Does your network contain confidential or other sensitive data? If so, you probably want to keep that data as secure as possible. In this article, we'll discuss some relatively simple procedures you can use to keep your data from falling into the wrong hands.
When people think of network security, they often think of passwords. However, secure passwords are only one of several barriers you can use to safeguard your data. Nonetheless, since passwords are such a prominent piece of your network's security system, it's worth discussing some simple steps you can take to make them more secure.
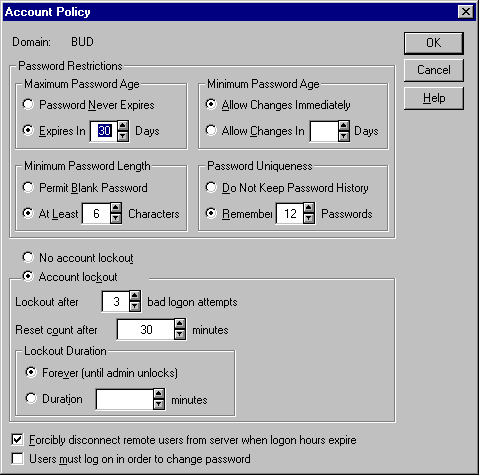
Because of the way passwords are encrypted, it can take hackers weeks to break difficult ones. For this reason, you should use passwords that aren't easy to crack and make them expire often. Both Windows NT Server and Novell NetWare servers allow you to impose certain restrictions on your network passwords. For example, as you can see in Figure A, we've set a minimum password length. We also force users to create a new password every 30 days and don't allow them to reuse old passwords for quite some time. Another safeguard we've taken is to disable an account after three bad logon attempts. This prevents hackers from trying to guess passwords.
Figure A

You can greatly restrict password credentials.
Unfortunately, there are other ways for hackers to obtain passwords. In fact, there are utilities that will crack passwords for you. For example, we ran one such utility, called NTCrack, on one of our test servers, and Figure B shows the result. In order to use NTCrack, a hacker must download another utility, called PWDUMP, to make a text file that contains a copy of the encrypted passwords stored in an NT Server's registry. NTCrack then compares the encoded passwords stored in the text file against a dictionary file containing regular words as well as names. Therefore, you should avoid using names and common words as passwords. The safest passwords are words that are made up, misspelled, or mixed with numbers or symbols.
Figure B
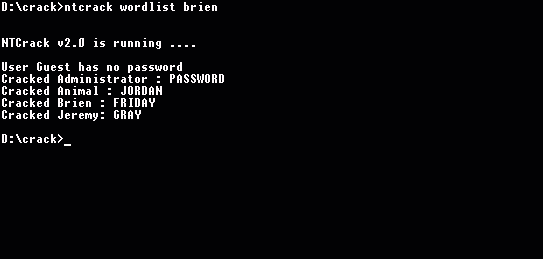
NTCrack instantly reveals weak passwords.
While it may seem scary that utilities such as NTCrack exist, there is a bright side. You can download a free copy of NTCrack from the Internet and then use it periodically to see if anyone is using a vulnerable password. You can download NT crack from
www.secnet.com/nav6.html
You'll also need PWDUMP, which you can download from
ftp://samba.anu.edu.au/pub/samba/pwdump
One word of caution: We noticed that NTCrack's dictionary contains less than 900 words. You may consider adding your own words to its dictionary file to further enhance security—you want to test for as many possible passwords as you can.
Although you can greatly reduce the chances of someone figuring out your password, you can never completely prevent it. Because of this, we recommend not putting all your eggs in one basket. If you use multiple servers, we suggest using a different Administrator password for each server. That way, if someone were to crack the Administrator password, the damage they could do would be limited to one server.
Even though your network may have secure passwords, there's always the chance that users may tell someone else their password or try to use information on the network for their personal gain. When this happens an employee will typically come into the office to access the network rather than using a dial-up connection, which is usually closely monitored. Since the user won't want to draw any attention, he or she may try to access the forbidden data from a PC in a remote corner of the building or plug a laptop into a vacant network jack in a secluded location. The user may also try to do this late at night when there are relatively few people in the building.
Fortunately, you can protect your network against this type of user. Both NetWare and Windows NT Server allow you to restrict which PCs a user may log in through, as shown in Figure C. By limiting a user's access to one PC or one department's PC, you prevent the user from logging on to a PC in a secluded section of the building. In the process, you've also made it more difficult for outside hackers to access your network, because even if they figure out a password, it will work only in certain locations.
Figure C
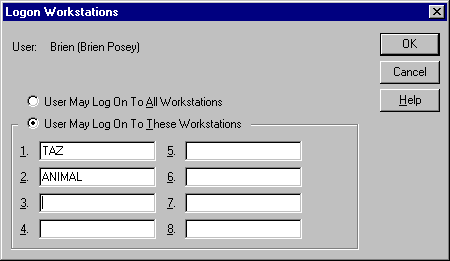
You can control which PCs a given user can log in through.
However, controlling which PCs users are allowed to log in through isn't a total solution. If users are allowed to log in through a laptop, they can plug the laptop in anywhere in the building, and the network will know only that they're logging in from an authorized PC. To prevent this, we recommend disconnecting any unused network jacks from your hubs. If you're using a coaxial cabling topology, we suggest replacing any unused T-connectors with barrel connectors. Although a malicious user could still disconnect another PC and use that network hookup, he or she would risk drawing unwanted attention in the process.
