This section explains typical Internet scenarios with Windows NT Server .
The simplest way to connect to the Internet is as a client. As a client you use Internet Explorer or other tools to search for information.
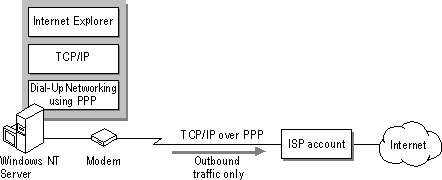
This configuration allows outbound traffic to the Internet only, as illustrated in Figure 2.2. (For more information about client connections to the Internet, see the Windows NT Workstation Resource Guide, Chapter 35, "Using Windows NT Workstation on the Internet.")

Figure 2.2 Windows NT as Internet client
In this scenario, the computer running Windows NT Server (or Windows NT Workstation) uses Dial-Up Networking and a modem to connect to an Internet service provider. After successful connection to the Internet service provider, the user can start and use any TCP/IP–based applications, such as Internet Explorer or the command-prompt FTP client.
For this type of scenario, you need to install and configure the following hardware or services:
Expanding the preceding configuration, you can create two-way communication with the Internet as illustrated in Figure 2.3.
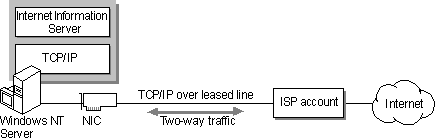
Figure 2.3 Windows NT Internet Information Server and client
In this scenario, the computer running Windows NT Server has a leased line to an Internet service provider. You install Internet Information Server and make information available to remote users on the Internet. In addition, the computer running Windows NT Server can use any TCP/IP–based applications, such as Internet Explorer or the command-prompt FTP client.
For this scenario, you need to install and configure the following hardware or services:
For more information about Internet servers, see Chapter 4, "Desktop Scenarios," and Chapter 5, "Enterprise Scenarios."
Note
Security becomes an important issue when you are connected to the Internet. This section describes only basic Internet scenarios. Many options that are not mentioned in this chapter exist to protect your computer or intranet from external intruders. For more information on security, see Chapter 3, "Server Security on the Internet."