Security Model Architecture
Figure 2.1 on the facing page shows the components of the Windows NT security model, which include:
- Logon processes, which accept logon requests from users. These include the initial interactive logon, which displays the initial logon dialog box to the user, and remote logon processes, which allow access by remote users to a Windows NT server process.
- Local Security Authority (LSA), which ensures that the user has permission to access the system. This component is the center of the Windows NT security subsystem. It generates access tokens, manages the local security policy, and provides interactive user authentication services. LSA also controls audit policy and logs the audit messages generated by the Security Reference Monitor.
- Security Account Manager (SAM), also known as the directory database, which maintains the user-accounts database. This database contains information for all user accounts and group accounts. SAM provides user validation services, which are used by LSA.
- Security Reference Monitor, which checks that the user has permission to access an object and perform whatever action the user is attempting. This component enforces the access validation and audit generation policy defined by LSA. It provides services to both kernel and user modes to ensure the users and processes attempting access to an object have the necessary permissions. This component also generates audit messages when appropriate.
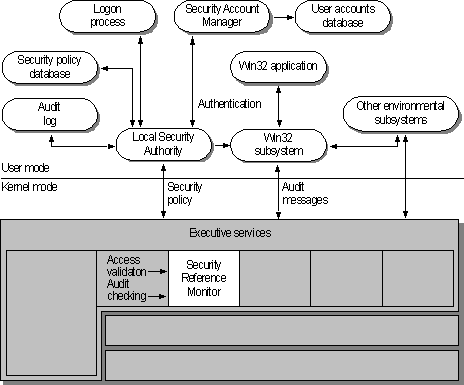
Figure 2.1 Windows NT Security Components
Together, these components are known as the security subsystem. This subsystem is called an integral subsystem, not an environmental subsystem, because it affects the entire Windows NT operating system.
The Windows NT security model is designed for C2-level security, as defined by the U.S. Department of Defense. Some of the most important requirements of C2-level security are:
- The owner of a resource (such as a file) must be able to control access to the resource.
- The operating system must protect objects so that they are not randomly reused by other processes.
For example, the system protects memory so that its contents cannot be read after it is freed by a process. When a file is deleted, users must not be able to access the data from that file.
- Each user must identify himself or herself by typing a unique logon name and password before being allowed access to the system. The system must be able to use this unique identification to track the activities of the user.
- System administrators must be able to audit security-related events. Access to this audit data must be limited to authorized administrators.
- The system must protect itself from external interference or tampering, such as modification of the running system or of system files stored on disk.
For more information about C2-level security, see "Security Considerations and C2 Security Rating," later in this chapter.

