Michael Wachal
Microsoft Corporation
Revision Date: January 1999
For the latest information, see http://support.microsoft.com/support/default.asp.
Introduction
Configuring Your Internet/Intranet Server
Configuring Microsoft Replication Manager 4.0
Distributing a Replica Set on the Internet/Intranet
Securing the Internet Server
Tips and Tricks
References
Internet synchronization was introduced in Jet database engine 3.5 as a way to exchange the data in a replicated database over an Internet or intranet connection. With the release of Jet database engine 4.0, several new features have been introduced to Internet synchronization. Among the new synchronization features in Jet 4.0 are:
Internet synchronization can also be used on a local area network (sometimes called an intranet) in place of standard indirect synchronization. Internet synchronization (unlike indirect synchronization) does not require a Synchronizer on the client computer to synchronize a database.
To initiate synchronization over the Internet, the client computer must make an HTTP connection to an Internet or intranet server. Depending on how the client computer and the server are configured, establishing a connection with the server may result in the display of a logon dialog box at the client computer. In this case, the synchronization will not occur unless a user at the client computer types the appropriate user name and password in the logon dialog box. Once connected, the client computer builds a message file containing the database changes that have occurred since the replicas were last synchronized, and uploads the message file to the drop box on the Internet or intranet server.
The Internet Synchronizer applies these changes to the base replica, unless you specify a replica other than the base replica by using Visual Basic® for Applications code.
Note The base replica is determined by three criteria: it must be a full replica; the Synchronizer must manage it; and it must have the lowest Replica ID of all the managed replicas from the same replica set at that Synchronizer. The base replica is sometimes referred to as the gateway replica.
After these changes have been applied to the base replica, the Internet Synchronizer builds a message file containing the database changes from the base replica (or the replica specified in code), that have occurred since the client and server replicas were last synchronized, and places the message file in the drop box on the Internet or intranet server. The Internet server sends the name and location of the message file back to the client computer. The client computer then transfers the message file from the server, and all the changes specified within the message file are applied to the client replica.
Internet synchronization allows users of a replicated database to exchange updates by means of a series of message files transferred by using either the FTP or HTTP protocol. The protocol used for transfer of the message files is dependent on the combination of the Internet protocols supported on both the client and the server computers. If both the client and server support the HTTP 1.1 protocol, HTTP will be used for transfer of the message file; otherwise, FTP will be used. When using HTTP 1.1, a client computer can now synchronize from behind a properly configured proxy server to a Synchronizer on the Internet. The reverse configuration, a Synchronizer behind a proxy server, has not been tested and is not supported by Microsoft. The use of a proxy server is not supported when using the FTP protocol. The following table shows the minimum requirements for Internet synchronization and the protocols that will be used by various Internet servers and clients.
| Server | ||||
| IIS 2.0/3.0 | IIS 4.0 | Netscape | ||
Client |
IE 3.02 | FTP | FTP | N/A |
| IE 4.x/5.0 | FTP | FTP/HTTP | HTTP |
Encryption Settings: In Jet database engine 3.5, all message files transferred through the Internet were encrypted. The encryption process increases the amount of time required to complete Internet synchronization. The performance of Internet synchronization in Jet database engine 4.0 has been improved by using the encryption status of the source database to dictate the encryption status of the message files. If a database is encrypted, the message file created from it will be encrypted; otherwise, the message file will not be encrypted. If data security is a concern in your replicated applications, you will have to make sure that all of the databases in your replica set are encrypted prior to use for Internet synchronization.
Replica Visibility Types: In Jet database engine 3.5, there was only one type of replica called Global. Jet database engine 4.0 adds two new types of replica visibility: local (not discussed in this paper) and anonymous. Anonymous replicas are designed to limit the amount of data stored about the members of a replica set and help control synchronization topology. Because of this, an anonymous replica is an excellent choice for a client replica. Because of the limited information that is stored about anonymous members of a replica set, the Synchronizer window will not be cluttered with icons representing client replicas. Anonymous replicas can only synchronize with their parent replicas (that is, the member of the replica set that was used to create the anonymous replica) and that parent replica must be managed by Replication Manager.
