By John Sheesley
Is your Windows NT network safe from hackers? Are you doing everything possible to ensure that hackers can't access information from your network? Have you wondered how hackers learn how to access networks? In this article, we'll show you how to find out what hackers know about your network and where they learn it.
Before you can defeat hackers, you must first know what they know about your network. You feel secure because you think you've properly designed your security strategy. You've assigned everyone a password. You've assigned groups and given users access only to what they need. But it's a false sense of security. For almost every step you can take to make your network secure, hackers have found a way around it. Your best defense is to find out what they know, how they know it, and where they learned it. Once you know what they know, you can devise strategies to combat them.
As with most things related to computing today, much of the information that hackers obtain about networks comes from the Internet. You can easily find information about hacking Windows NT networks on Usenet or the World Wide Web.
Usenet contains public messages on topics ranging from the latest operating systems to news about Star Trek. So it comes as no surprise that some newsgroups in Usenet are dedicated to hackers. The format is very similar to the old-fashioned BBS systems where one person leaves a message that everyone can read and respond to.
Some of the newsgroups where you'll find information that hackers use include:
You can use the DejaNews search engine to search the newsgroups for posts about hacking Windows NT. The URL for DejaNews is http://www.dejanews.com.
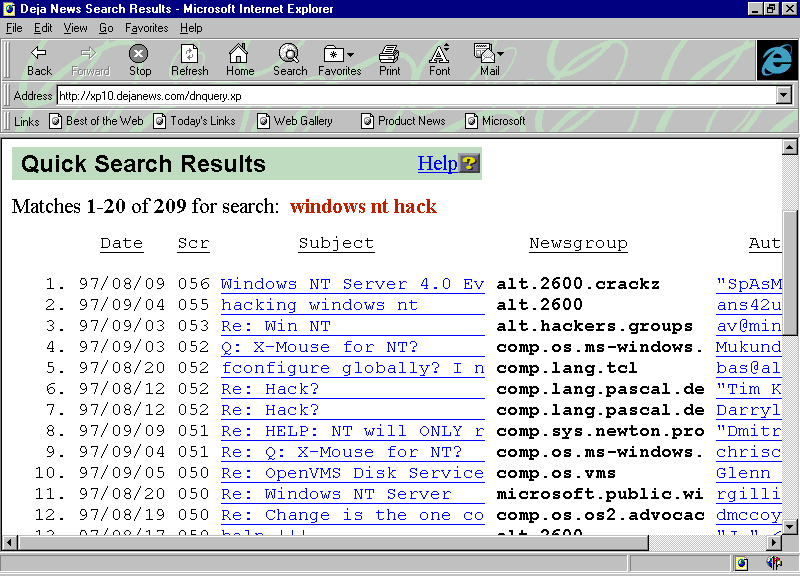
DejaNews is easy to use. Simply type in the words you want to search for and click Search. DejaNews searches through six to eight months' worth of posts to Usenet and returns all of the articles that contain those words. When we searched DejaNews using the keywords Windows NT and hack, it returned over 200 posts pertaining to hacking Windows NT, as shown in Figure A.
Figure A

We found over 200 Usenet posts about hacking Windows NT using DejaNews.
You can find other resources that hackers use to get information about attacking Windows NT networks on the World Wide Web. Finding Web sites dedicated to hacking is similar to trying to find and capture cockroaches. Just when you think you have one pinned down, you find that it has moved to another URL.
Your best bet is to use search engines, such as Yahoo! and AltaVista, to find those pages. Yahoo!'s URL is http://www.yahoo.com. AltaVista's URL is http://www.altavista.digital.com. When we searched AltaVista using the keywords hack and Windows NT, AltaVista returned 1,290 different Web sites with those keywords.
Unfortunately, or fortunately depending on your perspective, when we checked out many of the sites to judge the quality of information available, much of it was spotty at best. Most of the pages are run by hacker-wannabes who really don't provide any useful information. But sometimes you can stumble across valuable tips and tricks that hackers can use to attack your system. It just takes a little time.
Another place where hackers get their information about networks is from a FAQ (Frequently Asked Questions). FAQs contain information on many different topics, ranging from physical fitness to chemistry to hacking.
One of the best resources you can find on the Internet about hacking Windows NT networks is Simple Nomad's "Unofficial NT Hack FAQ." You can obtain this FAQ from the Nomad Mobile Research Centre Web site at http://www.nmrc.org/files/nt/index.html. At the time of this writing, Nomad had marked the Unofficial NT Hack FAQ as "beta" to indicate that he considered it to be incomplete. However, we'd expect this FAQ to grow as more NT hacking information comes available, so be sure to check the Nomad Mobile Research Centre Web site frequently for updated versions of this FAQ file.
To obtain the FAQ, download the NTFAQ1.ZIP file. This file is 34,448 bytes long, so it won't take much time to download. You should download the file to a temporary directory on your hard drive.
Because the FAQ is contained in a ZIP file, you'll need to extract it using PKUNZIP. When you unzip the file, you'll find an index and 12 additional files containing the FAQ sections. The files are plain ASCII text so you can view them with any text editor. The Unofficial NT Hack FAQ contains many topics about hacking Windows NT networks, some of which are
You might be shocked to find out some of the methods hackers have in their toolkits for attacking your network. Once you read through the file, you can devise a way to protect yourself from their attacks. You also might find the information useful if you accidentally lock yourself out of your network.
Providing a secure network is one of a network administrator's most important tasks. Even if you think you've built a secure network, you may not have. To build a truly secure network, you must know how people can break into your network and how to devise defenses. In this article, we showed you where you can find information about what hackers know about your network.
-------------------------
John Sheesley is Editor-in-Chief of The Cobb Group's Inside NetWare journal.
-------------------------
This article is reproduced from the December 1997 issue of Exploring Windows NT. Exploring Windows NT is an independently produced publication of The Cobb Group. No part of this article may be used or reproduced in any fashion (except in brief quotations used in critical articles and reviews) without prior consent of The Cobb Group. To contact The Cobb Group, please call (800) 223-8720 or (502) 493-3200.
Copyright © 1997 The Cobb Group, a division of Ziff-Davis Inc. The Cobb Group and The Cobb Group logo are trademarks of Ziff-Davis Inc. All rights reserved. Reproduction in whole or in part in any form or medium without express written permission of Ziff-Davis is prohibited.