![]()
This article assumes you're familiar with Internet Explorer 4.0 and
C++
|
This article may contain URLs that were valid when originally published, but now link to sites or pages that no longer exist. To maintain the flow of the article, we've left these URLs in the text, but disabled the links.
|
|
A Peek Inside Microsoft Security Products
Aaron Skonnard |
| Microsoft is producing a wide variety of products that will make Web-based applications safer for users. Now all you need is a Web site and a dream! |
|
Many people are nervous about sending sensitive information over the Internet. In fact, many of my friends who are software or Web developers still don't feel comfortable making credit card purchases over the Internet. Why are people so concerned? The answer can be summed up in one word: security.
It's amazing to me that most people have no problem giving their credit card numbers over the phone to some stranger, but at the same time are afraid to have their encrypted credit card number travel over a wire to another computer. They must put a lot of trust in the people asking for their credit card numbers over the phone. They can exploit this information the same way any hacker would. It boils down to a lack of understanding. If everyone understood the security features being used and those being developed, there would be less unwarranted concern and much more confidence in our networks.
The Microsoft Security Advisor
Authenticode
|
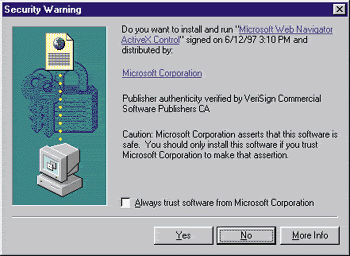
Internet Explorer 4.0 lets users customize how this type of security should be handled by introducing security zones. Currently, there are four security zones: local intranet zone, trusted sites zone, Internet zone, and restricted sites zone. For each zone, the user can specify a security level for potentially harmful active content (see Figure 2). The following four security levels can be specified: high (excludes all content that could damage your computer), medium (warns before running potentially damaging content), low (does not warn before running potentially damaging content), and custom (bases security on settings
you choose).
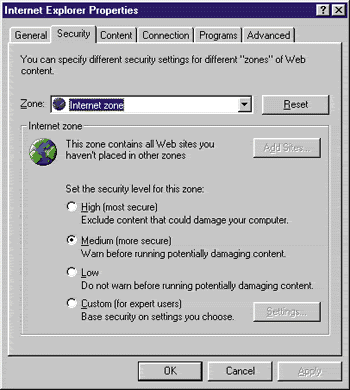
The security level is adjusted dynamically according to the security zone the user currently inhabits. For example, if you're browsing your company's local Web site, you would want to set the security level to medium or low since you trust the content on your own site. However, if you navigate to an unfamiliar external site on the Internet, you would want the security level to be bumped up a notch.
To sign code with Authenticode, follow the six-step process described here :
.Set ReservePerCabinetSize=6144 signcode -prog myfilename -name displayname
-info http://www.mycompany.com -spc mycredentials.spc
-pvk myprivatekey.pvk
chktrust filename
Client Authentication
Today, most Web sites don't require any authentication at all. You can surf to a Web site, view its content, and continue on your merry way without ever telling the Web server who you are. There are, however, many commercial sites that do business by subscription or that give users access to valuable information and services. For example, I have an online discount brokerage account that I use to lose money in the market. My bank offers a Web site for checking account balances, transferring funds, and so on. In these cases, it's very important to me that some form of authentication is offered.
Currently, when I navigate to one of these sites, I'm required to provide a user name and password. This is the only authentication process that most people are familiar with. With the release of Internet Explorer 3.0, Microsoft announced a new method called client authentication that people could use to authenticate with a Web server. While Authenticode allows the user to identify and authenticate a piece of code, client authentication gives the Web server the ability to identify and authenticate a particular client. Like Authenticode, this process is accomplished by using digital certificates issued by a CA.
This type of digital client authentication is rapidly becoming the standard on the Internet. Not only does it provide greater security than the typical password solution, it also reduces the maintenance costs incurred by having to maintain a password database. Digital client authentication also gives you more advertising power by enabling you to gather demographic information on visitors. Furthermore, you'll be able to use this information to figure out which sections of your site are the most successful and which ones need more work. And most importantly, it allows you to automatically customize the content viewed by the visitor according to his or her security level.
With digital client authentication, if I browse to my brokerage site or my online banking site, the Web server can automatically authenticate me by querying my digital certificate. No more logging in every time I navigate to the site. No more having to remember 20 different passwords. As soon as I navigate to a secure site, the server takes care of the authentication and displays the information that I have rights to view.
