The Component Object Model (COM) defines how components and their clients interact. The Distributed Component Object Model (DCOM) extends the COM infrastructure that underlies ActiveX, transparently and naturally adding support for reliable, secure, and efficient communication between ActiveX controls, scripts, and Java applets residing on different machines on a LAN, a wide area network (WAN), or the Internet. With DCOM, applications can be distributed across locations that make the most sense to your customer and to the application.
Because DCOM is a seamless evolution of COM, you can leverage your existing investment in all ActiveX applications, components, tools, and knowledge to move into standards-based distributed computing. As you do so, DCOM handles the low-level details of network protocols. DCOM enables component applications to operate across the Internet, because it works natively with such Internet technologies as TCP/IP and Java. It provides the "object glue" that allows business applications to work across the Web.
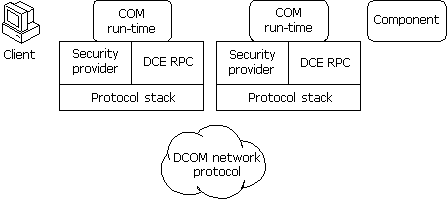
Figure 9.2 shows the overall DCOM architecture. The COM run-time provides object-oriented services to clients and components and uses the remote procedure call (RPC) and the security provider to generate standard network packets that conform to the DCOM wire protocol standard. COM provides sophisticated mechanisms for the marshaling and unmarshaling of method parameters that build on the RPC infrastructure defined as part of the distributed computing environment (DCE) standard. DCE RPC defines a standard data representation for all relevant data types, the Network Data Representation (NDR).

Figure 9.2 Overall DCOM architecture
A distributed application consists of multiple processes that cooperate to accomplish a single task. A distributed application can accommodate different clients with different capabilities by running components on the client side when possible and running them on the server side when necessary. A distributed application is also much more scalable than its monolithic counterparts, and easier to administer and deploy.
Designing a distributed application poses several challenges to the developer. One of the most difficult design issues is security: Who can access which objects? Which operations is an object allowed to perform? How can administrators manage secure access to objects? How secure does the content of a message need to be as it travels over the network?
Mechanisms to deal with security-related design issues have been built into DCOM from the ground up. DCOM provides an extensible and customizable security framework upon which developers can build when designing applications.
Different platforms use different security providers, and many platforms even support multiple security providers for different usage scenarios or for interoperability with other platforms. DCOM and RPC are built in such a way that they can simultaneously accommodate multiple security providers.
Common to all these security providers is their providing a means of identifying a security principal (typically a user account), a means of authenticating a security principal (typically through a password or private key), and a central authority that manages security principals and their keys. If a client wants to access a secured resource, it passes its security identity and some form of authenticating data to the resource, and then the resource asks the security provider to authenticate the client. Security providers typically use low-level custom protocols to interact with clients and protected resources.
The DCOM Configuration tool can be used to configure 32-bit COM and DCOM applications.
 To run the DCOM Configuration tool
To run the DCOM Configuration tool
Note
Before you can use an application with DCOM, you must use DCOM Configuration to set application properties, such as security and location.
You can use DCOM to integrate client/server applications across multiple computers. DCOM provides the infrastructure that enables client/server applications to share components over the Internet or intranet.
 To set default permissions for all DCOM applications
To set default permissions for all DCOM applications
 To set permissions for a DCOM application
To set permissions for a DCOM application
 To grant permissions that apply to all applications
To grant permissions that apply to all applications
 To set the location of a DCOM application
To set the location of a DCOM application