![]()
This article assumes you're familiar with Windows 2000
|
Host a Discussion Forum with the Windows 2000 NNTP Service
Davide Marcato |
|
If you've ever used a newsgroup, you've used NNTP. Now Windows 2000 makes this functionality easy to implement and serve up from your site. |
|
To the average Internet user, the Network News Transfer Protocol (NNTP) is synonymous with Usenet, a network of newsgroups dedicated to the discussion of every imaginable subject you can think of, and one of the most valuable resources on the Internet today. To the Internet techie though, NNTP is a standard Internet protocol defined by RFC 977 (http://info.internet.isi.edu/in-notes/rfc/files/rfc977.txt) that makes all this discussion possible, dictating the interactions between a client's news-reading software and the NNTP server that hosts the groups. By building on NNTP technology, you can exploit this same power to provide a valuable service to your customers. Suppose you run a software development company that sells products to a vast market. You offer technical support to your customers, typically via phone and e-mail. Wouldn't it be nice if you could set up a server to host discussion forums where your customers can post questions, answer other customers' inquiries, and share information? The Microsoft® NNTP service built into Microsoft Windows® 2000 Server offers all the power of Usenet newsgroups in a highly customizable way. In this article I will show you how to set up an NNTP server in Windows 2000 and create your own newsgroups. I'll begin with a discussion of what a news server is and how it's structured.
The News Server
Installing NNTP
The MMC Interface
|
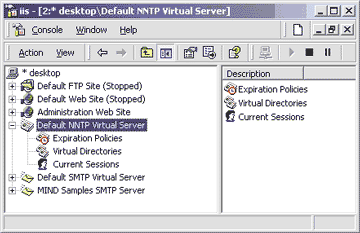 |
| Figure 1: The NNTP Service MMC Snap-in |
|
The second item in the MMC hierarchy, Virtual Directories, lists the directories where the archives of articles
are stored. Bear in mind that the names of the discussion forums are organized hierarchically. Every newsgroup tree or subtree can be associated with a physical directory on the server's hard disks. How the file hierarchy is arranged is up to the administrator. The last item in the MMC hierarchy, Current Sessions, provides the administrator with a snapshot of the clients connected to the server at any point in time, displaying their user name if it's known (or an anonymous face if it isn't), the source IP address, and the time the connection was established. In case of an emergency you can interrupt all active sessions at once by selecting the Terminate All context menu item, or selectively cut off certain clients by selecting the Terminate menu item.
The Virtual Server
|
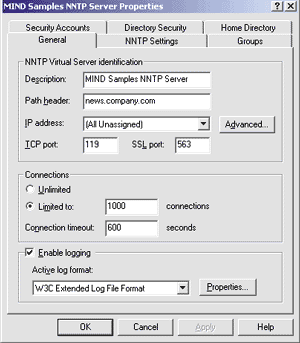 |
| Figure 2: General Settings |
|
The first tab, General, presents you with some general working parameters, as shown in Figure 2. The Description field simply contains the name displayed in the MMC snap-in to identify that specific virtual server, and carries no particular relevance outside this environment. Feel free to change it to any name you prefer; in this case, replace the default name with "MIND Samples NNTP Server." The Path header field influences how the local machine is identified in the header of each article posted through the server. In this case, the host is news.company.com in the DNS, so you should use that path header for consistency. (What the prerelease documentation neglects to say is that the string you put in this field also influences the important Xref: header.) Once you have modified this content, you must stop and restart the service for the changes to take effect. The IP address field, as I explained earlier, specifies which addresses this virtual server will respond to, with All Unassigned catching all those that are not handled by others. Clicking on the Advanced button will open up a dialog box to activate more than one identity for the current server. Notice how you can have the same virtual server responding to requests on different ports simply by adding entries in this list. The TCP and SSL (Secure Sockets Layer) port fields control which port numbers should be used during clear and encrypted communications with the clients. Notice that if you set any of these (especially the TCP port), your users will also have to configure their clients to bind to a nonstandard port number. For the convenience of your users, stick to the default ports 119 and 563.
Limiting Connections
Logs
For this test I chose the W3C Extended Log format. By clicking the Properties button you are presented with a dialog box that lets you customize the exact items that will be recorded in your log files, how often log files are generated, and the location where they are saved on the disk. For this example, the default setting of a daily log placed in System32\LogFiles works just fine.