Customized Timeout Values: Five new registry keys have been added to allow you to customize the timeout values for many of the processes of the Internet Synchronizer. The default settings for these keys allow the most flexibility and error recovery during Internet synchronization. You may be required to modify these settings to get an optimum configuration for your replicated application. The client program will be unavailable during Internet synchronization, including during the periods of time that it is waiting for a timeout to occur. The Jet database engine creates these keys in the following location in the Windows® Registry:
HKEY_Local_Machine\Software\Microsoft\Jet\4.0\Transporter\
These timeouts are stored in the Windows Registry as hexadecimal DWORD values and can only be changed by using a registry editor such as Regedit or Regedt32.
The names and default values are as follows.
| Key Name | Default Value (sec) | Description |
| Timeout_Internet_Client | 3600 | Determines the length of time the client (Access, Replication Manager, or the Synchronizer) will wait for a return message from the server once the initial message has been sent. |
| Timeout_Internet_Connect | 120 | Determines the length of time the client will wait to get an FTP connection to the Internet server. If you are using FTP to synchronize and you have a busy server, increasing this value may increase the chance of a successful synchronization. |
| Timeout_Synch | 60 | Determines the amount of time the Internet Synchronizer will wait for the target database if another Synchronizer is using it. The higher this value, the more pending synchronizations can be waiting on the Internet server. |
| Timeout_Sync_Internet_Server | 3600 | Synonymous to Timeout_Internet_Client, but is set on the server and affects the Internet Synchronizer. |
| Timeout_Synch_Lock | 60 | Determines the amount of time the Synchronizer will wait to obtain a Jet lock. If you get frequent synchronization failures due to contention or locking problems, try increasing this value. |
Before you can synchronize over the Internet, you must properly configure your Internet server and the Replication Manager. If you are new to the Internet, here is the easiest way to configure everything.
Note The Replication Manager runs on Intel server platforms only, and supports the Microsoft Internet Explorer and Netscape server platforms.
This paper describes configuring your Internet server, configuring Microsoft Replication Manager 4.0, and creating and distributing the replica set. For more information about installing Microsoft Access 2000, see the documentation provided with your product.
The first step in preparing for Internet synchronization is to configure your Internet or intranet server. The following section details the steps for configuring Microsoft Internet Information Server 4.0 on Windows NT 4.0 Server or Workstation.
For Internet or intranet synchronization to be successful, you will need two directories (folders) managed by your Internet server. The first directory should be part of the HTTP service. This directory is used to house the copy of the Internet Synchronizer program (mstrai40.exe) that handles the exchange of information with Internet or intranet replicas that are requesting synchronization. Because the Synchronizer will be running in this folder, it must have read and execute permissions enabled for it in the HTTP service. Either create your own new directory or use an existing directory, such as the Scripts directory in IIS. The second directory will be used as the Internet drop box. This directory serves as the exchange point for the message files that hold the database changes from each replica involved in the synchronization. Because both the Synchronizer and the remote replica will be using this directory, it needs both read and write permissions enabled on the server. Because Jet database engine 4.0 now supports the HTTP 1.1 protocol, the FTP service, the HTTP service, or both can manage this drop box. For maximum flexibility, you will want to make your Internet drop box available to both the FTP and the HTTP service.
Note For this to be properly configured in Replication Manager, you must have identically named Virtual Directories in both the FTP and HTTP services pointing to the same directory on your physical hard disk. This is explained in more detail in the configuration steps later in this paper.
The following examples for configuring an Internet or intranet server are specific to Microsoft Internet Information Server. The steps to configure your Internet or intranet server may be different. Microsoft Access support engineers do not directly support the configuration of Internet or intranet servers. If you have questions regarding the configuration of an Internet or intranet server, contact the manufacturer of that server. For questions about Microsoft Internet servers, please call (425) 635-7018, 6:00 A.M. to 6:00 P.M., Pacific Time, Monday through Friday, excluding holidays, and ask for support on your specific server product. Or, visit our support site at http://support.microsoft.com/support/default.asp.
Microsoft Internet Information Server 4.0 and Personal Web Server 4.0 on Windows NT 4.0 Workstation are based on the same Internet server software. Both are configured identically using the Internet Service Manager.
Note To install the Internet Service Manager and the FTP service on Windows NT 4.0 Workstation, you must use the custom install option when installing Personal Web Server 4.0.
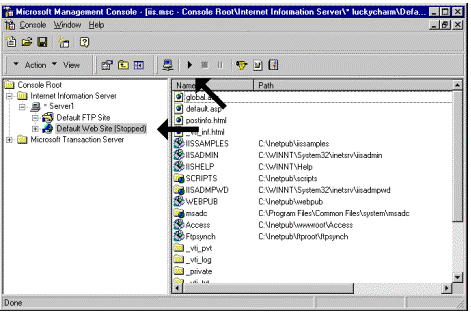
For the purpose of this example, it is assumed that you are using the Scripts directory for the location of the Internet Synchronizer, and you create a directory named Drop box to be used as the Internet drop box. See Figure 1.

Figure 1. Expanded Internet Information Server folder
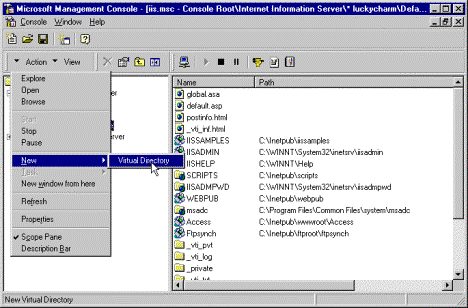
Figure 2. Locating the Virtual Directory
Drop box in the Alias to be used box, and then click Next.
Figure 3. Locating Scripts directory in Console Manager
Note For information about security concerns, see the "Securing the Internet Server" section later in this paper.
Note For information about security concerns, see the "Securing the Internet Server" section later in this paper.
Drop box in the Alias to be used box, and then click Next.You have now added the required directories to your HTTP and FTP services to use Internet or intranet synchronization. From here, you need to configure the Microsoft Replication Manager. To do so, see the "Configuring Microsoft Replication Manager 4.0" section later in this paper.
Internet synchronization is not supported by Microsoft Personal Web Server 4.0 on Windows 95 and Windows 98 because is does not support the FTP service and you cannot set Write permissions on an HTTP directory. For Internet synchronization to be successful, you must be able to send a message file to either an FTP or HTTP drop box.
To configure Microsoft Replication Manager 4.0 on your Internet server for use with Internet replication, follow these steps:
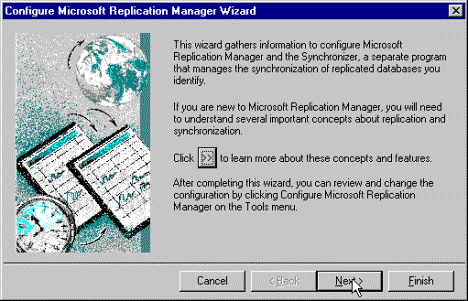
Figure 4. Configuring Microsoft Replication Manager Wizard
If this Synchronizer will not be used for Indirect Synchronization, do not select it, click Next, and go to step 8.
Note You may use the same FTP/HTTP folder that you created as your drop box for Internet synchronization in step 1 of the previous section as the indirect drop box; but it will be possible for outside users to read and write files to your FTP folder.
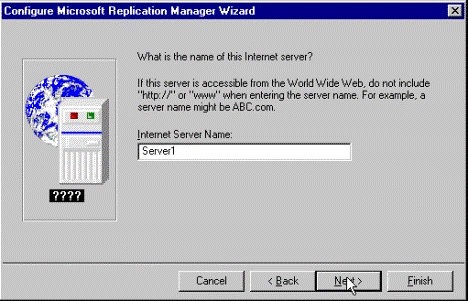
Figure 5. Enter name of Internet server
Scripts should automatically appear in the share name text box. If it does not, type it in, and then click Next. See Figure 6.
Note If you are using a directory other than the Scripts directory as your shared directory, you should provide the path and share name for that directory instead.
