Windows 98 allows users to log on fully. The first thing most users encounter after booting their Windows 98 systems is a logon dialog box, which varies depending on the type of network. Once the proper user name and password are validated against the security authority of the network server, the Windows 98 user interface is displayed.
System administrators can configure the Windows 98 system to allow entry into the operating system with no network access (this configuration is the default). As an alternative solution to this problem, system administrators can specify guest accounts that have limited network access.
The Windows 98 user logon should not be construed as a mechanism to fully secure personal computers. Because personal computers are still vulnerable to a floppy boot, all data stored on their disks is potentially available. The underlying file system in Windows 98 is the MS-DOS file allocation table (FAT) file system, which has no built-in encryption or other security mechanisms.
Network resources are secured under Windows 98 using the same security mechanisms employed by network servers on corporate networks. The user name and password in Windows 98 can be configured to be the same as those used by the network server. By doing this, the network manager can control network access, provide user-level security for access to shared resources on the local computer, control the various agents in Windows 98, and limit who has remote administration authority on this Windows 98 system. In this fashion, Windows 98 leverages the existing investment in network servers, management tools, utilities, and infrastructure. System administrators can manage user accounts centrally on the server, just as they always have. They can also use familiar tools for managing user accounts.
Implementing security in a Windows 98 networking environment involves the following types of activity:
Windows 98 provides share-level or, alternatively, user-level security for protecting shared resources on computers running Windows 98 (the share level requires file and printer sharing services).
Share-level security protects shared network resources on the computer running Windows 98 with individually assigned passwords. For example, you can assign a password to a folder or a locally attached printer. If other users want to access it, they need to type in the appropriate password. If you do not assign a password to a shared resource, every user with access to the network can access that resource.
User-level security protects shared network resources by requiring that a security provider authenticate a user’s request to access resources. The security provider, such as a Windows NT domain controller or a NetWare server, grants access to the shared resource by verifying that the user name and password are the same as those on the user account list stored on the network security provider. Because the security provider maintains a network-wide list of user accounts and passwords, each computer running Windows 98 does not have to store a list of accounts.
Note
For Microsoft networks, the security provider must be a Windows NT domain or workstation. For NetWare networks, it must be either a NetWare 4.x server running bindery emulation or a NetWare 3.x server.
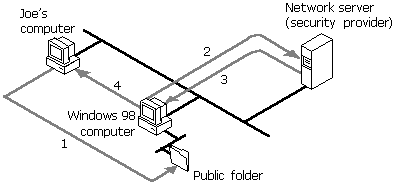
Figure 9.1 shows how user-level security works for Microsoft networks. The reference numbers are explained after the illustration.

Figure 9.1 User-level security
Joe’s password is stored on his computer’s PWL file to be used for authentication when he accesses that resource again. He will not be prompted for the password again during that session. When he logs off, the computer will erase his password from the file.
Before a user can share a resource on a computer running Windows 98, the computer must be configured for share-level or user-level security, and file and printer sharing services must be installed by using the Network option in Control Panel. Configuring share-level or user-level security is described briefly in the following sections, and in Chapter 18, "Logon, Browsing, and Resource Sharing."
Note
Share-level security is not available on NetWare networks.
 To set up share-level security
To set up share-level security
 To set up user-level security on a Microsoft network
To set up user-level security on a Microsoft network
 To set up user-level security on a NetWare network
To set up user-level security on a NetWare network
For information about specifying values for security in custom setup scripts, see Appendix D, "Msbatch.inf Parameters for Setup Scripts." For information about using System Policy Editor to set user-level security and other security options, see Chapter 8, "System Policies."
You can restrict access to resources such as a shared folder or a printer by either defining it as read-only or assigning a password to it.
 To share a folder or printer with share-level security
To share a folder or printer with share-level security
The shared resource name will be the computer name plus the share name. For example, in the following screen shot, if the computer name is mycomputer, this shared resource is \\mycomputer\mydocuments.
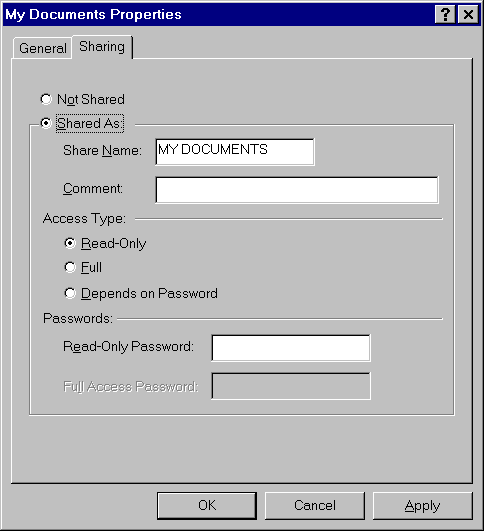
Note
There is no read-only share-level access for a printer or remote administration.
Tip
You can share a folder but hide it from the Network Neighborhood browsing list by adding a dollar sign ($) to the end of its share name (for example, PRIVATE$).
