![]()
This article assumes you're familiar with Active Server Pages,
VBScript, and
Internet Information Server .
Download the code (3KB)
|
This article may contain URLs that were valid when originally published, but now link to sites or pages that no longer exist. To maintain the flow of the article, we've left these URLs in the text, but disabled the links.
|
|
An Inside Look at Site Server Personalization & Membership
Robert Howard |
| Microsoft Site Server lets you easily build interactive, dynamic Web sites. But where do you begin? Here’s an introduction to using the Site Server personalization and membership features. |
|
Microsoft® Site Server 3.0 and Site Server Commerce Edition 3.0 were designed to help developers build interactive, dynamic Web sites. But with an abundance of tools and
options available, where do you begin? While the documentation for Site Server can seem daunting, you may be surprised by how simple and intuitive its tools really are.
The Microsoft Management Console (MMC) is the best place to start. You may be familiar with the snap-in concept introduced with Internet Information Server (IIS) 4.0. If you aren't, suffice it to say that snap-ins are common user interface tools designed to make it easy to manage enterprise applications centrally. Site Server adds several new snap-ins to the MMC that ease your managerial and administrative chores by abstracting even the most rudimentary tasks into wizards. Learning the more granular details of all the new snap-ins is time-consuming but worthwhile. The Personalization & Membership and the Membership Directory Manager snap-ins provide the control and configuration options for the personalization and membership functionality in Site Server.
What is Personalization & Membership?
Configuring a Site to Use Membership
Membership Directory and LDAP Protocol
Choosing a Database
Although using Microsoft Access for your Membership Server database is simple and quick to set up, keep in mind that the size of the Microsoft Access database directly correlates to the speed of the requests. When moving to a production environment, you should consider exporting or upsizing the Microsoft Access database to SQL Server to reap the performance benefits.
Creating the Membership Store
and Mapping to IIS
|
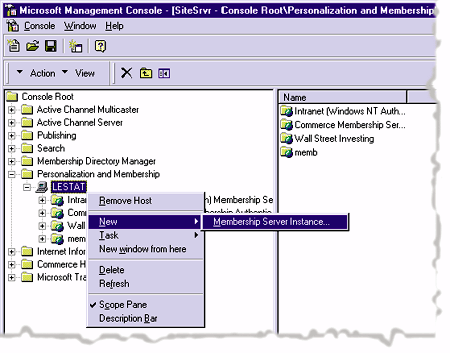 |
| Figure 3: Creating a Membership Server |
|
Now, with the New Membership Wizard open, press Next and select Custom Configuration. From this screen, select only AUO and the LDAP Service options. These options will allow you to access the Membership Directory from the Active User Object (AUO) and via LDAP. Don't select the Message Builder Service because you won't be using any mailing features here. Again, press the Next button, and create a new membership directory.
After navigating to the next screen in the wizard, you will be prompted to select an authentication mode. Remember the two security configurations I discussed earlier? This is where you make the decision to use the existing Windows NT user base or a membership user base. I'll select the membership authentication option since I don't want to create a Windows NT account for each member of my site. On the next screen you are asked to provide both a name and a password for the Membership Server instance. The name will be used as the realm when authenticating, and is the root node of the Membership Directory. The password is used for the administrator account (which is separate from the Windows NT administrator account) to administer the Membership Server. For this demo, use the name "Web Members" and set the password to "password." Pressing the Next button will display a screen prompting a database type. Select Microsoft Access and accept the defaults for all of the other options in the wizard. When the wizard has completed, a screen will display the name of the proxy user on your local Windows NT-based machine. Write this user name down, as it is dynamically granted rights to the system based on the assigned rights of the membership user. Before you move on, right-click on the new Membership Server, which will be listed as Membership Server #n (n = number of existing Membership Servers plus 1) and rename it "Web Members." Before you can authenticate users from the Web as members, you need to map the Web Members Membership Server to a Web server instance. Create a new directory under InetPub named Demo and create a new virtual server instance on an unused port. I usually use port 5000 and point it to the new Demo directory. Next, you need to map your Membership Server to the Demo Web server instance. This can all be accomplished from the MMC by simply right-clicking on the Web server instance, selecting Task | Membership server mapping, and selecting Web Members from the list of membership stores available in the dropdown menu. As soon as you click OK, press F5 and look for the new Web application (or virtual directory) _mem_ bin, which will contain two subfolders named Images and Trouble. This Web application contains all the files necessary to support the Membership Server mapping to the Membership Directory. Along with these files are special error and logon pages, as well as several ASP troubleshooting wizards. Creating and mapping a Membership Server instance to a Web server is very simple once you familiarize yourself with the MMC. All the tools you need to administer and configure the Membership Server are provided through wizards.
User Authentication and Personalization
The Active User Object
|
|
|
This statement creates the AUOUser object and maps to the current user's profile or to an anonymous profile (if enabled).
Once the AUO object has been created, it is easy to retrieve any relevant information you want. For example, to get the current user's CN, dimension a new variable and assign the value of either |
|
| or |
|
|
Either way will work equally well, although I prefer the more direct AUOUser.cn method.
To add information to the Membership Directory—assuming that the particular attribute exists—simply call the Put method for any number of items to be added, followed by the SetInfo method. Once an attribute has been added to the Membership Directory through a script or program, you can't set its value to null; you must remove it with the PutEX method. For example, after a user completes a form and posts the information back to the ASP, you should check for any nulls that the user may have sent and handle them accordingly (see Figure 4). Figure 5 lists some of the more commonly used AUO methods. If you want to see all of the methods and properties of the AUO object, you can use everyone's old friend, OLEView. AUO is listed under the ProgID of the Membership.UserObjects collection. Using the AUO object to retrieve and set user information is simple and straightforward. The set of APIs for the AUO hides from the developer the complexity of using the object to manipulate the Membership Directory. How does the AUO know who the user is? Just remember: the first thing that always happens on a personalization and membership-enabled site is authentication.
Putting It All Together
Conclusion
|
From the August 1998 issue of Microsoft Interactive Developer.