To enable client authentication, the user, Web server, and Web developer must each do their part. First of all, the user needs to get a digital certificate from a CA. This is very similar to the process that developers must complete to get a certificate for Authenticode. Once the CA gives the user the digital certificate, the user can identify himself to a Web server that understands client authentication. Web server administrators need to make sure that the server is configured for using client authentication. This can be accomplished by following these steps:
Secure Channels
Microsoft's secure channel technologies were designed to provide privacy between communicating applications such as a browser and a Web server. Currently, Microsoft provides Secure Sockets Layer (SSL) and Private Communications Technology (PCT) for this type of secure channel communication. Internet Explorer 3.0 and 4.0 and IIS 3.0 and later support SSL 2.0, SSL 3.0, and PCT 1.0. While SSL and PCT are similar, PCT enhances SSL in areas dealing with authentication and protocol efficiency. More information on PCT is available at
http://sectest.microsoft.com. The rest of this section will focus on how SSL works and how developers can take advantage of it in applications.
SSL uses a security handshake to initiate a TCP/IP connection. The handshake allows the client and the server to agree upon a certain level of security and takes care of any authentication necessary for the particular connection. Once the handshake is complete, SSL encrypts and decrypts all data sent between the client and the server. With HTTP, for example, SSL will encrypt the header and response including the URL being requested, form data (especially useful for information like credit card numbers), and any HTTP access authorization information such as a user name and password.
First, in order to establish an SSL connection, the client must initiate the handshake process. Once the server receives the connection request, it responds by sending the client its certificate, also known as a digital ID. At this point, the server might also request the client's digital ID if client authentication is being used. After the client receives the server's response, it verifies the server's digital ID, and if requested (for client authentication), sends its own digital ID back to the server. Then, the client sends the server a session key that is encrypted using the server's public key. Finally, both the client and the server use this session key to encrypt and decrypt all data that passes through the channel. At this point, if an intruder tries to intercept a packet, there is no way to decipher the data without knowing the previously established session key. Figure 3 illustrates how this works.
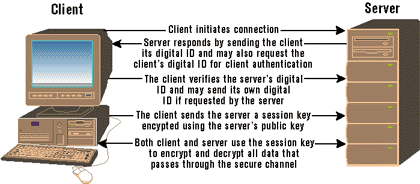
As with client authentication, the Web server administrator must configure the server to use SSL. Requests that use SSL are obviously going to take longer than those that don't because of the encryption overhead. Therefore, when configuring the server to use SSL, plan carefully to determine which files and directories need to be protected. To set up IIS to use SSL, you must follow these steps:
Smart Cards
The smart card is an exciting new security architecture that is fully supported by Windows 95 and Windows NT®. A smart card is like a credit card except that instead of storing your bank information, it stores your user identification and digital ID. Smart cards require an additional piece of hardware (just like credit cards, which need readers), so they make the most sense in public installations. This new
paradigm builds upon the digital certificate technologies and client authentication discussed earlier in this article.
With a smart card, a user can authenticate quickly and easily without having to remember and maintain a secure password. The Smart Card approach offers powerful, tamper-proof storage of private keys, account numbers, certificates, passwords, and so on. This also gives the user a simple and convenient way to move keys from one computer to another. Without Smart Cards, users of client authentication would have to transfer their digital IDs to any other computer they wanted to use with client authentication.
Microsoft's smart card strategy consists of the
following:
Certificate Server
The Microsoft Certificate Server is another example of how Microsoft is trying to simplify the management of security and lower network administration costs. The Microsoft Certificate Server issues, revokes, and renews digital certificates that can be used for client authentication. As I mentioned earlier, client authentication allows users to automatically validate themselves with a server in the most
secure and straightforward manner currently available. Furthermore, the certificate server allows for server customization by allowing the installation and configuration of different certificate issuance policies along with different certificate signature algorithms.
Let's look at three ways the certificate server could be used to fulfill specific business needs and strategies.
Corporate Web networking
A software consulting company wants to set up a Web-based bug reporting system as a communication mechanism between its clients, programmers, and testers. The programmers and testers can access the information over the intranet, while external clients need to access the information over the Internet. To accomplish this, the company issues certificates to all three groups. When the programmers or testers access the system over the intranet, their certificates will be queried and used for authentication. Similarly, when the clients access the site over the Internet, the server will query the client certificates using SSL and authenticate the clients. Once validated, whether over the intranet or the Internet, users will have immediate access to all areas of the system to which they have rights.
