Let's take our DCOM experimentation with our ActiveX Calendar application to the final stage and distribute the computing load over three (or more) machines. This will allow us to get our hands wet working with the DCOM facilities provided by Windows 95 and the Windows NT system. The same technique can easily apply to any multitiered intranet applications that you may build employing DCOM technology.
While this book has dealt mainly with software development and techniques thus far, the following section will feel more like a description of a laboratory exercise. In general, any description for testing of DCOM applications will involve describing the network topology, machine profiles and the staging scenario.
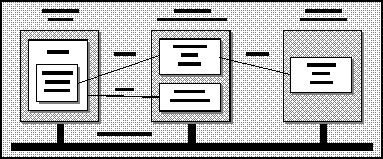
What we'll be attempting to do is set out in this diagram:

There are three machines in this configuration. They are all connected via a TCP/IP Ethernet LAN. Machine A is our client machine running the Calendar control embedded on a web page. Our web server is residing on machine B. Machine B is also where the ATLFinder COM object is run. Machine C is the host for a departmental server. The ATLDept object on machine C supports the
, IATLDept
, and ICorpEvents
interfaces with the object (and interaction) model that we covered in the last chapter.ICorpEvent
All our clients and servers are running under Windows95 in the hope that the configuration can be easily duplicated by the reader for experimentation purposes. Another reason is the relatively simple security model that DCOM for Windows 95 supports. This allows us to focus on setting up DCOM without getting caught up in security issues. Remember that since a built-in, operating system based security infrastructure is nonexistent in Windows 95, DCOM based servers all run as the currently logged on interactive user. What this means is that provided we're logged on to all the machines as the same user when we're doing the staging, there'll be no security issues whatsoever. In Chapter 9, we'll be examining the finer-grained control over DCOM security that a Windows NT platform can offer.
We'll assume all four machines are setup for DCOM as described in the DCOM Enabling our ActiveX Control: A Preview section of this chapter. The following will only cover setup procedures which are customized for each machine involved in the experiment.