The following section is a crash course in NT Directory Services (NTDS). It is not intended to compete with the numerous books that are dedicated to NT administration, but is included to define various concepts that are used in the remainder of this chapter.
Directory Services is one of the services provided by NT. It enables a user to be identified, and provides access to the various resources throughout the systems and networks. In addition, it allows a system administrator to manage the users and the network, from any system on that network.
The reader should be aware that the future plans for Windows NT 5.0 include the Active Directory, which will be the next generation of NT Directory Services. This extends the previous Windows-based directory services and will provide a single administration point for locating and managing all system resources—the Active Directory will contain items such as: users, printers, email addresses, databases, fax servers, distributed components and so on. It is designed to scale to the largest of enterprises and contain millions of items that could be distributed over many thousands of computers. Wrox Press will be bringing a book out focussing on the Active Directory in the near future.
Everyone who has access to an NT system is identified by a user account, which comprises of a user name, a password, and a number of logon parameters that are applied to that user; for example, the location of a script file that is automatically invoked at logon. A special NT user account is that of the administrator. Initially it is actually called Administrator, but this really should be renamed: there is no point in giving a potential hacker half the account details for free!
The administrator has complete control over the system, including the ability to create, amend and delete user accounts. The management of user accounts is done using the User Manager utility that is usually found by selecting the Start | Programs | Administrative Tools menus.

Another special user account created during NT installation is the guest account—initially called Guest and is disabled. This is designed for people who require temporary access to the system.
Ideally, the administrators will assign meaningful names to the user accounts, however these names are only used externally. Internally, NT handles user account names by using a one-to-one mapping with a unique identifier called the Security ID (SID). Even if a user account is deleted and then recreated with identical name, password, and logon parameters, it will be assigned a new SID. The internal SID value is never exposed to any users—including administrators.
A group is a collection of user accounts, and is a powerful mechanism for granting common capabilities to a number of accounts in one operation. This is extremely useful when administrating systems with a large number of accounts. Groups are created, and users added into the groups, with the same User Manager utility as manages user accounts.
There are a number of predefined groups, including:
| Administrators | users having full system control. |
| Users | users that can perform tasks for which they have been granted rights. |
| Guests | users requiring temporary access to the system. |
| Server Operators | users that can manage server resources |
| Account Operators | users that can manage user accounts. |
| Backup Operators | users that can back up and restore files. |
| Print Operators | users that can manage printers. |
A domain is a logical group of computers that share a set of common user accounts and security information—this is stored in a central Directory Services database. A version of the User Manager, called the User Manager for Domains, is used to maintain the users and users groups in a domain.
A domain includes one NT server designated as the Primary Domain Controller (PDC) that is responsible for storing the master users database. In addition, one or more Backup Domain Controllers (BDC's) may exist, which maintain a copy of the PDC's users database. The PDC and BDCs ensure that the various copies of the users databases are kept synchronized.
A user may logon to a domain, using any connected computer, and is validated by either a PDC or a BDC. The BDCs can share the workload in a heavily used network, and provide redundancy in case a PDC becomes unavailable. A PDC and BDC can also be an application server; for example, it can also host the Internet Information Server. In large enterprises, multiple domains may exist to reflect the business or territorial structure of the organization. It is possible to share resources across domains by setting up Trust Relationships.
However, the whole process of designing and setting up domains is outside the scope and concept of this book—we are assuming that you already have your internal network up and running, and you want to know more about how an Internet connection, and Active Server Pages, will affect it.
Once a user has successfully logged on to the domain, the NT security system dictates what resources that user may access. Different resources have different levels of access, and it is up to the users in the administrators and operators groups to define what level of access each user may have.
The User Rights Policy dialog within the User Manager utility can help to manage the rights granted to groups and user accounts. The security system will block any action by a user that does not have the appropriate rights.
