 To share an application on a network
To share an application on a network
This section describes how to install and remove applications locally or on a network. It also describes how to configure distributed applications across a network using Distributed COM.
Before you install and configure applications for use with Windows 98, consider the following questions:
To share some large applications, you must run a separate setup on the server and on the workstation. Check the documentation for the application before attempting to share it across the network.
How you install and configure an application depends on whether it was created for Windows 95, Windows 3.1, or MS-DOS. This section discusses how to install and configure applications written for each operating system and how to find out whether your application is compatible with Windows 98. For more information about installing and configuring distributed applications across a network using Distributed COM, see "Distributing Applications Across a Network" later in this chapter.
Windows 98 simplifies installing Win32-based applications by providing an Add/Remove Programs option in Control Panel. When you install an application using this option, Windows 98 does the following:
If you upgrade by placing Windows 98 in the Windows 3.x directory, you do not need to reinstall applications. Setup automatically moves information about currently installed applications to the registry. Setup also converts existing Program Manager groups and adds them to the Programs menu on the Start menu.
If you install Windows 98 in a separate directory, you must reinstall all Windows-based applications to ensure that they work properly under Windows 98. Copying GRP and INI files from your previous \Windows directory is not sufficient to run applications under Windows 98.
When a Windows-based setup application creates an application group and icons, Windows 98 creates folders and icons for the Programs menu on the Start menu. If a setup application fails to create a shortcut correctly, you can do it manually. For information about adding shortcuts to the Start menu, see the section titled "Configuring the Start and Programs Menus" in Chapter 6, "Configuring the Active Desktop and Active Channels."
You generally install an MS-DOS-based application by running its Setup.exe file. When you install the application, Windows 98 copies information about the application from Apps.inf to the application’s program information file (PIF). If the application was installed under an earlier version of Windows, Setup automatically moves its settings to the new Apps.inf. If there is no information about the application in Apps.inf, Windows 98 uses default settings instead, or you can manually set the properties, as described in "Configuring MS-DOS-based Applications" later in this chapter.
Note
Windows 98 has no separate PIF Editor. To configure an application, right-click its executable file, and then click Properties.
For more information about whether a specific application runs under Windows 98, check the Windows 98 Readme.txt file. If you do not find an application listed in Readme.txt, check with the application’s manufacturer or your software vendor. Windows 98 provides a utility that makes an incompatible application compatible with Windows 98. This utility is a file named Mkcompat.exe in the \Windows\System directory. For more information, see "How Windows 98 Accommodates Application Problems" later in this chapter.
For more information about installing applications after you have installed Windows 98, see online Help.
This section describes how to share and install applications over a network. It first explains how to make applications available over a network. It then explains an optional procedure for giving users a master list of available applications.
You can share most applications on a network by installing them on a network server and then creating shortcuts to them on the client computers. Users can run an application by double-clicking the shortcut or by double-clicking the application’s icon in Network Neighborhood.
You can also install applications over a network by using software distribution channels, a type of Active Channel that updates subscriber’s computers at regular intervals. For more information about software distribution channels, see Chapter 6, "Configuring the Active Desktop and Active Channels."
 To share an application on a network
To share an application on a network
For more information about creating shortcuts, see online Help. For information about creating and distributing custom shortcuts using system policies, see Chapter 8, "System Policies." For more information about configuring Active Desktop toolbars, see Chapter 6, "Configuring the Active Desktop and Active Channels."
If users will be installing applications from source files stored on a network, you can create an Apps.ini file that contains a master list of applications and their network locations. When a user’s registry contains a reference to Apps.ini, a new tab named Network Install appears under Add/Remove Programs, in Control Panel. The Network Install tab lists all the applications that appear in the Apps.ini file and that can be installed from the server.
 To create an Apps.ini file on a network server
To create an Apps.ini file on a network server
[AppInstallList]
application name = [*] UNC path
For application name, substitute the name that you want users to see on the Network Install tab. For UNC path, substitute the network location of the Setup application. If a Setup application cannot work with universal naming convention (UNC) names, include an asterisk before it. For example:
Microsoft Word 97=*\\applications\forusers\word97\setup.exe
 To display the applications listed in Apps.ini on a client computer’s Network Install tab
To display the applications listed in Apps.ini on a client computer’s Network Install tab
Hkey_Local_Machine/Software/Microsoft/Windows/Current Version
\\myserver\myshare\apps.ini
For information about adding registry settings in setup scripts, see Appendix D, "Msbatch.inf Parameters for Setup Scripts." For information about adding registry settings using system policies, see Chapter 8, "System Policies."
This section describes how to use the Distributed COM Configuration tool to configure clients, servers, and applications. The Distributed COM Configuration tool lets you configure 32-bit COM and Distributed COM distributed applications to run across computers by specifying properties for the distributed application, such as the locations of application components and security for those components.