Windows 98 uses the logon process to provide user-level security for a variety of services beyond network resource access, including the following services that are remotely accessible:
Pass-through security is implemented in Windows 98 as the mechanism to enable user-level security. Pass-through literally means that Windows 98 passes authentication requests through to a Windows NT or NetWare server. Windows 98 does not implement its own unique user-level security mechanism but instead uses the services of an existing server on the network.
Enabling pass-through security is a two-step process. First, user-level security must be enabled using the Control Panel. Second, the device must be shared, and users with access privileges must be specified. Right-clicking the drive C icon in My Computer and selecting Properties from the Shortcut menu displays a property sheet that shows which shares already exist and which users have access. It also allows new devices to be shared and new users to be added to specific shares. The Windows NT server or the NetWare bindery supplies the user names listed in this property sheet.
For more information about file and printer sharing, see Chapter 18, "Logon, Browsing, and Resource Sharing."
The Remote Administration function of a Windows 98 personal computer specifies the users or groups who have authority to manage the Windows 98 system, including the following:
Remote Administration is controlled through the Passwords option in Control Panel. For more information about Remote Administration, see Chapter 23, "System and Remote Administration Tools."
For each network resource governed by user-level security, there is a list of users and groups that can access that resource.
 To share a resource with user-level security
To share a resource with user-level security
Assign, for each user, a set of rights for the resource. The kinds of rights that you assign depend on the kind of resource you are securing:
Permissions are enforced for a resource as follows:
When you do not explicitly assign access rights to a file or folder, Windows 98 uses implied rights. Implied rights are those assigned to the nearest parent folder of a file or folder. If none of the parent folders (up to and including the root directory of the drive) have explicit rights, no access is allowed.
Note
Implied rights are displayed automatically on the property sheet for the shared file or folder.
Access rights specify what a user can do in a folder protected by user-level security. The access rights you define for a folder apply to all of its subfolders. You cannot, however, assign access rights to individual files in Windows 98. (Both Windows NT and NetWare let you assign access rights to files.)
Note
Any subfolders of the shared folder, if they are also shared, must be set with the same level of security as the parent folder.
For each folder, you can assign read-only, full, or custom access. Custom access lets you further specify exactly what each user or group can do in the folder, as specified in Table 9.1.
Table 9.1 Custom access options
| File operation | Required permissions |
|---|---|
| Read from a closed file | Read files |
| See a file name | List files |
| Search a folder for files | List files |
| Write to a closed file | Write, create, delete, change file attributes |
| Run an executable file | Read, list files |
| Create and write to a file | Create files |
| Copy files from a folder | Read, list files |
| Copy files to a folder | Write, create, list files |
| Make a new folder | Create files |
| Delete a file | Delete files |
| Remove a folder | Delete files |
| Change folder or file attributes | Change file attributes |
| Rename a file or folder | Change file attributes |
| Change access rights | Change access control |
 To define custom access
To define custom access
Windows 98 user-level security depends on a list of accounts and groups located on a security provider. You cannot add or remove users and groups from the security provider list by using Windows 98 tools. However, you can do this by running User Manager for a Windows NT domain, SYSCON for NetWare 3.x, and NETADMIN for NetWare 4.x in a NetWare bindery environment. You can use these tools on a computer running Windows 98. These tools are provided by the respective vendors and not by Windows 98. Under Windows 98, you specify what rights users have to specific resources on the local computer as described in "Using Share-Level Security" earlier in this chapter. For more information about changing a user’s access rights, see "Specifying Folder Access Rights in User-Level Security" earlier in this chapter.
Note
Although Windows NT networks allow multiple domains, a computer running Windows 98 can specify only one domain for user-level security. However, you can set permissions for users or groups from any domain in the Sharing properties for the shared resource, as long as the two domains have a proper trust relationship. Also, rights may include user accounts from different trusted domains. To use a trust relationship to access multiple domains, you should consult the Microsoft Windows NT Server 4.0 Concepts and Planning Guide, part of the Windows NT Server documentation set.
NetWare 3.x servers store all the information about users, groups, passwords, and rights in a database stored on the server called the bindery. NetWare 4.x servers can appear to have a bindery through bindery emulation, a feature that is enabled by default. There is a separate bindery for each NetWare server. Windows 98 can use the bindery of only one NetWare server as the security provider. It is common for a company to have one or more NetWare servers per department, where users log on to the server for their department. This scenario can pose a problem when the bindery differs from one NetWare server to another. For example, Sue and Bob log on to the Sales server, and Fred logs on to the R&D server. Because Sue is running Windows 98 and can specify only one server for pass-through validation, she specifies Sales (the server she uses for logon). She can now grant access to shared resources on her computer to Bob but cannot grant access to Fred.
The only way to solve this problem is to include all user accounts for all servers on one NetWare server. This server should be specified as the security provider for every computer running Windows 98 with File and Printer Sharing for NetWare Networks.
Note
Windows 98 supports only bindery emulation to obtain user lists on NetWare 4.x servers. It does not support user lists obtained with NetWare Name Service (NNS) or other add-on services for that purpose.