We will now move on to look at a software technology that provides a higher level of security than those we have just seen. It enables additional endpoint authentication, message encryption, and message authentication to be used—in fact, all the weapons we need to defeat the charlatans, spies and vandals we met earlier. This software is called Secure Channel Services (SCS).
As we all know, the Internet or an Intranet is a network of many machines, all communicating using the TCP/IP protocol standards. A protocol is a set of rules and procedures that define how two entities communicate. A protocol stack is a combination of several protocols, where each layer is responsible for handling a specific function. The TCP/IP protocol stack is shown here:

Transmission Control Protocol (the TCP part) is sometimes referred to as a transport protocol—it guarantees that packets of data are sent and received without error. It also ensures that received packets are ordered into the same sequence that they were transmitted.
Internet Protocol (the IP part) is sometimes referred to as a network protocol—it is responsible for addressing and routing packets over the network.
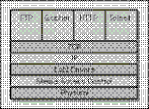
Application protocols (such as HTTP and FTP) provide the specific application data transfer logic using the lower levels for the actual delivery. Secure Channel Services transparently slots into the TCP/IP protocol stack, as shown here:

SCS is shipped with NT4.0 and IE4.0 as a dynamic-link library (
) and provides the following features: schannel.dll
SCS actually provides support for several standard security protocols
SSL 2.0 / SSL 3.0Secure Socket Layer developed by Netscape
PCT 1.0Private Communications Technology developed by Microsoft
TLS Transport Layer Security which is intended to provide a simpler and more robust solution by using the best parts of SSL and PCT
Before we can understand how SCS works, we need to investigate the cryptography it uses, and then see how to implement it on our systems.
Low-level discussions on cryptography are normally reserved for those with brains the size of a planet—since this book is supposed to be about Active Server Pages, we will keep things simple and dive in just deep enough to get a basic understanding of how it all works.