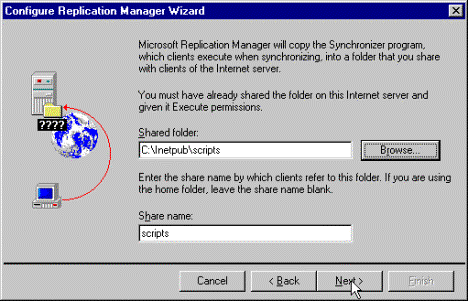
Figure 6. Share name text box
Dropbox in the FTP/HTTP alias name text box, and then click Next. See Figure 7.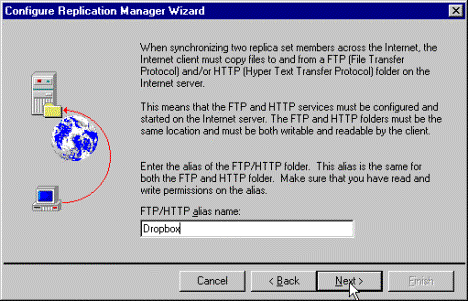
Figure 7. FTP/HTTP alias name text box
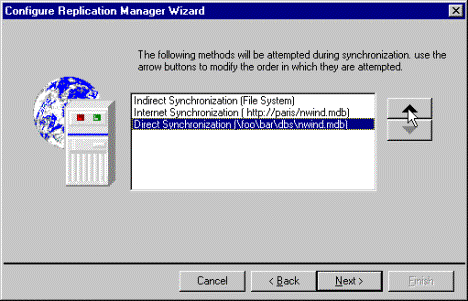
Figure 8. Using arrow buttons to set priority of synchronization types
After configuring Microsoft Replication Manager on your Internet or intranet server, you must manage at least one member of the replica set on the server. This stamps the replica with the Internet address of the Synchronizer managing it. After managing the replica in Microsoft Replication Manager, you should synchronize with other members of the replica set. This propagates the Internet address of the Synchronizer that is managing the hub replica to other members of the replica set, and enables them to synchronize to it over the Internet.
After a replica set has been enabled for Internet synchronization, you must determine the best way to distribute the set to your users. There are several ways to accomplish this:
In all cases, you must make sure that the replicas made available for distribution were created with knowledge of the Internet server that is managing the hub replica. You can ensure this by using Replication Manager to create a new replica from the managed hub, and then distribute that replica. Another thing to consider is the use of anonymous replicas at the Internet client computer. Anonymous replicas can only be created through the Microsoft Access user interface or through Jet and Replication Objects (JRO) code. An example of creating an anonymous replica is included later in this paper.
If you are distributing your replicas using FTP, you do not have to manage the replicas in the shared folders. The following diagram in Figure 9 illustrates how you might distribute a replica set for Internet synchronization using FTP. In this diagram, the Managed Replica would be in an unshared folder, and a copy of that replica is placed in an FTP folder. The FTP folder used to distribute the replica can be different than the Drop box folder (discussed earlier) and need only have Read permissions.
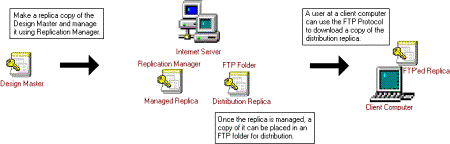
Figure 9. Distributing a replica set for Internet synchronization using FTP
To properly distribute a replica set on the Internet or intranet, you will have to convert a database to a Design Master, make a hub replica that is managed by the Replication Manager, and a create a distribution replica.
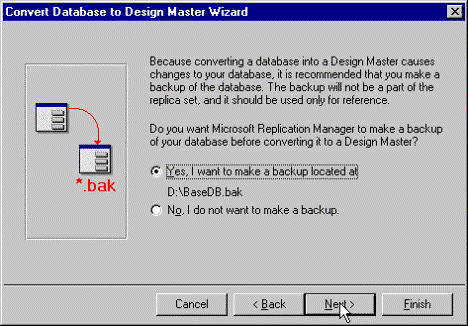
Figure 10. Making backup of database before converting to Design Master
Note If you select the option to make read-only replicas, you will not be allowed to enter data into any of the replicas made from this Design Master.
Note It is recommended that you do not manage the Design Master, but instead use a replica as the hub for synchronization. See Figure 11.
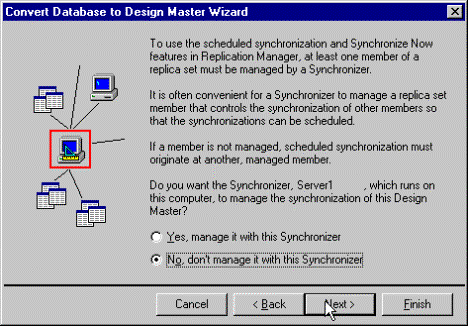
Figure 11. Managing or not managing the synchronization of the Design Master
Note Internet synchronization will not work properly if your managed hub replica is located on a different computer and managed using a UNC path. If you must save your managed hub replica to a different computer, you will need to map a drive from the Internet server to the computer where the hub replica is stored. You can then manage the replica using the drive letter.