NNTP Settings
|
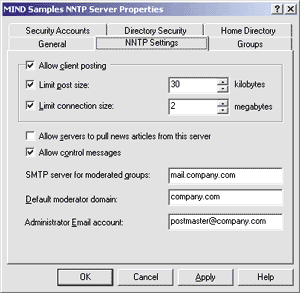 |
| Figure 3: NNTP Settings |
|
The next two checkboxes toggle advanced features on and off. The first controls whether peer news servers are permitted to log into your server and pull articles, so they can mirror your contents and offer it to their users. This mechanism is used by Microsoft with their public msnews.microsoft.com news server, which is mirrored (partially or totally) by many other NNTP hosts worldwide, thereby reducing the load of the main server. For a corporate server you will probably want to turn this switch off, as I did in this sample. The second checkbox governs control messages. A control message is a special type of posting that doesn't show up regularly in a group, but rather requests a particular service of the news server. The most common control message is the Cancel message, through which the author of a posting requests that a published article of his be immediately deleted from the archives. For a fully operational news server, leave this box option enabled.
The Moderator
Adding Discussion Groups
|
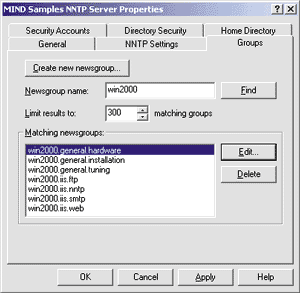 |
| Figure 4: Creating Newsgroups |
|
For this sample, I'm adding seven new groups, distributed under two subtrees—win2000.iis and win2000.general. If you select a newsgroup and click on the Edit button, you'll see the dialog in Figure 5. For each group you can choose the name, decide if it is moderated (by a specified moderator or by the default moderator), create its description, and set its read/write or read-only property. The Display Name field provides a more reader-friendly name that some browsers can display in place of the official group name. This field supports Unicode strings, which makes it useful in a wide-character language such as Chinese. If you don't plan to support Far East alphabets, leave the box empty. |
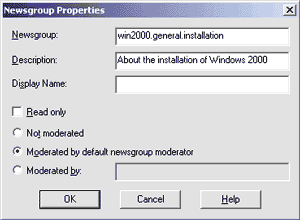 |
| Figure 5: Newsgroup Properties |
|
Security Accounts
Items under the Security Accounts tab control who can modify the configuration settings of the virtual server and which account hosts anonymous clients when they connect to the NNTP server (see Figure 6). In this case, you need to provide both a user name and a password that is valid in the Windows domain, then grant that account rights on the machine to which you want to transfer all anonymous clients. |
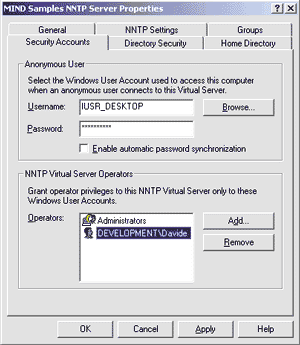 |
| Figure 6: Security Accounts |
|
The listbox in the lower half of the dialog lists the names of the security principals who are granted the rights to modify the settings of this virtual NNTP server. Valid users are identified by the Windows NT® domain name followed by the official name of the account . As you have probably realized by now, all of the configuration options are applied at the virtual host level and do not extend to the global machine-wide level. Consequently, you might decide to grant some users access to the configuration options of a secondary virtual server, while preventing them from tampering with the settings of the default news server. The default security policy considers the members of the Administrators group to be server operators, which is a reasonable setting for small to mid-sized servers. If you run a large corporate server, you might not be comfortable having to grant your mail administrator full rights in the Windows domain. If this is the case, consider adding your mail administrator to the operator's list, or create a new group in User Manager comprising the users with this kind of privileged access to the NNTP service. For this example I opted for the first solution and added the user Davide from the domain called Development to the operator's list. Notice this applies to Windows NT domains, not DNS, so Development must be a valid network domain and not a name registered with an authorized Internet naming authority.