Customer registration An online magazine sells
subscriptions to users who want to access its information regularly. To take advantage of client authentication using
the certificate server, the client first needs to fill out a subscription signup form on the Web site. The Certificate Server processes the application information and issues the user a certificate. The user's information and security policy is then logged to the magazine's database. Once the user's certificate has been set up successfully, she can point her browser to the secure site and attempts to access the service will be authenticated automatically. Furthermore, if the user wants to cancel her subscription, the network administrator can revoke the user's certificate and deny her further access to the system.
Extending the intranet Another software company wants to give various clients access to certain directories located on the company's intranet. Each client may require different rights and security levels. To implement this, the company needs to assign each client to a Windows NT user group with specific access privileges. Then, the certificate server issues certificates to each client and maps them to the client's Windows NT account. Finally, once the certificates are assigned and mapped, the client can log onto the company intranet, which will authenticate the client according to his certificate; the user will only have access to those resources that match the privileges assigned to his Windows NT account.
As you can see, the Microsoft Certificate Server could be used to solve many common business needs while providing an environment that's more secure and easier to manage. One of the main benefits of the certificate server is that it allows an organization to manage the issuance, renewal, and revocation of certificates without having to rely on time-consuming external CAs. Using Microsoft Certificate Server, the organization has full control over the security policies and procedures it wants to implement through a simple COM interface. In addition, Microsoft Certificate Server provides tools for managing certificate transactions. For more information, point your browser to http://www.microsoft.com/iis/.
CryptoAPI and Cryptography
Cryptography is the study or application of the techniques of secret writing. In computer terms, cryptography provides a set of techniques for encoding data, which will allow the data to be stored and transmitted securely. I've already discussed some security technologies that use forms of cryptography. For example, cryptography can be used to maintain secure networks or communication systems, to safely and securely store files so other people can't read them, or to verify the origin of the data using digital certificates.
One of the main ideas behind cryptography is that everything can be public except the private cryptographic key. In other words, anyone can know about the algorithms, key sizes, file formats, and so on. Nevertheless, unless a person has access to the private cryptographic key, the security cannot be compromised.
The Microsoft CryptoAPI provides an interface that allows applications to take advantage of cryptography by encrypting or digitally signing the data. The CryptoAPI allows developers to leverage the lower-level cryptography technologies without knowing anything about the underlying implementation. Cryptography and the CryptoAPI were both covered in the June 1997 issue of MIND in articles by Dino Esposito and Brian Jamison, Josh Gold, and Warren Jamison. For additional information, point your browser to http://www.microsoft.com/security/tech/misf6.htm.
PPTP
Point-to-Point Tunneling Protocol (PPTP) is a new protocol that allows your computer to use the Internet as a virtual private network. This means you can connect to the Internet through an ISP, then access a remote network as if you were physically on the LAN.
To set up PPTP, you must configure both the server and the client. On the server side, PPTP is built into Windows NT Server and is tightly integrated with the Windows NT Remote Access Services (RAS). On the client side, PPTP is included as part of the Windows 95 Dial-Up Networking 1.2 Upgrade. For the PPTP client to work properly, you must configure the PPTP server with one port on the Internet and one port on the private network. Furthermore, you must configure each Windows 95 client to use the same protocol required
by the server.
There are many advantages to using PPTP.
Microsoft Wallet
Microsoft Wallet is another new product that helps provide a secure yet convenient way for consumers to shop over the Internet. If you've ever made an online purchase, you know the inconvenience of having to type in all your personal information (name, address, phone number, and so on) along with your credit card number. This usually requires you to get out your wallet, find the card that you want to use, and then carefully type in the number while shifting your attention back and forth between the card and the form.
Microsoft Wallet addresses these problems by allowing you to store and access payment and address information securely. If you browse a Web site that uses Microsoft Wallet for online purchases, you'll be able to select the card that you want to use and with a single mouse click send the credit card number along with your address securely over the Internet.
The Microsoft Wallet consists of the Payment Selector and Address Selector components, which are available as either ActiveX controls or Netscape plug-ins. Both the payment and address information are secured by password, so multiple users can securely access their own information stored in the same wallet module.
 |
| Figure 6: Wallet |
Conclusion
As you can see, Microsoft provides a wide array of security technologies. One key component behind most of these technologies is the digital certificate. With digital certificates in place, technologies such as Authenticode, client authentication, SSL, and PCT are possible.
As the Internet continues to grow, people will be looking for easier and more secure ways of doing business. New technologies like smart cards and Microsoft Wallet help make this possible. They provide convenient ways of storing sensitive information, and they make it easy for users to authenticate, gain access to secure information, and execute transactions.

From the March 1998 issue of Microsoft Interactive Developer.