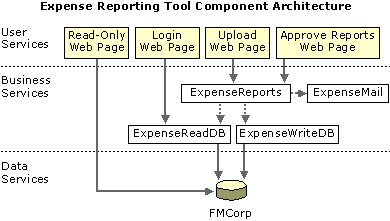
The Expense Reporting Tool uses four components developed using Microsoft Visual Basic 6.0. The components were deployed as MTS packages using the MTS Explorer. The following diagram shows how the COM components communicate between the other two tiers of the architecture.

The diagram shows the relationships the components have with each other. It is easy to see how program execution is based on validation of business rules by the MTS components. When an expense report violates the employee expenditure limits, for example, the ExpenseReports component calls the ExpenseMail component to notify the employee who submitted the report.
The Expense Reporting Tool clearly demonstrates the advantages of MTS. The ExpenseReports and ExpenseWriteDB components require transactions. This preserves the integrity of the data by ensuring that if errors occur in the system, expenses are not incorrectly posted to the database. The case described in the following paragraph describes how this works:
An employee returns from a business trip and uploads a file containing three expense report items. Her logon is validated, and a new expense report with her e-mail user name attached is generated. The first expense item, a hotel room, is added to the appropriate field in the database. The employee, however, inadvertently types $1500 instead of $150 into the form when she is reporting her car rental. This is where the MTS enforcement of business rules takes over. The employee has an expense limit of $500. When the application rejects the car rental, the ExpenseReports component is informed that the query has failed. MTS transactions are atomic, which means that all the work that a component attempts must succeed or fail as a single unit. The hotel room that had been posted to the database is now rolled back as well. The employee receives the appropriate notification and fixes the error.
The ExpenseReadDB component does not require transactions because it encapsulates all of the application's read-only methods. Because these methods do not execute any business logic or any data transformations, they can fail without threatening the integrity of the data.