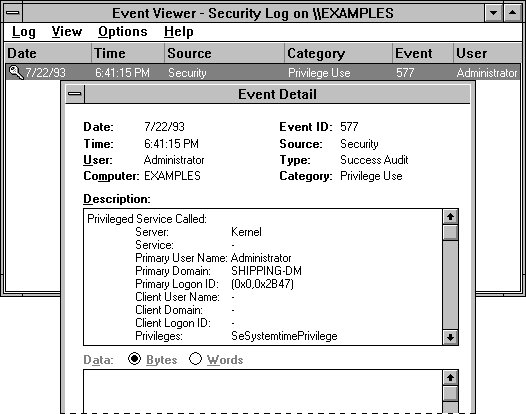
This event indicates that a privileged service was called and that a server component named Kernel has called an audit check on the primary username of the user. The audit type is a Success Audit, meaning that the user successfully exercised the right to use the SeSystemtimePrivilege (that is, the right to change the system time).
In this example, a new user account is added to the user accounts database. Auditing is enabled in User Manager by specifying both Success and Failure of User and Group Management. This generates four audit events, as shown below:
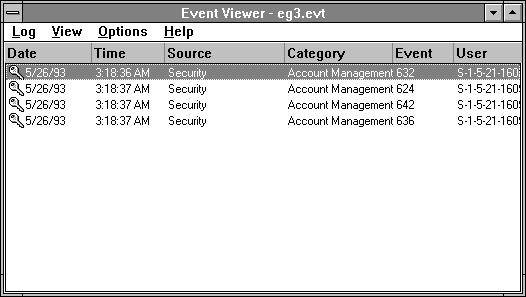
Table 2.2 Security Events for Added User Account
Event ID and description | Analysis |
Event 632: Global Group Member Added | A new security ID (member) is created and added to the group represented by the target account ID. This is a default global group Domain Users. At this point, the security ID does not have a username allocated to it. |
Event 642: User Account Changed | This event indicates that the account name of the security ID represented by the Target Account ID has been changed to the new user's. |
Event 636: Local Group Member Added | This event indicates that the account represented by the new user's security ID is created. The new user is added to the local group represented the security ID under Target Account ID (Users). |
In this example, auditing is enabled in User Manager for both Success and Failure of Restart, Shutdown and System.
In this example, seven events were generated. Note, however, that the number of events generated is related to the number of trusted systems that you start when the system is restarted. This number may vary if you replicate this scenario on your own Windows NT computer.
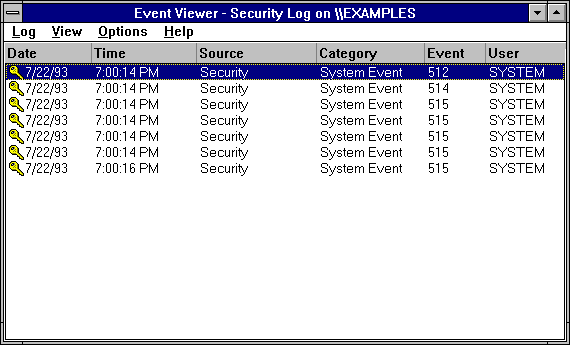
Table 2.3 Security Events for System Startup
Event ID and description | Analysis |
Event 512: Windows NT is starting up. | Identifies the date and time the system started. |
Event 514: Authentication package loaded | The description of this event says: An authentication package has been loaded by the Local Security Authority. This authentication package will be used to authenticate logon attempts. This is the standard authentication package shipped with Windows NT. |
Events 515: Trusted logon process | The description for each of these events says: A trusted logon process has registered with the Local Security Authority. This logon process will be trusted to submit logon requests. The logon process name is listed for each of these events, as follows: Winlogon Each of these events is a successful audit in the category of system event. These events indicate that the respective logon processes have registered themselves with the Local Security Authority and are now trusted to submit logon requests. |