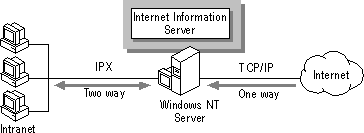
If you want both Internet and intranet computers to communicate with the computer running Internet Information Server, you can use protocol isolation security. In this model, the Internet server has two network adapters. The network adapter connected to the Internet is bound to Transmission Control Protocol/Internet Protocol (TCP/IP). The network adapter connected to the intranet runs IPX (the transport protocol used in Novell® NetWare® networks) or any other network protocol except TCP/IP. Intranet users can copy files and maintain the server. However, they cannot access the IIS server because access requires TCP/IP. Internet users can "see" the IIS server, but cannot reach the intranet because reaching it requires IPX.

Figure 3.8 Protocol isolation security model
The protocol isolation security model works best for users who spend most of their time making information available to Internet users and who want to copy files directly from the intranet to the Internet server. Or, some users need to frequently download information that is left in a drop box by Internet users, and then integrate that material with information from corporate electronic mail and other resources on the intranet.
The resources on this server are accessible from either direction, but data cannot be passed through. Because of this, there is a virtual barrier to passing packets through the server. Such barriers are often referred to as firewalls.
The advantage of the protocol isolation security model is that your users can share information with Internet users from their workstations on the intranet without exposing the intranet to unauthorized use.
One disadvantage of using this model is that your users cannot directly access the Internet or Internet Information Server. The users cannot search for or retrieve Internet resources, only those resources on the computer running Windows NT Server. Users also cannot exchange mail with other Internet users unless you have provided the necessary Internet mail server services on the server.
Another disadvantage is that, theoretically, an Internet user can maliciously penetrate this security model. However, it is very challenging since the server does no protocol conversion.
A variation on the protocol isolation security model is to replicate the data on the Internet server onto another computer on the internal intranet by using the Windows NT Replication service.
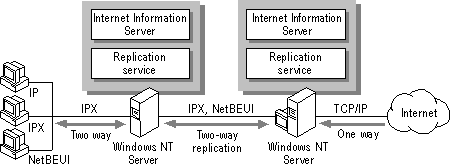
Figure 3.9 Using the Windows NT Replication service for security
For example, if you use the Internet server as a drop box for customer questions and suggestions, Internet users leave information on the Internet server, and then the Windows NT Replication service replicates the contents of the Internet server to the intranet computer. Conversely, if your intranet users need to post information to the public, users on your corporate net copy the information to be shared to the intranet intermediary computer, and then that information is replicated to your Internet server. The intermediary computer can also run Internet Information Server to provide an internal version of your Internet site. This is a scenario used in the Microsoft corporate intranet.
A replication scenario also allows more control over what is brought into the intranet and permitted out of the intranet. Files can be checked for viruses or other problems. You can also use TCP/IP on your intranet because the IPX segment between your intranet and the Internet provides protocol isolation.
For more information about replication, see Chapter 4 of the Windows NT Server Concepts and Planning guide.