The worst way to find out if your system is as secure as it should be is to discover that somebody has broken in and damaged it. However, if they break in and steal something without causing your server to fall over, you might never know—at least until it appears in the newspapers or in one of your competitors new products.
Audit Logging For Users And Resources
To find out if anything untoward is happening, like unwelcome visitors in the night, you can implement auditing on your system. This logs events to a disk file that you can examine at your leisure to see what's going on. A typical example is the WWW log that is produced by most Web servers. However, this is often aimed more at providing information about legitimate visitors that unwelcome ones. In Windows NT, we can use the Audit Log to audit more obvious tasks.
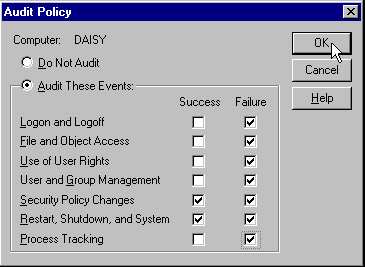
Audit logging is available for a range of events. As part of each user account's profile, you can record events like the success or failure of that user to log on or off the system, all attempts to shut down the server or change security policies, and of course their accesses to a range of resources. This dialog is available from the Policies | Audit menu:

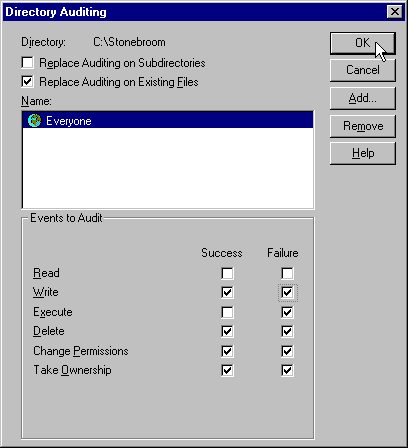
As well as logging the actions by user, you can log actions taken by groups of users on a specific resource, such as a file or directory. This is done from the Security page of the Windows NT Explorer Properties dialog for that file or directory (the dialog we saw when looking at file and directory security in the previous section):
Other applications and services can write different events to the audit log. For example MSMQ can log details of messages that failed to arrive, or attempts by users to access queues for which they have no permissions. The audit log can be viewed using Event Viewer (on the Administrative Tools section of the Start menu). Select Security from the Log menu.
One other technique is to use the Windows Performance Monitor tool to watch and record actions taking place, especially those involving the transmission of data over the network. There are also many separate applications that you can purchase for this task to offer more detailed information.
For a general view of all the security features implemented in Windows NT and the BackOffice applications and services see: www.microsoft.com/security/MSProductSecurity.htm