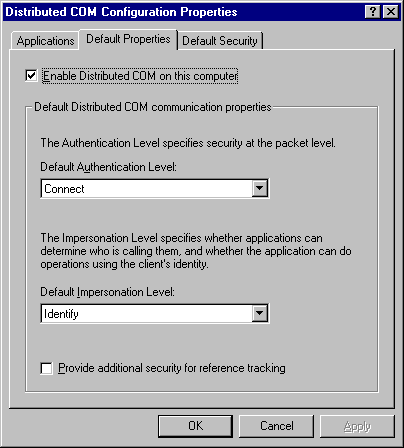
Note
Application configuration can also be specified in the application itself. If so, the settings override any settings you choose in the DCOM Configuration tool.
For additional procedures on using the Distributed COM Configuration tool to configure applications, see the Distributed COM Configuration tool’s online Help system.
For more information about setting security levels and permissions for Distributed COM applications, see Chapter 9, "Security."
A Distributed COM computer running Windows 98 can be either a client, a server, or both. A client makes calls to a component, and a server gets calls. Thus, if computer A is running an application that calls a component on computer B, computer A is acting as a client and computer B is acting as a server. If the component on computer B also calls a component on computer C, computer B is acting both as a client and as a server.
Using the Distributed COM Configuration tool, you can configure your computer as a client, a server, or both. By default, your computer is configured as a client but not as a server. Before you can use dcomcnfg your computer must be configured for user-level security. For more information, see Chapter 18, "Logon, Browsing, and Resource Sharing."
 To configure your computer as a DCOM client and server
To configure your computer as a DCOM client and server
You can configure the client computer to use authentication when a connection is made to the server. You can also configure the server to use authentication when a connection is made to a server. If either the client or the server requests authentication, both will need to use authentication.
It is highly recommended that you configure your computer to use authentication if it will be used as a server. Otherwise, client computers can call the server without being authenticated.
If your computer is not part of a Windows NT domain and has no access to Windows NT domain security, authentication will fail. If either the client or the server request authentication, the connection will fail. Thus, if you are certain that your computer is a client and not a server, and your computer is not part of a Windows NT domain, you might want to set that computer not to use authentication. However, even if you do so, the connection will fail if the server requests authentication.
If your computer is a server and is part of a Windows NT domain, but it is configured to use share-level security, a secure connection will fail. In that case, you might want to set your computer to use user-level security. For more information about user-level security, see Chapter 9, "Security" and Chapter 18, "Logon, Browsing, and Resource Sharing."
Before you can use dcomcnfg your computer must be configured for user-level security. For more information, see Chapter 18, "Logon, Browsing, and Resource Sharing."
 To set authentication on communications between applications
To set authentication on communications between applications
With impersonation, one process can take on the security attributes of another process. For example, a server process can impersonate a client process to complete a task involving objects to which the server does not normally have access. The server application can impersonate the client application only on the computer running the server application.
You can set impersonation levels for a Distributed COM application on a Windows 98 Distributed COM client, enabling Windows NT Distributed COM servers to impersonate the client.
In most cases, the default settings are correct. However, if you want to change the impersonation level, see online Help.
The first step in configuring an application for Distributed COM is to specify the location of the server application that will be accessed by the computer running the client application. You do this on the computer running the client application. Before you can use dcomcnfg your computer must be configured for user-level security. For more information, see Chapter 18, "Logon, Browsing, and Resource Sharing."
 To set the location of a Distributed COM application
To set the location of a Distributed COM application
You can create an access control list that specifies the user accounts that will have permission to have access to or start applications, on either the server or the application, or both. Before a component can run, Distributed COM validates the user name using whatever authentication mechanism is configured and checks the user name against the access control list. The permissions you can set depend on the server’s operating system:
Note
If you set custom permissions for a Distributed COM application, the custom permissions will override any default permissions that have been set for all applications.
For information about how to use the Distributed COM Configuration tool to configure users and permissions, see online Help.
The extent to which a Distributed COM client computer running Windows 98 can start or access a Distributed COM–enabled application on a server depends on the server’s operating system:
If you installed applications through Add/Remove Programs in Control Panel, you can safely remove them in the same way. Because the application’s components are tracked through the registry, Windows 98 deletes all of the application's files unless those files are being used by another application. Shared files are retained on the hard disk. You see a prompt if you try to remove a shared file.
Removing a Win16-based or MS-DOS-based application is not always straightforward. You can delete the directory that contains the application, but additional files belonging to the application (especially in a Win16-based application) are often located in the \Windows or \Windows\System directory. There is no way to determine which applications placed certain files in these directories, so some of the application’s files may be left behind on your hard disk.
If you try to delete all the files of an application installed in the \Windows or \Windows\System directory, you might delete a system file used by other applications. If this happens, the other applications will not run properly and must be reinstalled.
To avoid problems when removing Win16-based or MS-DOS-based applications, check their documentation for instructions about removing them, and keep backup copies of dynamic-link libraries (DLLs) and other essential system files, in case you need to restore them.