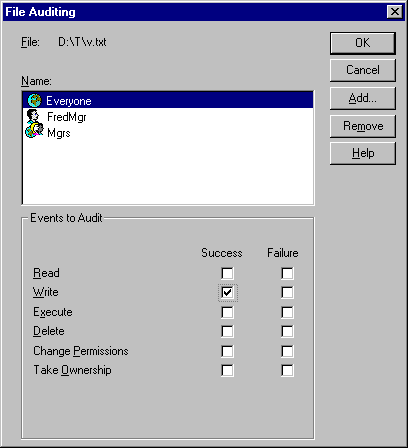
Windows NT has an audit determination process similar to its access determination process, described earlier in this chapter. After access determination, Windows NT evaluates the following information for possible auditing:
Each ACE in the audit ACL is evaluated as follows:
1. Windows NT checks to see if the type is SystemAudit. If not, the ACE is skipped.
2. Windows NT compares the identifier in the ACE to the set of identifiers representing the subject. If no match is found, the ACE is skipped.
3. The desired accesses are compared to the access mask specified in the ACE.
4. If none of the accesses specified in the ACE's mask were requested, the ACE is skipped. The SUCCESSFUL_ACCESS_ACE_FLAG and FAILED_ACCESS_ACE_FLAG flags of the ACE are compared to the final determination of whether access was granted or denied.
5. If access was granted but the SUCCESSFUL_ACCESS_ACE_FLAG flag is not set, or if access was denied but the FAILED_ACCESS_ACE_FLAG flag is not set, the ACE is skipped.
If Windows NT performs all of these steps successfully, an audit message is generated.
The following scenario illustrates this process. In this scenario, a system access ACL is being evaluated. Here, Write access to the file object is granted, and the SUCCESSFUL_ACCESS_ACE_FLAG is set in each ACE.

In this example, Windows NT evaluates the ACL by comparing the desired access mask with each ACE and processes the desired mask as follows:
1. Windows NT evaluates an ACE for SnrMgrs (of which FredMgr is a member). However, when the desired access is compared to the access mask of the ACE, no match is found, and the ACE is skipped.
2. Windows NT evaluates the ACE for FredMgr and finds a match.
3. Windows NT checks access flags and finds the SUCCESSFUL_ACCESS_ACE_FLAG is set. Processing stops, and an audit message is generated.