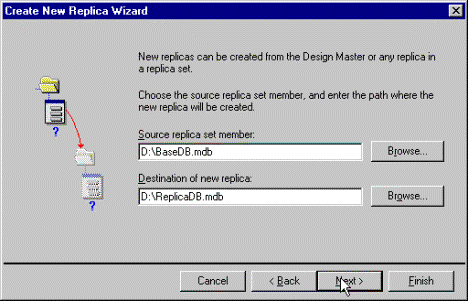
Figure 12. Create New Replica Wizard screen
Note Although it is possible to manage a partial replica as the hub replica on your server, it is not a good idea. The Microsoft Jet Synchronizer will only use a partial replica for synchronization if it is the only member of the replica set that is managed. Also, it is important to remember that you can never synchronize a partial replica to another partial replica. So if you are distributing partial replicas, you must manage a full replica.
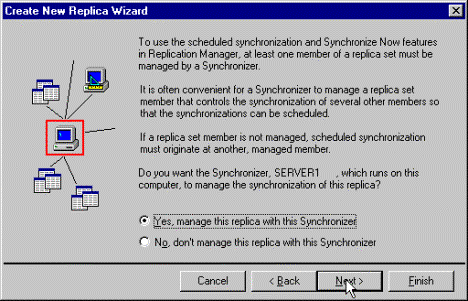
Figure 13. Managing the replica with the Synchronizer
(Optional)
While it is not required to use anonymous replicas as the client databases, several design changes in Jet database engine 4.0 make anonymous replicas ideal for Internet replication:
To create an anonymous replica for distribution, you will have to open the managed replica in Microsoft Access 2000. You can either open the managed replica directly from Access, or use Replication Manager to start Access with the managed database selected. See Figure 14.
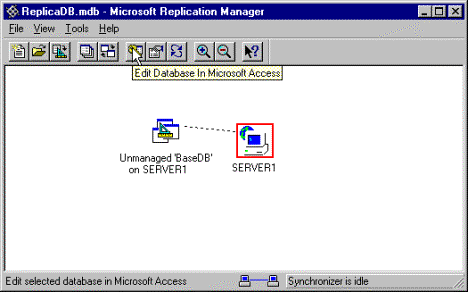
Figure 14. Starting Access using Replication Manager
Once Access 2000 is running, you can create the anonymous replica.
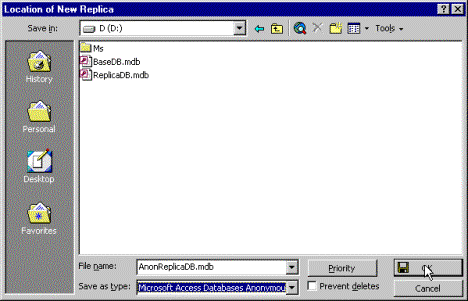
Figure 15. Location of New Replica dialog box
After the anonymous replica has been made, it can be distributed using any means appropriate for your application. Any copies of an anonymous replica will also be anonymous replicas with the same Managed hub replica as its parent.
Note Even though the option says Directly with Replica, by selecting the Web address, you will be using Internet synchronization.
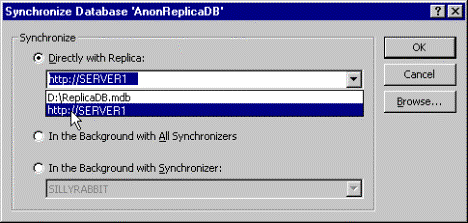
Figure 16. Synchronize Database dialog box
Limited Directory Security is available for use with Internet Synchronization when working with Microsoft Internet Information Server 4.0 running on Windows NT 4.0 Server. When an FTP or HTTP service is configured for Anonymous login, you can limit the number of users that can access the service by individual user IP address, Network ID, and Sub-net Mask or Domain. If your Internet Server supports the use of both FTP and HTTP, then directory security must be implemented for the drop box Virtual Directory in both services.
