
Although you might want the users on your corporate network to use the Internet, and users from the Internet to access certain information, you probably do not want Internet users to have full access to your corporate network.
You can use physical isolation, protocol isolation, third-party routers, and Windows NT router security in your network to provide security, although the topology you choose affects the service you provide to LAN users.
The following figure illustrates the different network topology scenarios you can implement and how each scenario influences security and service for LAN users.

Figure 20.8 Network Topology Affects Security Levels
A computer physically isolated from your LAN is the safest and easiest to plan and configure. Only the Internet server can see and be seen by the Internet. Even the most clever hacker cannot browse your corporate network without physical access. Of course, the Internet server is still open to attack.
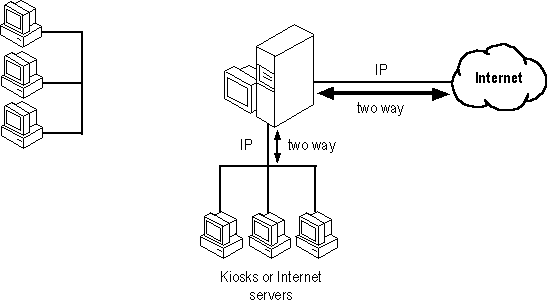
Figure 20.9 Physical Isolation Security Model
A limitation to this configuration is that you cannot share files between the corporate network and the Internet. You have to use floppy disks to share information between the two systems.
You can expand this scenario to create a small LAN connected to the Internet server. The type of configuration you choose depends on the size of your organization and on how much Internet gateway you want to give your users.
For example, if you have a single computer connected to the Internet, it serves as an Internet server that provides information to share with Internet users, and (optionally) as an Internet client that allows the users in your organization access to the Internet. For this computer to serve as an Internet client, however, it must be physically accessible to employees because it is not on the corporate net.
To give users in your organization easier access to the Internet, you can set up a small, separate network consisting of the Internet server, additional Internet servers, and individual workstations, or kiosks. The kiosks can be located in conference rooms, hallways, libraries, or in special offices scattered throughout the company. Individuals who need to make heavy use of the Internet can have kiosks in their offices. The kiosks can be used to retrieve information from your Internet server, to place new information on the server, and to gather information from the Internet at large. This type of scenario, however, might require additional cable installation.
If you want both Internet and LAN computers to see the Internet server, you can use protocol isolation security. In this model the Internet server has two network adapters. The network adapter connected to the Internet is bound to TCP/IP. The network adapter connected to the LAN runs IPX or any other network protocol except TCP/IP.

Figure 20.10 Protocol Isolation Security Model
The key to this model is that the Internet requires use of the IP protocol. If a different protocol, such as IPX, connects your Internet server to the corporate network, then the corporate network cannot be accessed by Internet users because they aren't using the correct protocol. Likewise, corporate network users cannot directly access the Internet because they are not using TCP/IP.
The protocol isolation security model is useful for users who spend most of their time making information available to Internet users and who want to copy files directly from the corporate network to the Internet server. Or, some users might need to frequently download information that is left in a "drop box" by Internet users, and then integrate that material with information from corporate electronic mail and other resources on the corporate network.
The resources on this server are accessible from either direction, but data cannot be passed through. In this way, there is a virtual barrier to passing packets through the server. Such barriers are often referred to as firewalls.
The advantage of the protocol isolation security model is that your users can share information with Internet users from their workstations on the corporate net, without exposing the corporate net to unauthorized use. One disadvantage of using this type of model is that your users cannot directly access the Internet. The users cannot search for or retrieve Internet resources, other than those resources on the Internet server you have set up. Users also cannot exchange mail with other Internet users unless you have provided the necessary Internet mail server services on the server. Another disadvantage is that, theoretically, an Internet hacker could penetrate this security model, but it is very challenging since the server does no protocol conversion.
A variation on the protocol isolation security model is to replicate the data on the Internet server onto another computer on the internal LAN using the Windows NT Replication service.

