You can use Windows NT user accounts to control access to your entire server or to control access to certain files or directories. When the Anonymous check box on the Service property sheet is cleared, every initial request from a client causes an authentication dialog box to appear. If Anonymous is selected, and Basic (clear text) or Windows NT Challenge/Response is also selected, the user is prompted for a user name and password only if the user tries to gain access to a resource on a Windows NT File System (NTFS) drive and if that resource's properties do not allow the IUSR_computername account access.
Accounts used by Internet Information Server must be granted the Log On Locally user right—whether you specify that account in Internet Service Manager or the user supplies the user name and password. By default, user accounts on a Windows NT Server domain controller are not granted the Log On Locally user right. Be sure that any account on a domain controller that is used for access by Internet Information Server is granted the right to log on locally.
How you configure and use Windows NT user accounts is determined by the authentication method your clients support and whether you use authentication over your intranet or the Internet.
User authentication is easiest to use on an intranet with an existing Windows NT user account system. Because Internet Information Server uses Windows NT user accounts, you can use your network's existing accounts and domain structure, and administer the user accounts with the familiar User Manager. Figures 3.3 through 3.5 show Maria Gonzales (mariag) logging on by using her password (KamInop8).
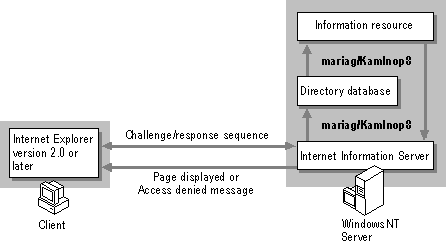
If all of your clients run Internet Explorer version 2.0 or later, you can use Windows NT challenge/response authentication, which provides secure authentication, as illustrated in Figure 3.3. If you select Windows NT Challenge/Response, all requests from Internet Explorer version 2.0 or later use challenge/response authentication. All other browsers can connect only by using Basic authentication, and the Basic authentication check box must be selected.

Figure 3.3 Challenge/response process
Internet Explorer version 1.5 does not support Windows NT challenge/response authentication. If your clients run Internet Explorer version 1.5 or earlier, or any other Web browser (for example, Netscape Navigator), you cannot use challenge/response authentication. You can, however, use Basic (clear-text) authentication, as shown in Figure 3.4.
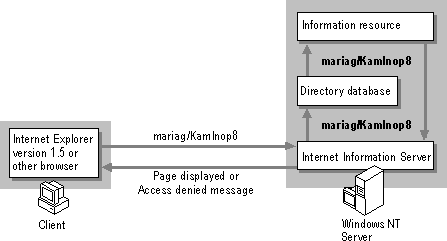
Figure 3.4 Basic authentication process
Warning
Basic (clear-text) authentication sends your Windows NT user name and password over the network unencrypted. User names and passwords sent by using Basic authentication can be learned and then used maliciously.
Basic authentication encodes the user name and password by using a base-64 algorithm—so it is not completely clear text. To intercept the user name and password, a network monitor must intercept the packet, then decode the packet containing the user name and password. With base-64 encoding, the user name or password can also contain characters that cannot be used inside a Hypertext Transport Protocol (HTTP) header.
If you are concerned about security on your intranet, you can use Basic authentication in conjunction with Secure Sockets Layer (SSL), as described in "Encrypting Private Data with SSL," later in this chapter. SSL encrypts the authentication process, as shown in Figure 3.5. However, in this scenario all transmissions are encrypted, which has a significant impact on server performance.
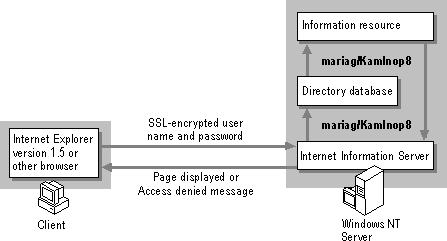
Figure 3.5 Basic SSL authentication process
The principles just discussed in the intranet section apply to user authentication over the Internet. However, because you cannot assume everyone uses Internet Explorer version 2.0 or later to access your server, you must use Basic authentication in conjunction with SSL for secure authentication.
If you expect to create thousands of user accounts for clients on the Internet, you need to investigate the hardware requirements for maintaining a large number of user accounts. Table 3.2 outlines hardware requirements for domain controllers.
Table 3.2 Domain Controller Hardware Requirements
Approximate number of user accounts | User account database file size1 | Minimum processor needed | Required RAM2 |
Up to 3,000 | 5 MB | 486DX/33 | 32 MB |
3,001-7,500 | 10 MB | 486DX/66 | 32 MB |
7,501-10,000 | 15 MB | Pentium, MIPS® Rx4000, Digital Alpha™ | 48 MB |
10,001-15,000 | 20 MB | Pentium, MIPS Rx4000, Digital Alpha | 64 MB |
15,001-30,000 | 30 MB | Pentium, MIPS Rx4000, Digital Alpha | 128 MB |
30,001-40,000 | 40 MB | Pentium, MIPS Rx4000, Digital Alpha | 166 MB |
1 User account numbers are approximate. The exact file size of the directory services database depends on the number of user accounts, machine accounts, and group accounts.
2 RAM must be at least 2.5 times the size of the directory services database.
For more information about establishing large numbers of user accounts, see the white paper, Microsoft Windows NT Server Domain Planning for Your Enterprise, available on www.microsoft.com.