Directory security settings are configured from the Internet Service Manager by opening the Properties dialog box for the virtual directory on which you want to set up security. Once the Properties dialog box is open, click the Directory Security tab. You have two options for security configuration. By default, all users are granted anonymous access to the folder, and you can add specific users, groups, or domains that will be denied access. These instructions focus on the second option, in which you deny all users access to the directory, and then add specific users, groups or domains that will be granted access.
Note If you plan to secure your Internet server, you must specifically grant access permission to the IP Address being used by your Internet Server, together with any other users.
Single User. You can specify either the IP Address for a single user's computer or, if your system supports Domain Name Services, you can click the DNS Lookup button, and then specify the DNS computer name of the user's computer. Click OK to save the entry.
Group of Computers. You can specify a group of computers to grant access to by specifying the Network ID and Subnet Mask for the group of computers. Every computer in the specified group will have access to the directory. Click OK to save the entry.
Domain Name. You can specify a domain name to grant access to every computer in the domain. Granting permissions by domain name is by far the slowest of these methods.
Directory security for the HTTP service is configured similarly to the FTP service.
Incorrect configuration of the directory security settings can prevent users from accessing the FTP and HTTP services. If this happens, synchronization attempts by your users will fail. You should fully understand TCP/IP Networking, IP Addressing, and the use of subnet masks before using these options.
You should be aware of the following limitations when you use directory security with replication:
Internet/intranet synchronization works well when the replica set remains small (fewer than 10 individual replicas) and the number of data inserts and updates are limited. When determining if Internet/intranet replication will suit your needs, also consider the hardware and network requirements for your application. To implement Internet/intranet replication properly requires a network connection capable of handling the appropriate traffic, an Internet server that can handle enough user connections, and the hardware resources to manage running the different programs involved in synchronization, including the Internet Server, the Internet Synchronizer, and the Jet database engine. Frequently, replicated applications that work well in a small test environment will become slow or fail altogether in a much larger production environment. Make sure that when you test a replicated application, the test environment adequately duplicates the production environment not only in design, but also in resource usage.
While not considered part of the standard configuration required for successful Internet/intranet synchronization, you can tweak some settings to improve synchronization success when working with large replica sets or applications requiring frequent or numerous data inserts or updates. Most of these settings involve modification of the Windows Registry or changes to Microsoft Internet Information Server 4.0. Before making changes to the Windows Registry, you should back up the registry.
The amount of time required for the Internet Synchronizer to run is proportional to the amount of data being exchanged. When you attempt to exchange a large number of data changes or fewer data changes involving more data, it is possible that the Internet Server may close the connection to the client before the exchange is completed. A timeout setting in IIS 4.0 controls the amount of time before the server will close a connection.
CGI Script Timeout: The CGI Script Timeout determines the amount of time a CGI script is given to execute and return a value before the operation is stopped. If you are experiencing synchronization failures during long exchanges, you may benefit from increasing this timeout in the Internet Service Manager.
Because Access replication works in Jet databases, modifying some settings that affect the Jet database engine may improve the efficiency and success rate of synchronization.
Increasing Maximum Locks Available: When inserts and updates are being exchanged, the synchronization needs to obtain a Jet lock on the database that is being modified. If you are exchanging many rows in a single synchronization and experience frequent failures due to locking problems, you might benefit from increasing the number of available locks. The MaxLocksPerFile value in the Windows Registry controls the number of locks that can be obtained for any single file and has a default value of 9500. The MaxLocksPerFile value is in the registry at the following location:
HKLM\Software\Microsoft\Jet\4.0\Engines\Jet 4.0
Note Novell allows a maximum of 10,000 locks. If you are experiencing locking issues while synchronizing and one of the databases involved is on a Novell server, you may have to move the replica to successfully synchronize.
For more information about configuring an Internet server for Internet replication, search the Microsoft Replication Manager 4.0 Help Index for "Replication Manager, Internet or intranet servers."
For more information about Microsoft Replication Manager, see the Microsoft Jet Replication white paper, included with Microsoft Office 2000 Developer. You may also obtain this white paper from the Microsoft Software Library on the World Wide Web. For more information on how to obtain the Microsoft Jet Replication white paper, please see the following articles in the Microsoft Knowledge Base:
ID: Q190766 "Database Replication in Microsoft Jet 4.0"
ID: Q158721 "How to Configure and Administer Personal Web Server"
ID: Q172138 "How to Create a Virtual Directory"