
A quick review
Before we discuss the new file system permission features of NTFS, let's review some of the basics of NTFS security available with Windows NT 4. With NTFS version 4 security, you can apply restrictions that affect users' capabilities to access files both locally and across the network. Windows NT 4 uses two terms to identify the authorization settings you apply. You apply permission sets, options like Add or Full Control, to folders and files. When the pre-defined permission sets don't offer the features you need, you can apply permissions--low-level NTFS settings like Execute or Delete. You probably don't use these terms according to their formal definitions. If you're like most NT administrators and support reps, you use the term permissions when you really mean permission sets.
Regardless of the terminology, you can assign these settings on a user or group basis. The authorization that a user actually enjoys is a combination of the permission sets granted to both their user account and to any groups to which they belong. Keep in mind that you can block all access to a file or folder with the No Access permission. This setting supersedes all others, even if the user inherits a more permissive setting through another assignment.
What's new in Win2K?
With our review out of the way, let's see how this environment will change with Win2K. First, Microsoft has re-aligned the terminology with common usage. You'll be assigning permissions rather than permission sets. When the stock permissions don't meet your needs, you'll assign special permissions. In Win2K, like NT 4, the permissions available for files differ somewhat from folder permissions. Table A shows the file permissions and Table B shows the folder permissions that will be available with Win2K.
Table A: File Permissions in Windows 2000
| File permission | Enables you to |
|---|---|
| Full Control | Read, write, modify, execute, change attributes, permissions, and take ownership of the file. |
| Modify | Read, write, modify, execute, and change the file's attributes. |
| Read & Execute | Display the file's data, attributes, owner, and permissions, and run the file (if it's a program or has a program associated with it for which you have the necessary permissions). |
| Read | Display the file's data, attributes, owner, and permissions. |
| Write | Write to the file, append to the file, and read or change its attributes. |
Table B: Folder Permissions in Windows 2000
| Folder permission | Enables you to |
|---|---|
| Full Control | Read, write, modify, and execute files in the folder, change attributes, permissions, and take ownership of the folder or files within. |
| Modify | Read, write, modify, and execute files in the folder, and change attributes of the folder or files within. |
| Read & Execute | Display the folder's contents and display the data, attributes, owner, and permissions for files within the folder, and run files within the folder (if they're programs or have a program associated with them for which you have the necessary permissions). |
| List Folder Contents | Display the folder's contents and display the data, attributes, owner, and permissions for files within the folder, and run files within the folder (if they're programs or have a program associated with them for which you have the necessary permissions). |
| Read | Display the file's data, attributes, owner, and permissions. |
| Write | Write to the file, append to the file, and read or change its attributes. |
The Read & Execute and List Folder Contents folder permissions appear to be simply copies of each other. However, they're inherited differently, thus are different permissions. Files can inherit the Read & Execute permission but can't inherit the List Folder Contents permission. Folders can inherit both.
That's it? Tell me more
Now, if those were the only changes, they'd hardly warrant mention. What's significant with Win2K is that you'll be able to assign permissions differently. You'll be able to specifically grant or deny any permission. Like before, explicitly granting a permission to a user specifically gives them the authorization to perform the actions associated with that permission. (If you assign the read permission, the user will be able to read the file.) What's new is the option to explicitly deny a permission to a user, thereby specifically withdrawing from them the authorization to perform the actions associated with that permission. As with Windows NT 4, you have a third option, which is to neither grant nor deny a particular permission. In that case, users might inherit permissions from groups of which they are members.
This new grant/deny/unspecified scheme will offer you greater control in setting permissions. With Windows NT 4, your options were limited to either not specifying a particular permission (and relying on the user not inheriting the permission through a group membership) or blocking all access via the No Access permission.
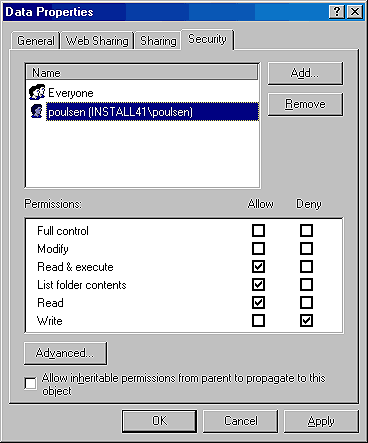
Now, for example, if you want to guarantee that a particular user can't write to a file, you can do so by explicitly denying him that permission. To do so, simply check the Deny check box for the Write permission in the Security tab of the Data Properties dialog box for the user, and no matter what permissions he inherits from group assignments, he'll be denied the ability to write to the file. Depending on his other permission assignments, the user in question might still be able to read or execute the file.
