Before a user can do anything on a Windows NT system, he or she must log on to the system by supplying a username and password. Windows NT uses the username for identification and password for validation. The following procedure illustrates the interactive logon process for Windows NT.
The initial logon process for Windows NT is interactive, meaning that the user must type information at the keyboard in response to a dialog box the operating system displays on the screen. Windows NT grants or denies access based upon the information provided by the user.

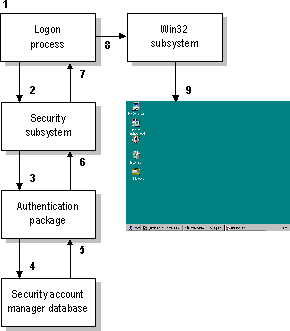
Figure 6.3 Windows NT Validation Process
The following list details the steps included in the interactive logon and validation process, as illustrated in Figure 6.3:
1. The user presses Ctrl+Alt+Del to gain the attention of Windows NT. This key combination before logon protects against Trojan Horse-type programs that impersonate the operating system and trick users into disclosing their username and password.
2. When the user provides a username and a password, the logon process calls the Local Security Authority.
3. The Local Security Authority runs the appropriate authentication package.
Note
Windows NT can support multiple authentication packages that are implemented as DLLs. This flexibility gives third-party software vendors the opportunity to integrate their own custom authentication packages with Windows NT. For example, a network vendor might augment the standard Windows NT authentication package by adding one that allows users to log onto Windows NT and the vendor's network simultaneously.
4. The authentication package checks the user accounts database to see if the account is local. If it is, the username and password are verified against those held in the user accounts database. If it is not, the requested logon is forwarded to an alternate authentication package.
5. When the account is validated, the SAM (which owns the user accounts database) returns the user's security ID and the security IDs of any global groups to which the user belongs.
6. The authentication package creates a logon session and then passes the logon session and the security IDs associated with the user to the Local Security Authority.
7. If the logon is rejected, the logon session is deleted, and an error is returned to the logon process.
Otherwise, an access token is created, containing the user's security ID and the security IDs of Everyone and other groups. It also contains user rights (described in the next section) assigned to the collected security IDs. This access token is returned to the logon process with a Success status.
8. The logon session calls the Win32 subsystem to create a process and attach the access token to the process, thus creating a subject for the user account. (Subjects are described in the section called "Subjects and Impersonation," later in this chapter.)
9. For an interactive Windows NT session, the Win32 subsystem starts the desktop for the user.
After the validation process, a user's shell process (that is, the process in which the desktop is started for the user) is given an access token. The information in this access token is reflected by anything the user does, or by any process that runs on the user's behalf.