SNA Server can also automate the process of logging on to your host system. This feature, commonly called single sign-on support, automatically logs users onto all security systems in a host security subdomain once they have been validated by any system within the subdomain. For example, if a user is logged on to the Windows NT domain, then single sign-on can automate logons to host systems that are encompassed by the defined host security domain.

Figure 7.8 Automatic logon procedure.
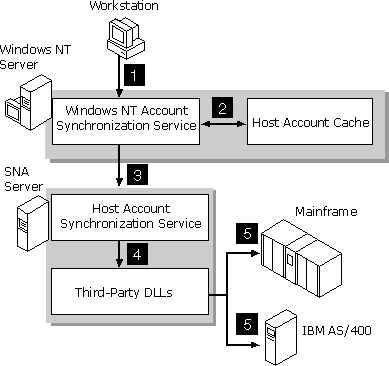
The following steps describe the automatic logon feature as shown in Figure 7.8:
When a user starts a terminal emulator or other SNA application on a client workstation, the application works with the SNA Server subdomain to perform a resource location operation to determine which SNA Server computer and connection to use to open the session (step 1).
The SNA application provides a replacement keyword as a placeholder for security information during the session initialization phase. The exact format of this keyword is dependent on the type of LU session being established. For example, the string "MS$SAME" is used for APPC or CPI-C applications.
SNA Server detects the replacement keyword and determines the Windows NT user name under which the client is logged on. Because this step requires the support of Windows NT domain authentication, automatic logon is only supported for users running native client-server sessions (for instance, SNA Server client). For example, TN3270 users are not supported because the TN3270 Service cannot determine the client’s Windows NT user name.
Once the user name is determined, the SNA Server computer uses resource location to locate the Host Account Cache in the SNA Server subdomain (step 2). The cache may be located on either the actual SNA Server computer or on the Primary Domain Controller of the SNA Server subdomain, depending on your installation. SNA Server then sends a lookup message to the host account cache that contains the Windows NT user name and password, and requests the corresponding host user name and password.
The Host Account Cache Service verifies that the Windows NT account exists in the database, and that the account is a member of the Windows NT group in the host security domain. If either check fails, the user record is purged from the host account cache. If all checks pass, the service replies to the SNA Server computer with a message containing the appropriate host account user name and password via an encrypted RPC network message (step 3).
Finally, SNA Server substitutes the host account name and password into the SNA data stream, and the host computer receives a regular session initialization request containing the correct host account information (step 4).
As mentioned previously, SNA Server natively supports single sign-on to an AS/400 host system. Single sign-on features are also available for APPC and CPI-C applications on both mainframes and AS/400 systems using third-party products. See the Microsoft SNA Server Web site at http://www.microsoft.com/sna/ for a list of supported third party-vendors.