
Windows stores a range of details about each user that has access to resources on the network in a user account. This includes the password and username that they log on with, their home directory (the directory that appears as the root directory when they log on to the server), the periods during the day in which they can log on, and a range of other information.
One of the things that this does is to uniquely identify each user, so that the operating system can decide if they have permission to access each individual resource on the network server(s). However, to avoid having to enter all the information about each user individually, NT allows each user to be added to one or more groups of users, by defining group accounts. Members of a group inherit the permissions defined for that group. It's possible for user accounts to be given permissions on an individual basis as well, though it's not a good idea to do so.

It's important to remember that nobody ever logs onto the system using a group account, but only as a user. The groups are there only to allow permissions for a resource to be granted or revoked to all the user accounts assigned to that group as one operation, a big time-saver if you have a lot of users to administer. If you remove access to a particular resource from a group, all the members of that group lose access to it. However, if a user is a member of more than one group, and the other group still has access to it, they will retain this access permission.
Group And User Account Characteristics
Each group and user account is created and modified with the Windows User Manager program. Once an account has been created, it is assigned characteristics through the Account Policy dialog (available from the Policies menu):
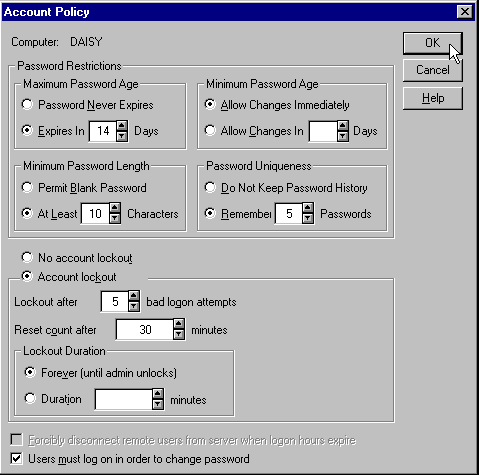
Good Practice With Accounts
The options available in User Manager mean that you can limit user access to all the resources on the machine at the lowest level, and provide a core secure environment. Because the root of all security is accurate and reliable identification of each user (i.e. authentication), you should take advantage of features like the minimum password length, password expiry periods, password renewal policies, etc.
The usual advice for creating a basic secure environment includes:
The limitations you apply to each group will, of necessity, have to match the needs that the users are required to make of the system. For more information and general guidelines on basic security, check out http://microsoft.com/ntserver/guide/secure_ntinstall.asp, or the Help files for NT's User Manager program.
One common suggestion is to disable the built-in Administrator account. However this can be dangerous, because any account that you create can be deleted by someone with appropriate permissions, while the built-in Administrator account cannot. If you (by accident) or someone else (perhaps intentionally) were to delete the only account that you have with full administrator level permissions, you are at sea without a paddle. The built-in Administrator account is disabled, and the psuedo-administrator account is gone. You can’t re-enable it the original Administrator account without it, so it's time for a full re-install...