Networking provides a way to connect a client computer to a server by means of a transmission medium such as a network wire or a dial-up connection. It contains three key elements: the client, the transmission media, and the server.
Similarly, virtual private networking (VPN) provides a way to connect a client computer to a server by means of a tunnel through an intermediary network. That is, it uses a network as a transmission medium. The virtual private network consists of the two computers (one at each end of the connection) and a route, or tunnel, over the public or private network.
For example, suppose you want to access the resources on your corporate LAN, but you have only an Internet connection. With virtual private networking, you can "tunnel through" the Internet to access resources on your corporate LAN.
In another example, suppose you are connected to your corporate LAN (LAN A), but you want to access the resources on a server on another LAN (LAN B). LAN A and LAN B are connected by means of a private TCP/IP network. With virtual private networking, you can tunnel through the private network to access the resources on the server on LAN A just as if you were directly connected to it.
In Windows 98, virtual private networking is implemented using the Point-to-Point Tunneling Protocol (PPTP). PPTP allows you to tunnel through TCP/IP-based data networks to securely access resources on remote servers. PPTP supports multiple network protocols (IP, IPX, and NetBEUI) and can be used for virtual private networking over public and private networks. You can use PPTP to provide secure, on-demand, virtual networks by using dial-up lines, LANs, WANs, or the Internet and other public, TCP/IP-based networks.
The networking technology of PPTP is an extension of the remote access PPP protocol defined in the IETF document "The Point-to-Point Protocol" (RFC 1661). PPTP is a network protocol that encapsulates PPP packets into IP datagrams for transmission over the Internet or other public TCP/IP-based networks. PPTP can also be used in private LAN-to-LAN networking.
For more information about virtual private networking, visit Microsoft’s Web site at http://www.microsoft.com/communications/. You can also download the IETF Internet draft "Point-to-Point Tunneling Protocol—PPTP" from http://www.ietf.org/.
There are two common virtual private networking scenarios:
Some less common virtual private networking scenarios require a server provided by a third party. For instance, some VPN tunnel servers, called front end processors (FEPs), can be used for modem pooling. If your PC is on a network with a FEP that has modems available for dialing out, users can simply connect to that tunnel server, dial out, and establish a connection to a PPP access server on another network.
The following section describes the first scenario, in which you use the Internet as the network through which the client tunnels. However, keep in mind that you could use any TCP/IP network in place of the Internet. If so, you must have a permanent TCP/IP connection to a VPN server, and you do not need a dial-up connection to a network access server.
A typical deployment of virtual private networking starts with a remote or mobile Windows 98 client that uses a local ISP to access the Internet. The client then tunnels through the Internet to a private enterprise LAN.
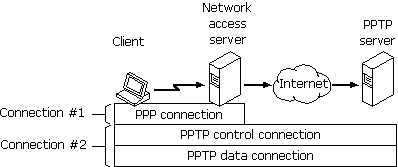
A Windows 98 client must make two connections to establish a VPN tunnel: one physical connection and one logical connection. Figure 19.6 shows these connections. The client first uses Dial-Up Networking and the remote access protocol, PPP, to connect to a network access server at an ISP’s facility. Once connected, the client can send and receive packets over the Internet. The network access server uses the TCP/IP protocol for all traffic to the Internet.
Note
Network access servers are also referred to as dial-in servers, or point-of-presence (POP) servers.

Figure 19.6 Creating a VPN tunnel
The client then uses Dial-Up Networking to make a second logical connection over the existing PPP connection. Data sent using this second connection is in the form of IP datagrams that contain PPP packets, referred to as encapsulated PPP packets.
The second connection creates the VPN connection to a VPN server on the private enterprise LAN (a computer running Windows NT Server 4.0 and configured as a VPN server). This connection is referred to as a tunnel.
Tunneling is the process of sending packets to a computer on a private network by routing them over some other network, such as the Internet. The other network’s routers cannot access computers on the private network. However, tunneling enables the routing network to transmit the packet to an intermediary computer, a VPN server that is connected to the both the routing network and the private network. Both the VPN client and the VPN server use tunneling to route packets securely to a computer on the private network by using routers that know only the address of the private network intermediary server.