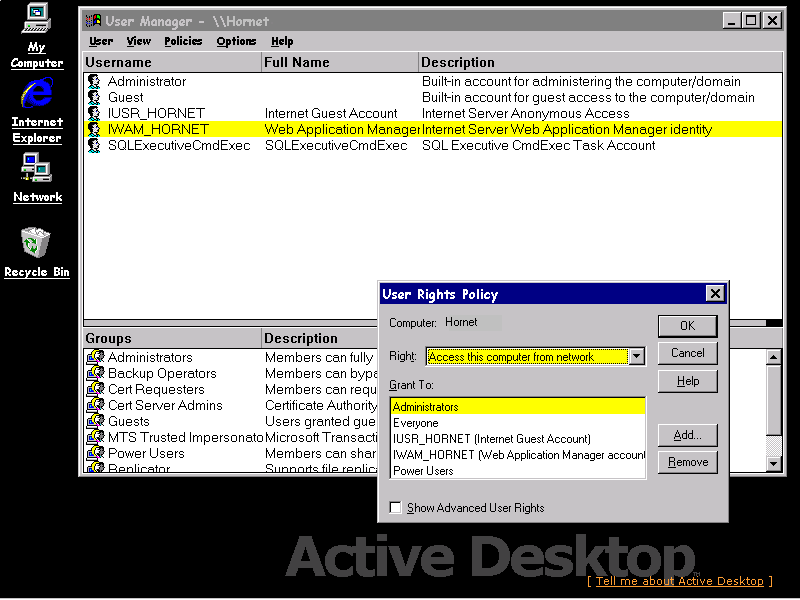
User rights are applicable to the system functions and differ from permissions that regulate to what level a user can access an individual object (such as a file or printer).
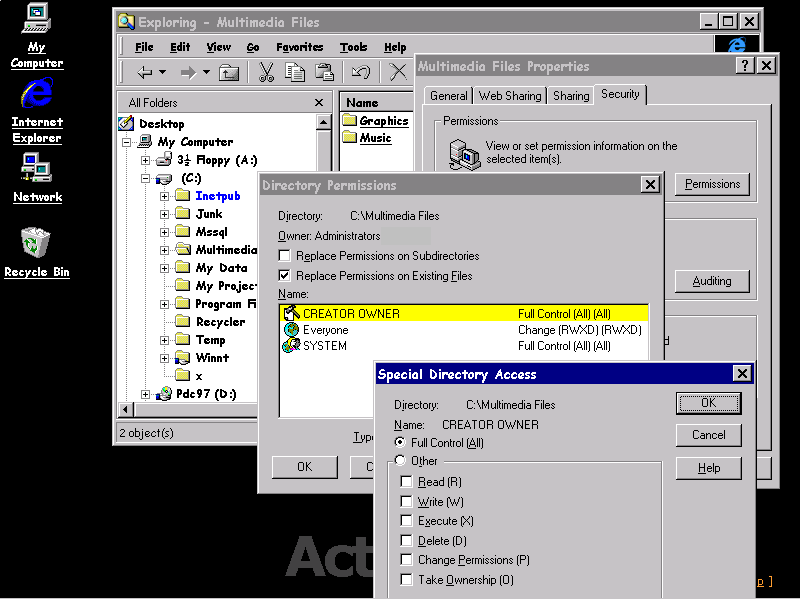
The following permissions can be assigned to a user for accessing a particular directory or file:
| Read (R) | Allows viewing the names of files and subdirectories/file data. |
| Write (W) | Allows adding files and subdirectories/changing the file data. |
| Execute (X) | Allows running the file if it is a program file. |
| Delete (D) | Allows the deleting of a directory/file. |
| Change Permissions (P) | Allows changing the directory/file permissions. |
| Take Ownership (O) | Allows taking ownership of the directory/file. |
Windows NT disks are either formatted as FAT (File Allocation Table) or NTFS (NT File System). Individual files resident on disks that are formatted as FAT do not have any security, and can only take the permissions of their parent directory. NTFS offers a greater level of security, since individual files can have their own specific permissions assigned.
Windows Explorer is used to apply or change the permissions of files and directories for individual users and groups. This is done by right-clicking on the appropriate directories, or files, and selecting the Properties option. In the Properties dialog, select the Security tab, followed by the Permissions button.
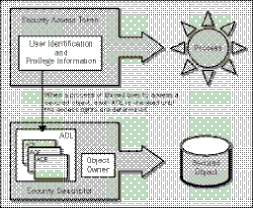
The security information of an object is stored in a Security Descriptor. This includes the name of the object owner, and something called an Access Control List (ACL). The ACL is a list of user accounts and groups (i.e. SIDs), and their associated access permissions. Each entry in the ACL is called an Access Control Entry (ACE).
Once a user's logon as been successfully validated, the system produces a Security Access Token (SAT), which is attached to any process invoked by that user. This SAT identifies the user, and is applied during all interactions with secured objects to determine the level of access allowed. All these terms are clarified in this diagram: