Many enterprises today are connecting their private, internal networks to the Internet to provide access to external resources on the Internet. Although this is an important capability, it is one that must be well planned to avoid possible security risks by exposing the internal network to users outside the enterprise.
One common way to provide protection is to use a computer that is referred to as a firewall. A firewall is a computer or network device that allows only certain authorized operations or programs to be run between internal networks and the Internet.
A firewall configuration can be very simple or extremely complex depending on the particular requirements of the enterprise. This chapter is not designed to provide an exhaustive description of firewalls but will briefly discuss how the Microsoft DNS server can be used on a network that uses the services of a firewall to provide security for the network.
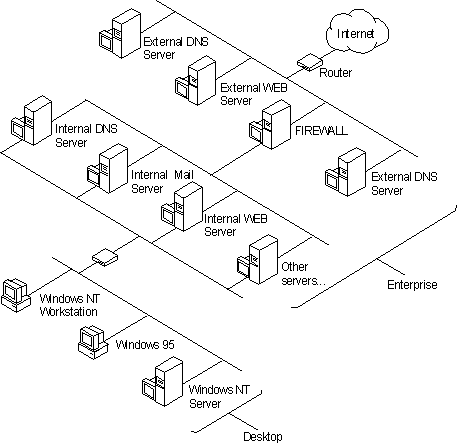
The following figure illustrates a typical network architecture that includes a multihomed computer running as an Internet firewall.

Figure 9.3 A Typical Network with a Firewall
As is illustrated in the Figure, the firewall protects the internal network from computers on the Internet that may attempt to access the internal network, while allowing computers on the internal network to access Internet resources. The example network design also includes computers that are configured as WWW and FTP servers that are external to the firewall.
The external servers allow computers from outside the internal network to access resources provided as public services, but these external servers must be closely monitored and secured because they are connected directly to the Internet network and do not use the firewall for access control. A router that is configured to control the type of packets allowed to pass through the router (referred to as packet filtering) can provide some additional access control.
The DNS services for the external and internal networks should be entirely isolated from one another to prevent computers outside the internal network from obtaining the names and IP addresses for resources located on the internal side of the firewall. This will help ensure that the only externally available information are the names and IP addresses of the external servers that are configured to provide external public services. These services include electronic mail, WWW, and FTP servers.
When internal network computers require access to computers outside the internal network, DNS name resolution typically requires interaction with DNS servers located on the public Internet. For this reason, you may want to allow only certain DNS servers to communicate outside the internal enterprise network. A DNS server that can communicate outside of the private network to resolve a DNS name query is referred to as forwarder.
After one or more DNS servers are designated as a forwarder, all other DNS servers on the internal network should be configured to use the forwarder for name resolution outside the internal network. The following figure illustrates this concept.
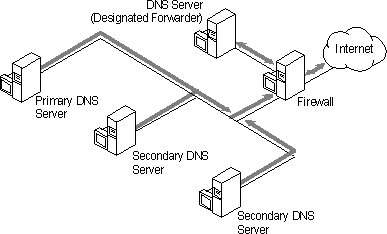
Figure 9.4 Using a DNS Forwarder and a Firewall
When a DNS server which is configured to use forwarders receives a DNS request that it is unable to resolve (through its own zone files), it passes the request to one of the designated forwarders. The forwarder then carries out whatever communication is necessary to resolve the request and returns the results to the requesting server, which, in turn, returns the results to the DNS client. If the forwarder is unable to resolve the query, the DNS server attempts to resolve the query on its own as normal.
To configure a Microsoft DNS server to use a forwarder
1. In DNS Manager, right-click the appropriate server icon, and then click Properties.
2. In the Server Properties dialog box, click the Forwarders tab and enter the IP address of the forwarder.