Directory Security
|
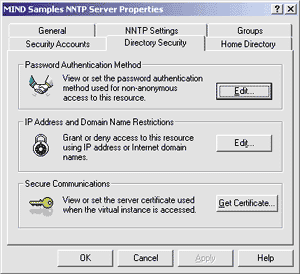 |
| Figure 7: Directory Security |
|
The Edit button in the Password Authentication Method box specifies the types of authentication that will be accepted for inbound connection attempts (see Figure 8). The first, Allow Anonymous access, is the default, and should always be checked if your NNTP server must communicate with anonymous clients over the Internet. Basic authentication permits the client to identify itself with a user name and password rather than impersonating the default account chosen by the administrator for anonymous logins. Notice that security is at risk with this method because the password travels over the wire in plain text and thus can be easily sniffed. A better and more flexible solution is selecting "Enable SSL Client Authentication", where the client and the server negotiate the best security mechanism that they both support. Then the password never travels over the wire in a reusable form. |
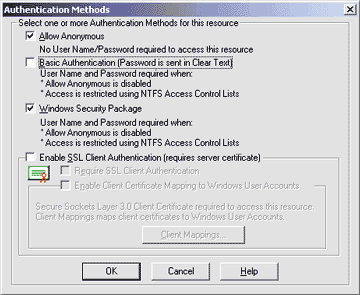 |
| Figure 8: Authentication Settings |
|
To achieve the highest level of security, extended not only to the password, but also to the entire exchange of data between client and server, check the "Enable the SSL Client Authentication" checkbox. By enabling authentication, you interface your NNTP server with an SSL certificate authority and enable encryption of the network traffic flowing through the communication channel in both directions. Beware of the resource overhead involved in processing high volumes of data prior to conducting any actual work. This can negatively affect performance. An in-depth analysis of all of the pros and cons of enabling SSL client authentication falls beyond the scope of this article. For this sample, turn off encryption altogether and enable only anonymous and Windows package-based authentication. Access can be restricted based on the IP address of the client, too. This approach has the advantage of retaining full compatibility with any NNTP user, whereas authentication-based security works only with specific clients. Clicking on the corresponding Edit button lets you grant access to everyone except those whose IP address you add to the black list. You can also choose to deny access to everyone except those whose IP address is included in the list. For the server to be publicly accessible, grant everyone access rights. A side note: if you restrict relay rights to your LAN only (this can be done through a filter in the subnet mask), you might run into the paradoxical situation of being unable to access the groups from the server machine itself. The reason is that your client will be detected as coming from the IP address on which the service is answering, hence if you contacted localhost (the loopback alias for the local machine in TCP/IP), you'll be seen as 127.0.0.1, which by definition cannot match with the subnet mask of any LAN. You can work around this by either remembering to test your local server, always using its real-world IP address, or granting additional relay rights to IP address 127.0.0.1. This is safe because nobody outside the local machine can use the special loopback address.
The Home Directory
|
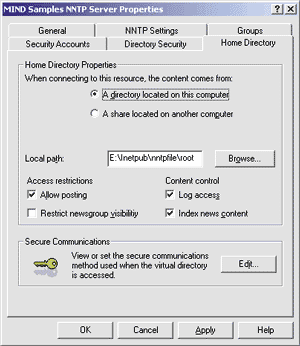 |
| Figure 9: Home Directory |
|
The Access restrictions options influence the accessibility of the newsgroups contained in the home directory. You can allow or disallow posting and restrict the visibility of the list of newsgroups to the users who have the right to read and post to them. If you uncheck this box, everybody will be able to see the list of groups—even those they are not permitted to access. I suggest you leave this box unchecked for free news servers, thereby avoiding a significant performance hit. The Content control options on the right side of the dialog affect auxiliary server features, such as the logging of transactions in the IIS log and the indexing of the posts' bodies to simplify keyword searches in the article base. These options apply to the contents of server's home directory only and can be set for each virtual directory. Notice that in order for logging to work, the administrator must have turned on the functionality at the global level in the General property tab first. The Secure Communications box enables and configures the SSL protocol for guaranteeing secure encrypted communications between the client and the server. This setting affects access to the home directory only and overrides the global parameters.
Virtual Directories and Expiration Policies
|
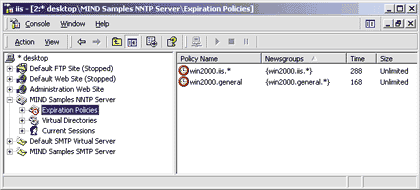 |
| Figure 10: Expiration Policies |
|
When you are finished, the window should look like the one in Figure 10. Since I haven't mentioned the Size field, you might wonder what it represents. In brief, it is supposed to represent the maximum size of the articles archive allowed by the policy. When the peak is reached, the server automatically starts to delete the postings one by one, from the oldest to the most recent, until the size falls below the cap again. This feature is convenient for containing the growth of the data files, but it doesn't appear to be supported as of Windows 2000 Server Beta 3 Build 2031, so the Size field must be set to Unlimited. Look for it in the final version.
Conclusion
|
|
|
|
http://msdn.microsoft.com/workshop/essentials/forstarters/starts1223.asp |
From the January 2000 issue of Microsoft Internet Developer.