Finally, you'll probably want to limit the times when users can log in. Obviously, you may have to be flexible for people who work lots of overtime, but you can limit everyone else's login privileges to business hours Monday through Friday, as shown in Figure D. Even those users who work overtime usually do so at consistent times throughout the week For example, suppose a user works late but is usually gone by 9:00 PM. In that case, you might deny access between 11:00 PM and an hour or two before the user typically arrives in the mornings. Of course, you should use caution when restricting access times—you don't want to interfere with the productivity of legitimate users.
Figure D
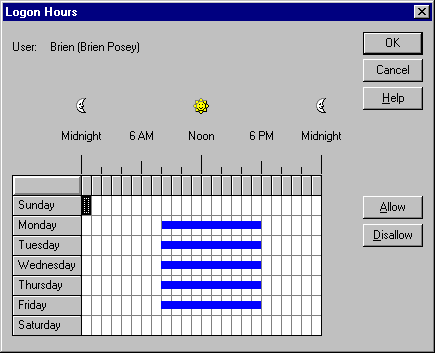
You can tighten security by limiting access times.
If people at your company use laptops, chances are you've got a dial-up connection set up for remote network access. Unfortunately, remote access servers give hackers an easy way to crack your network without ever being seen. One way you can significantly reduce the chance of this happening is to use an automatic call back feature. For example, suppose that some users typically dial in to the network from home. If you're using Windows NT Server, you can set it up so that when the user logs in, the server disables the connection and then calls the user back at his or her preprogrammed home phone number. This way, you can be relatively sure that it's really that user who's logging in.
Some remote access packages will allow the person logging in to specify the number the server should call back at. Although this isn't as secure as using preprogrammed phone numbers, it accommodates users who travel. The server will keep a log of all phone numbers it has dialed, so you can periodically review the list for suspicious phone numbers.
Both Windows NT Server and NetWare provide tools for auditing various network events. Tools such as Audit Policy, shown in Figure E, allow you to keep a written record of various network events. Because these tools let you audit many different events, the log files can quickly become overwhelming to read. Therefore, you should audit only those events that could be signs of someone trying to break into your network. For example, you might keep track of login attempts that fail to provide the correct password within the number of attempts you've specified. Or you might keep a record of people who log in after business hours.
Usually, one of the first things that a hacker will do when breaking in to a system is create a network account that can be used for future access. Therefore, it's very important to audit the creation and deletion of accounts.
In a NetWare environment, you must supply a password to view the audit log. You should use a unique password and be very selective about whom you give it to.
Figure E
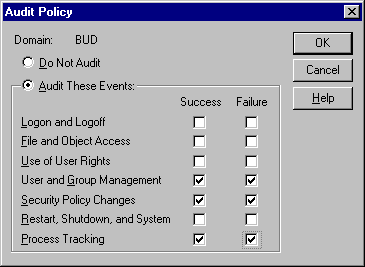
Auditing can be used to track network usage.
All the workstation security in the world won't help you if someone can access your server directly. Therefore, you should keep your servers behind locked doors. Keep in mind though that the room should be climate-controlled; don't keep your servers in a closet with no air conditioning or ventilation.
You should also keep your hubs in a secure location. If you don't, someone wanting to steal your data badly enough could hook a network analyzer up to a hub and steal data and passwords as they come across the wire.
It's also important to keep your LAN cables in a secure location. If you don't, a hacker could tap a cable and steal the data packets as they go across the network. When possible, we recommend running network cables in crawl spaces or in hanging ceilings. However, if you do run cable in these areas, be sure to use plenim cable to avoid starting a fire.
One of the easiest ways for hackers to access your data is to steal one of your backup tapes. They could then set up their own server elsewhere and restore only the data portion of the tape, thus bypassing any security. To prevent this from happening, we recommend that you keep a fire-proof vault in a secured location, such as the room where you keep your servers. As soon as you arrive in the morning, you should place the previous night's backup tape in the vault to prevent it from being stolen or accidentally damaged. Store all other backups in a secure off-site location, so you'll be well protected against theft and natural disasters. At the end of the day, you should move the previous night's backup to the off-site location and then load a blank tape into the tape drive. If you recycle tapes, you should erase the tape you plan on using for tonight's backup before you leave for the night. The idea is to make sure that if someone steals the tape after you leave, the only thing they'll get is a blank tape.
There are also a couple of things you can do when you schedule the backup to make your data more secure. First, most backup programs will allow you to assign a password to the tape—make sure you take advantage of this feature. Second, schedule the backup so that it finishes about the same time that you arrive in the morning. That way, no one can steal the tape in the middle of the night, because the backup will still be running. If someone does steal the tape during the backup, they won't be able to get any data off of it. That's because most programs back up all the files before they write the file's location to the header of the tape.
In this article, we've discussed some of the ways in which data can be stolen from a network. We've also explained some precautions you can take to make your network more secure.
-----------------------
This article is reproduced from the December 1997 issue of Windows 95 Professional. Windows 95 Professional is an independently produced publication of The Cobb Group. No part of this article may be used or reproduced in any fashion (except in brief quotations used in critical articles and reviews) without prior consent of The Cobb Group. To contact The Cobb Group, please call (800) 223-8720 or (502) 493-3200.
Copyright © 1997 The Cobb Group, a division of Ziff-Davis Inc. The Cobb Group and The Cobb Group logo are trademarks of Ziff-Davis Inc. All rights reserved. Reproduction in whole or in part in any form or medium without express written permission of Ziff-Davis is prohibited.