As you can see, this is a more flexible arrangement than the simplistic No Access permission of Windows NT 4. Figure A shows the Security tab in the Data Properties dialog box configured in this way.
Figure A: With Win2K, you can deny only Write access to a user
while allowing all other permissions.
Getting down to the details --special permissions
As we mentioned, file and folder permissions are actually built from groupings of special permissions. Tables C and D show which special permissions comprise each of the standard file and folder permissions.
Table C: File Special Permissions in Windows 2000
| File Special Permissions | Full Control | Modify | Read & Execute | Read | Write |
|---|---|---|---|---|---|
| Traverse Folder/Execute File | x | x | x | ||
| List Folder/Read Data | x | x | x | x | |
| Read Attributes | x | x | x | x | |
| Read Extended Attributes | x | x | x | x | |
| Create Files/Write Data | x | x | x | ||
| Create Folders/Append Data | x | x | x | ||
| Write Attributes | x | x | x | ||
| Write Extended Attributes | x | x | x | ||
| Delete Subfolders And Files | x | ||||
| Delete | x | x | |||
| Read Permissions | x | x | x | x | x |
| Change Permissions | x | ||||
| Take Ownership | x | ||||
| Synchronize | x | x | x | x | x |
Table D: Folder Special Permissions in Windows 2000
| Folder Special Permissions | Full Control | Modify | Read & Execute | List Folder Contents | Read |
|---|---|---|---|---|---|
| Traverse Folder/Execute File | x | x | x | x | |
| List Folder/Read Data | x | x | x | x | x |
| Read Attributes | x | x | x | x | x |
| Read Extended Attributes | x | x | x | x | x |
| Create Files/Write Data | x | x | |||
| Create Folders/Append Data | x | x | |||
| Write Attributes | x | x | |||
| Write Extended Attributes | x | x | |||
| Delete Subfolders And Files | x | ||||
| Delete | x | x | |||
| Read Permissions | x | x | x | x | x |
| Change Permissions | x | ||||
| Take Ownership | x | ||||
| Synchronize | x | x | x | x | x |
Permissions will still be automatically propagated down through the directory tree by default. With Windows NT 4, your only option for blocking such inheritance of permissions from a higher level folder was to assign different permissions to the object. With Win2K, you'll be able to block this inheritance of permission settings by deselecting the Allow Inheritable Permissions From Parent To Propagate To This Object check box in the Security sheet, as shown in Figure B.
Figure B: You can control permission inheritance through the
Security property sheet.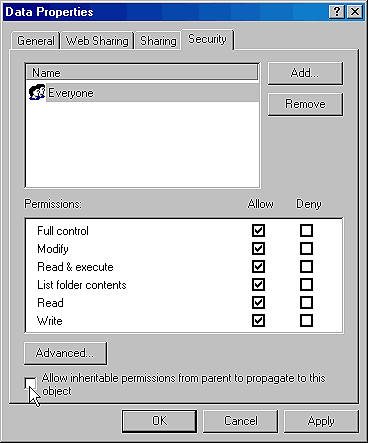
A word of caution
Finally, a feature is missing from Win2K that might catch you unaware. With Windows NT 4, if you really messed up permissions, you could simply apply new permissions to a higher level folder and check both the Replace Permissions On Subdirectories and Replace Permissions On Existing Files check boxes. Your new permissions would then get propagated down through the directory tree, effectively resetting any previously assigned permissions. Unfortunately, that feature doesn't exist within Win2K. There's no way to simply bulk-replace permissions on a whole branch of the directory tree. Of course, administrative users can still take ownership and thus gain access to files for the purposes of resetting permissions.
Conclusion
While NTFS version 5 doesn't offer any huge changes to security features, it will still significantly enhance your ability to finely control permissions settings. Through careful assignment of permissions and special permissions, you'll be able to more effectively secure your environment while allowing the access your users need.
Copyright © 1999, ZD
Inc. All rights reserved. ZD Journals and the ZD Journals logo are trademarks of ZD
Inc. Reproduction in whole or in part in any form or medium without
express written permission of ZD Inc. is prohibited. All other product
names and logos are trademarks or registered trademarks of their
respective owners.