When the VPN server receives the packet from the routing network, it sends it across the private network to the destination computer. The VPN server does this by processing the PPTP packet to obtain the private network computer name or address information in the encapsulated PPP packet. Note that the encapsulated PPP packet can contain multi-protocol data such as IP, IPX, or NetBEUI protocols. Because the VPN server is configured to communicate across the private network by using private network protocols, it is able to read multi-protocol packets.
Figure 19.7 illustrates the multi-protocol support built into virtual private networking. A packet sent from the VPN client to the VPN server passes through the VPN tunnel to a destination computer on the private network.
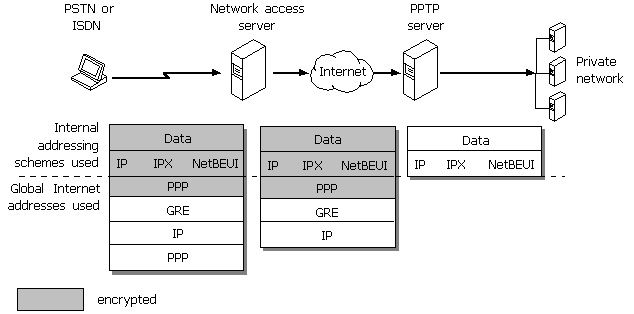
Figure 19.7 Connecting a Dial-Up Networking VPN client to the private network
PPTP encapsulates the encrypted and compressed PPP packets into IP datagrams for transmission over the Internet. The IP datagrams are created using a modified version of the Internet Generic Routing Encapsulation (GRE) protocol. (defined in RFCs 1701 and 1702).These IP datagrams are routed over the Internet until they reach the VPN server that is connected to both the Internet and the private network. The VPN server disassembles the IP datagram into a PPP packet and then decrypts the PPP packet. It then sends the de-encapsulated IP, IPX, or NetBEUI packet on the private network.
Virtual private networking allows you to create a tunnel over a public TCP/IP network but retain existing network protocols, network node addresses, and naming schemes on the private enterprise network. Thus, no changes to existing network configurations or network-based applications are required when using virtual private networking to tunnel across the Internet or other TCP/IP-based public networks. For example, IPX or NetBEUI clients can continue to run applications on the private network that require these protocols.
Name resolution methods used on the private network—such as Windows Internet Naming Service (WINS) for NetBIOS computers, Domain Name System (DNS) for TCP/IP host names, and Service Advertisement Protocol (SAP) for IPX networking—do not need to be changed.
Note
The address and name resolution schemes on the private enterprise network must be correctly configured. If they are not, VPN clients are unable to communicate with computers on the private network.
Consider the following issues when using virtual private networking:
Depending on how you will be using virtual private networking, you will need to configure different types of connections.
If you have a permanent TCP/IP connection (such as a LAN connection) to a VPN tunnel server, and you want to connect to a remote network that is connected to your VPN server, you need only configure the connection to that VPN tunnel server.
If you want to connect your workstation to a remote server by tunneling through the Internet, you must configure two connections: a connection to the Internet through your ISP and a tunnel connection to the VPN server on the target network.
To configure the connection to your ISP or your VPN tunnel server, follow the procedures outlined in "Defining a Dial-Up Networking Connection" and "Configuring and Using Dial-Up Networking Clients" earlier in this chapter.
This section describes how to use the two common VPN configurations.
Note
If you are using PPP or PPTP to connect to another IPX network, you will lose IPX connectivity to your local network. Thus, after you make a dial-up or virtual private networking connection, you will no longer be able to see NetWare servers on the local network.
VPN clients with a permanent IP connection to a VPN tunnel server can use VPN tunneling over that IP connection. For example, suppose that you are in a networked office environment and your network has a VPN tunnel server. You can then use that VPN server to tunnel to any private network that is connected to that VPN server, such as the personnel department’s private network. Thus, you can create a virtual private network by using your direct LAN connection. Data sent from your VPN client to another computer on the LAN is encrypted and secure because you are using a VPN server to connect to the remote computer.
In the following scenario, the VPN client uses Dial-Up Networking over a LAN connection instead of a telephone line. Only one connection to the VPN server is required.
 To connect to a VPN server over a LAN connection
To connect to a VPN server over a LAN connection
Note
The connection speed displayed is only an estimate. If you see a connection speed that seems too high or too low it will not impact performance and should not be cause for concern.
