
The NetLogon service provides users with a single access point to a domain's PDC and all BDCs.
The NetLogon service also synchronizes changes to the directory database stored on the PDC to all domain controllers. The size of the directory database is limited only by the number of registry entries permitted and by the performance limits of the computer.
The Windows NT Server NetLogon service automatically synchronizes the directory database. Based on settings in the registry, the PDC sends timed notices, which signal the BDCs to request directory changes from the PDC. The notices are staggered so that not all BDCs request changes at the same time. When a BDC requests changes, it informs the PDC of the last change it received, so the PDC is always aware of which BDC needs changes. If a BDC is up-to-date, the Net Logon service on the BDC does not request changes.
Changes to the directory database consist of any new or changed passwords, new or changed user and group accounts, and any changes in the associated group memberships and user rights.
Changes to the domain-directory database are recorded in the change log. The size of the change log determines how long changes can be held. The default NetLogon-service setting for updates is every five minutes, and the change log holds about 2,000 changes. As a new change is added, the oldest change is deleted. When a BDC requests changes, the changes that occurred since the last synchronization are copied to the BDC.
The change log keeps only the most recent changes. If a BDC does not request changes in a timely way, the entire domain directory database must be copied to that BDC. For example, if a BDC is offline for a time, more changes could occur during that time than can be stored in the change log.
Partial synchronization is the automatic, timed replication to all domain BDCs of directory database changes that have occurred since the previous synchronization.
Full synchronization is copying the entire directory database to a BDC. Full synchronization is automatically performed when changes have been deleted from the change log before replication takes place or when a new BDC is added to a domain.
The default NetLogon-service setting for update timing (every five minutes) and the size of the change log (about 2000 changes) ensure that full synchronization will not be required under most operating conditions.
The NetLogon service accepts logon requests from any client and provides complete authentication information from the directory database.
The NetLogon service runs on any Windows NT computer that is a member of a domain and requires the Workstation service. It also requires the Access This Computer from Network right, which is set in User Manager on computers running Windows NT Workstation, or in User Manager for Domains on domain controllers. A domain controller also requires that the Server service be running.
On a computer running Windows NT Workstation or a computer that is not a domain controller running Windows NT Server, the NetLogon service processes logon requests for the local computer and passes through logon requests to a domain controller.
The NetLogon service processes authenticates a logon request in three steps:
1. Discovery.
2. Secure channel setup.
3. Pass-through authentication (where necessary).
When the computer starts up, it must determine the location of a domain controller within the domain and in each trusted domain. (There is an implicit trust between the workstation and domain controllers in the workstation's own domain.)
Locating the domain controller is called discovery. If the computer is part of a workgroup, rather than of a domain, the NetLogon service terminates. (If the workstation is not connected to a network, Windows NT treats it like a member of a workgroup consisting of one member.) Once a domain controller is discovered, it is used for subsequent user-account authentication.
When a domain controller starts up, the NetLogon service attempts discovery with all trusted domains. Discovery is not necessary on the domain controller's own domain, because it has access to its own directory database. Each domain is called three times in intervals of five seconds before discovery fails. If a trusted domain does not respond to a discovery attempt, the domain controller attempts another discovery every 15 minutes until it locates a domain controller on the trusted domain.
If the domain controller receives another request for authorization before discovery is successfully completed, it immediately attempts another discovery, no matter when discovery was last attempted.
The Net Logon services from each computer issue challenges to and receive challenges from every other computer, to verify the existence of their valid computer accounts. When verification is complete, a communication session is set up between the computers and used to pass user-identification data.
The NetLogon service maintains security on these communication channels by using user-level security to create the channel. The following special internal-user accounts are created:
The NetLogon service attempts to set up a secure channel when it is started and discovery is complete. If it fails, NetLogon retries every 15 minutes or whenever an action requiring pass-through authentication occurs. To reduce network overhead for trusted domains, the NetLogon service on a domain controller creates a secure channel only when it is needed.
The first time a user logs on to a domain account from a given workstation, a domain controller downloads validated logon information (from the domain directory database) to the workstation. This information is cached on the workstation. If a domain controller is not available on subsequent logons, the user can log on to the domain account using the cached logon information.
Computers running Windows NT Workstation and Windows NT Server store the information authenticating the last several (the default number is ten) users who logged on interactively. The credentials for users who log on to the local computer are also stored in that computer's local directory database.
Pass-through authentication occurs in the following cases:
Note
If the logon computer is not running Windows NT Workstation or Windows NT Server, domain controller authentication has no effect on the user's ability to use resources on the logon computer.
In case 1, the logon computer sends the logon request to a domain controller in the domain to which the computer account belongs. The controller first checks the domain name. If the domain names matches the controller's domain, the controller authenticates the logon credentials against its directory database and passes the account-identification information back to the logon computer, allowing the user to connect to resources on both the logon computer and the domain.
If the domain does not match the controller's domain, the controller checks whether the domain is a trusted domain. If it is, the domain controller passes the logon request through to a domain controller in the trusted domain. That domain controller authenticates the username and password against the domain directory database and passes the account-identification information back to the initial domain controller, which sends it back to the logon computer.
If the logon credentials supplied match the account-identification information, logon succeeds. If not, logon fails.
In case 2, the controller checks the domain name to see if it is a trusted domain. (The domain controller does not check for computer name because its directory database contains only domain accounts). If the domain is a trusted domain, the controller passes the logon information to a domain controller in the trusted domain for authentication. If the trusted domain controller authenticates the account, the logon information is passed back to the initial domain controller, and the user is logged on. If the account is not authenticated (is not defined in the trusted domain directory database), the logon fails.
If, in case 3, the user is logged on to a computer or domain account and then tries to make a network connection to another computer, pass-through authentication proceeds as in interactive logons. The credentials used at interactive logon are also used for pass-through authentication unless the user overrides those credentials by typing a different domain or computer name and user name in a dialog that appears under the following circumstances:
The figure below illustrates pass-through authentication. In this example, AnnM wants to access a computer in the London domain. Because the London domain trusts AnnM's home domain, Topeka, it asks the Topeka domain to authenticate AnnM's account information.

Figure 2.3 Pass-through authentication
If the user tries to make a network connection to a remote computer in an untrusted domain, the logon proceeds as if the user were connecting to an account on the remote computer. That computer authenticates the logon credentials against its directory database. If the account is not defined in the directory database but the Guest account on the remote computer is enabled, and if the Guest account has no password set, the user will be logged on with guest privileges. If the Guest account is not enabled, the logon fails.
For information about the Guest account, see the Microsoft Windows NT Server 4.0 Concepts and Planning Guide, Chapter 2, "Managing User and Group Accounts."
If the computer being connected to is a BDC in the domain in which the user account is defined, but the BDC fails to authenticate the user's password, the BDC passes through the logon request to the PDC in the same domain. For example, this happens if authentication is attempted after the password changes but before the BDC synchronizes with the PDC.
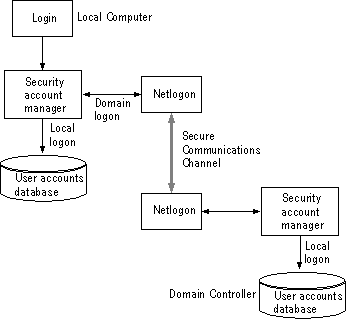
Figure 2.4 Passthrough authentication in Windows NT