Peter Vogel
In March 1998, the first Access virus appeared. Here's what you need to know about it.As reported in sources as diverse as PC World and WOW (the Woody's Office Watch free weekly e-mail newsletter: http://www.mcc.com.au/wow/index.htm), there's now a VBA virus that can infect Microsoft Access files. In this Smart Access article, you'll find the information that's currently available on this virus from the company that discovered it, FMS (which has released a tool for detecting it) and other sources.
Trend MicroThe virus was originally reported by Trend Micro on March 19, 1998, within a few days of the virus's creation. The new virus, written in Visual Basic for Applications, is the first known Microsoft Access database virus ever created. Although the virus doesn't have a damaging "payload" -- that is, it's not designed to destroy files -- it will actively attempt to insert itself into any database in the same directory as the infected database. There's no reason why later versions of the virus couldn't include more malicious payloads.
The virus was released through a posting to the alt.comp.virus.source.code newsgroup with the message: "I have created the first ever MS Access Macro Virus, currently under Access 97! It's called AccessiV. If you want to see the virus, mail me and I'll send you a database with the virus in it!"

Subsequent postings promised new versions with Stealth and Polymorphism enhancements, along with the ability to infect MDBs in multiple directories. The virus is also known as JETDB_ACCESS 1.
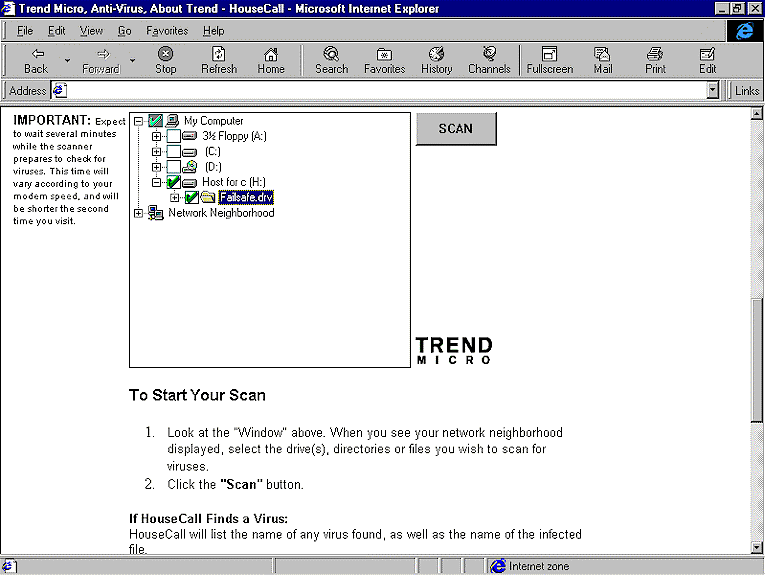
As of this writing, there are no reports of the virus outside of its original posting to the newsgroup. However, Trend Micro has updated its free online virus scanning service, HouseCall™, so that concerned Access users can reassure themselves that this virus isn't on their systems (see Figure 1). The HouseCall service can be found at http://housecall.antivirus.com.
"Trend Micro has always been known for its technical expertise in the field of virus detection and protection," said Eva Chen, chief technology officer at Trend Micro. "Today, we have set another 'first' by . . . immediately offering our customers a way to deal with [the virus] in the event their system becomes infected."
You can reach Trend Micro at 1-800-228-5651, or e-mail them at cbrodeur@schwartz-pr.com. One of the online services provided via their Web site (www.antivirus.com) is a virus encyclopedia. The entry for the Access environment can be found in Table 1.
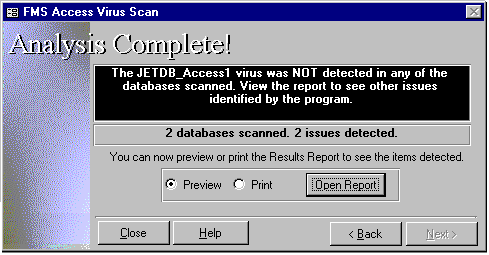
FMS to the rescueAs a service to the Access developer community, FMS (one of the leading developers of Access tools) has developed the FMS Access Virus Scanner. This simple utility scans all selected Access/Jet databases for the virus, and also detects other possible risk issues (see Figure 2). The output of this utility is a report that identifies all known issues. Note that this program doesn't remove viruses from databases -- it can only detect the virus. However, the program documentation includes complete information on removing the virus.