After you successfully connect to a VPN server, all traffic from your computer is first routed to your VPN server, which then forwards your data across the LAN to the remote computer. Your computer behaves as if it were physically connected to the remote network. While the tunnel is open, you continue to see computers and servers on your immediate LAN subnet. However, you might not be able to see hosts and servers on other subnets on your LAN. Contact your network administrator for more information.
With virtual private networking, you can connect your workstation to a remote network by tunneling through the Internet to a VPN server on that network. To do so, you must make two connections. First, you must connect to the Internet through an ISP. Next, you must create a tunnel to the target network. This section explains how to make these connections.
 To connect to the Internet
To connect to the Internet
 To connect to the target network using a tunnel to the VPN server
To connect to the target network using a tunnel to the VPN server
You now have two connections, as seen in the two following similar boxes.
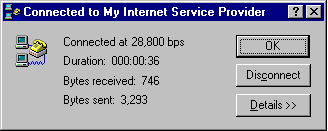
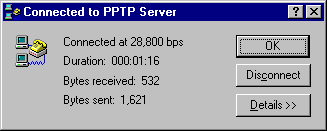
After you connect successfully to the VPN server on the remote network, the ISP routes all traffic sent from your workstation over the Internet to the VPN server. The VPN server then routes the traffic to the correct computer on the remote network. Consequently, you see only computers and servers on the remote network. You no longer see the Internet unless the remote network itself provides access to the Internet.
This section describes VPN security and discusses how to use virtual private networking with firewalls.
When you dial an ISP network access server (NAS), the NAS requires require initial dial-in authentication. This authentication is required only to log on to the NAS; it is not related to Windows NT-based authentication. Check with your ISP for their authentication requirements.
When you dial a VPN tunnel server to connect to a private network, the VPN server requires a standard Windows NT-based logon. Therefore, remote access logon using a computer running Windows 98 is as secure as logging on from a Windows-based computer connected to the local LAN.
Authentication of remote VPN clients is performed using the same PPP authentication methods used for any Dial-up Networking client dialing directly to a RAS server. Microsoft’s implementation of Dial-up Networking supports the CHAP, MS-CHAP, and PAP authentication schemes.
After authentication, all access to a private LAN continues to use the Windows NT-based security model. Access to resources on NTFS drives or to other network resources requires the proper permissions.
For more information about using security on NTFS drives or other network resources, see your product documentation or the Microsoft Windows NT Server Resource Kit (for Microsoft Windows NT version 4.0).
For data encryption, virtual private networking uses the RAS "shared-secret" encryption process. Both the client and the server share a secret, the user’s password. Both the client and the server uses the secret to generate an initial 40-bit encryption key, then uses the key to encrypt and decrypt all data that it passes over the Internet. When you are connecting to a Windows NT 4 RAS Server with Service Pack 4 or later, the key changes on every packet. For earlier versions of Windows NT 4, the key changes every 256 packets.
Note
The process by which the client and server generate the initial key occurs only when MS-CHAP is used.
Users in the United States and Canada can obtain a 128-bit session key through a cryptography pack for use inside the US. Contact your Microsoft reseller for more information. When 128-bit encryption is used, the initial key is based on the password and a unique MS-CHAP challenge.
To protect the VPN server from malicious attacks, you can enable PPTP filtering on the VPN server. With PPTP filtering, the VPN server on the private network accepts and routes only authorized, encrypted PPTP packets from authenticated users.
PPTP filtering is enabled on the VPN server. For step-by-step instruction on enabling PPTP filtering, see the white paper "Installing, Configuring, and Using PPTP with Microsoft Clients and Servers" at http://www.microsoft.com/ communications/.
PPTP traffic uses TCP port 1723, and IP protocol uses ID 47, as assigned by the Internet Assigned Numbers Authority (IANA). Virtual private networking can be used with most firewalls and routers by enabling traffic destined for TCP port 1723 and protocol 47 to be routed through the firewall or router.
Firewalls ensure corporate network security by strictly regulating data that comes into the private network from the Internet. An organization can deploy a VPN server running Windows NT Server 4.0 behind its firewall. The VPN server accepts PPTP packets passed to the private network from the firewall and extracts the PPP packet from the IP datagram, decrypts the packet, and forwards the packet to the computer on the private network.