 Verifying a Signature on a Message
Verifying a Signature on a Message
A digital signature is similar to a person's handwritten signature; it can be used to authenticate a sender's identity and ensure that a message is not modified during transit. It is a string of bits, called a message hash or checksum, that is calculated and then added to a signed message. Every message has a unique signature or checksum that is generated by applying a 128-bit Rivest-Shamir-Adelman (RSA) algorithm called Message Digest 5 (MD5) to the message.
Microsoft Exchange Server relies on public key cryptography to ensure the authenticity of digital signatures. When the user signs a message using the client, the checksum of the message is encrypted using the sender's private signing key. When the recipient verifies the message's signature using the client, the sender's public signing key is used to decrypt the checksum and verify the sender's identity. The signature on a message is valid only if the public and private keys correspond to each other.
Microsoft Exchange Server determines the integrity of a signed message by comparing the checksum on the message with the new checksum of the message that the recipient's client generates. If the two checksums are identical, the message hasn't been modified since it was signed. However, if even one bit in the message has been changed, the messages will have different checksums and the recipient is notified that someone tampered with the message. Encrypting the checksum using the signer's private key also ensures a signed message that no one can tamper with because the checksum on a message cannot be switched without the signer's private key. Signing a Message
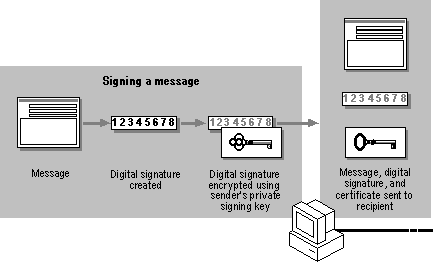
When a user signs a message, the client generates a checksum of the message and adds it to the message. The checksum (digital signature) is then encrypted using the sender's private signing key. Finally, the original plaintext message, the digital signature, and the sender's signing certificate (which contains the sender's public signing key) are sent to the recipient. The following illustration shows the steps in the message signing process.
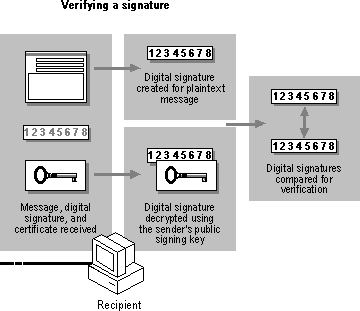
 Verifying a Signature on a Message
Verifying a Signature on a Message
When a recipient verifies a message's signature, the client checks the sender's signing certificate against the CRL. If the certificate is on the list, the recipient is warned that the sender's certificate has been revoked. If the sender's certificate is valid, the encrypted checksum (digital signature) is decrypted using the sender's public signing key, which was sent with the message. Finally, the client generates a checksum on the plaintext message so that it can be compared with the checksum that was just decrypted. The two checksums should be the same. If they are not, the recipient is warned that the message has been altered since it was originally signed. The following illustration shows the steps in the verification process.