You can download this utility free of charge from the FMS Web site at www.fmsinc.com. Please read the license agreement on the site for important information. The FMS Access Virus Scanner is an Access 97 (version 8) database, so you must have Access 97 installed to use the program. "We are very pleased to make this utility available for the Microsoft Access community," said Dan Haught, vice president of product development and author of the FMS Access Virus Scanner. "While this first virus is fairly benign, future viruses could be much more destructive. It's important for all Access users and developers to be aware of the potential dangers and to guard against them."
Description of the virusFMS describes the virus as follows: "The virus is being distributed in the form of a Microsoft Access 97 database. The database is like any other database -- it's not corrupt, or some other file disguised as an MDB. It's merely a database with an Autoexec macro and a single module containing 100 percent legal VBA code.
"Two databases have been documented as the original carrier of the virus: accessiv.mdb and acesiv_b.mdb (the second version, released about two weeks after the original). The author of this virus has marked the macro and module in the acesiv_b.mdb version as 'hidden' using the standard Access user-interface method. This makes it harder to detect the virus at first glance, but this protection is easily circumvented.
"In order to get the virus onto your local or network drives, you must obtain and open one of the original two databases or a database infected by one these databases. The virus can't spread by any other means -- it relies on you to open its 'carrier' database in Access 97 and allow its Autoexec to run.
"Since the database is in Access 97/Jet 3.5 format, its original form can't be opened using earlier versions of Access (95, 2.0, 1.1, or 1.0). However, it can infect Access 95 databases. Infection of Access 2.0 databases is theoretically possible, but since Access 2.0 doesn't support VBA, the code won't run -- effectively preventing the Access 2.0 database from becoming an active virus carrier."
As of April 10, searches on the Microsoft Web site haven't turned up any information about the virus. In the case of Excel and Word macro viruses, Microsoft has provided protection against those viruses by disabling all VBA code in the document or spreadsheet. This is obviously not an appropriate solution for Access, where much of the functionality of the database is delivered through VBA.
Table 1. Trend Micro's Virus Encyclopedia entry on the Access virus.
| Type | Data |
| Name: | JETDB_ACCESS-1 |
| Alias: | AccessIV |
| Type: | Macro |
| Platform: | Microsoft Access |
| Number of macros: | 1 (Autoexec) |
| Encrypted: | No Encryption |
| Size of virus: | 12,288 Bytes |
| Place of origin: | USA |
| Date of origin: | March 7, 1998 |
| Symptoms: | A macro called Autoexec will be added to the database macros list. The database might or might not increase in size. |
| Destructive: | No |
| Trigger date: | No |
| Password: | No |
| Seen in the wild: | No |
| Description: | This is the first known Microsoft Access Database virus. The virus appears to have been written on March 7, 1998. The author of this virus calls himself "Jerk1N" and claims affiliation with an organization called "DIFFUSION Virus Team." Our analysis indicates that the virus has one module called "Virus" and one macro called "Autoexec." The code indicates that when you open an infected database file, the virus will search for all the .MDB files in the current directory and infect them. Our tests and analysis confirm that behavior: The virus infected the .MDB file by transferring the virus module and virus macro into the .MDB file. Unlike .COM and .EXE file infections, these infections can't be accurately identified by file size increase, but in most cases the file size will change. The foolproof way to check whether your database file is infected is to open the suspicious database file using Microsoft Access, then: 1) Go to Tools/Option/Show, choose the check box Hidden Objects, and choose the Module tab. If you can see the Virus module here, go to step 2 below. 2) Go to the Tools/Macro menu and select Run Macro; you'll see the virus macro name "Autoexec" appear on the macro list. This virus can also infect double byte Microsoft Access 97 files in languages such as Chinese or Japanese. The virus was originally written for Microsoft Access 97, but it's possible for the virus code to infect and replicate under Microsoft Access 95. It doesn't appear to infect SQL databases. |
Since Access databases aren't distributed with the same frequency as Word documents or Excel spreadsheets, the danger level for this particular virus is low. Jimmy Kuo, from Network Associates, characterized Access macro viruses as "academic." However, the virus's appearance emphasizes the importance of regular backups and constant virus checks. If you're running virus-checking software, you should check with your vendor to determine when (and if) they'll be providing protection against this threat.
Peter Vogel is the editor of Smart Access.