Although you might want the users on your intranet to use the Internet, and want to give users from the Internet access to certain information, you probably do not want Internet users to have full access to your intranet.
When you connect an intranet to the Internet, you can use physical isolation, protocol isolation, third-party routers, and Windows NT routing in your network to provide security. The topology you choose affects the service you provide to intranet users.
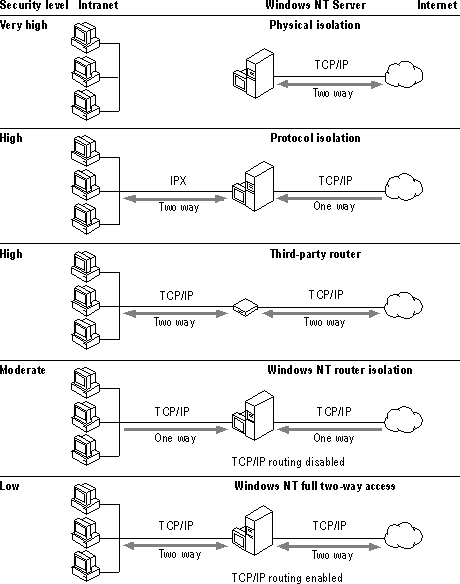
Figure 3.6 illustrates the different network topology scenarios you can implement and how each scenario influences security and service for intranet users. The sections that follow in this chapter give more information about the benefits of each security topology illustrated in Figure 3.6. (Note that third-party Internet security devices and software are available, but are not discussed in detail in this chapter.)

Figure 3.6 How network topology affects security levels