Figure 20.11 Using the Windows NT Replication Service for Security
For example, if you are using the Internet server as a drop-box for customer questions and suggestions, Internet users leave information on the Internet server, and then the Windows NT Replication service replicates the contents of the Internet server to the LAN computer. Conversely, if your LAN users need to post information to the public, users on your corporate net copy the information to be shared to the LAN intermediary computer, and then that information is replicated to your Internet server.
A replication scenario also allows more control over what is brought into the LAN and permitted out of the LAN. Files can be checked for viruses or other problems. This is a scenario used in Microsoft's corporate network.
If you are using TCP/IP on a large corporate network with high volume or multiple subnets, you will probably use a third-party router and a leased-line connection to the Internet. Some third-party routers can create a firewall by filtering packets.
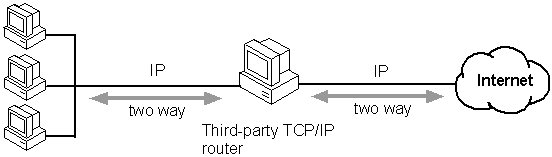
Figure 20.12 Third-party TCP/IP Router Security
If you are using TCP/IP on your corporate network, you can create a firewall in the Internet server by disabling TCP/IP routing.
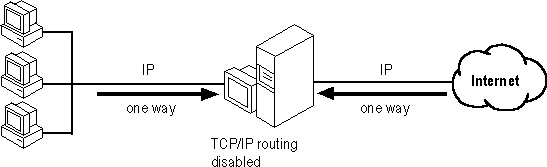
Figure 20.13 Disabled TCP/IP Router Security
This feature controls whether data is passed through the Internet server to and from the corporate network; that is, it controls whether the computer acts as a gateway.
The router feature works both ways. Either traffic can pass both ways or traffic cannot pass through the server at all. This type of security model has all the advantages and disadvantages of the protocol isolation model.
A major concern with this model is that the separation between the Internet and your corporate network depends on a single checkbox in the TCP/IP configuration dialog box (or on the associated Registry entries). Assuming an intruder somehow entered your Windows NT gateway, the intruder need only change one Registry value to expose your internal TCP/IP network.
If you use this type of security model, you also need to be especially careful to control physical and administrative access to the computer used as an Internet server. An individual familiar with Windows NT configuration tools and administrative privilege can find and change the router checkbox in a matter of moments.
Some organizations need to provide unrestricted Internet gateway to their users. For example, you might have researchers in your organization who need to scan the Internet directly as a major part of their work, and then combine information gleaned from the Internet with information that is on the corporate network. Rather than have each of these users connect to the Internet through a modem, you can have one computer running Windows NT that serves as a simple gateway to the Internet.

Figure 20.14 A Windows NT Computer Serving as a Gateway to the Internet
The computer that serves as a gateway must have a physical connection to the Internet, must be running the TCP/IP protocol, and the Router feature must be enabled.
See the Windows NT Installation Guide, TCP/IP manual, or TCP/IP online Help (TCPIP.HLP) for information on configuring TCP/IP routing.
The router feature works both ways. Either traffic can pass both ways or traffic cannot traverse the server at all. If you enable the router feature, you need to protect sensitive data by other means, such as file protections and access control as described later in this chapter.
Make sure that the users who have direct Internet gateway are aware of the security issues. In fact, you might want to periodically remind them of these issues.
You'll probably want to use the computer that serves as the gateway to the Internet configured for some Internet server services as well. It is an ideal place for shared directories where Internet users and users of the corporate network can deposit and retrieve files, and for indexes of those files.
Note Windows NT is suited as a TCP/IP router only in small, single subnet networks because Windows NT does not process RIP requests that automatically maintain a TCP/IP router's table. If you have a larger network with more that one subnet, you probably need the performance of a dedicated router (and likely have routers in your network already).