

Setting Up Java Custom Security
You can deploy Internet Explorer with the default settings, or you can configure Java custom settings, which explicitly define the Java permissions for signed and unsigned applets. The options for configuring Java custom settings are the same whether you access them from Internet Explorer 5, the Internet Explorer Customization wizard, or the IEAK Profile Manager. For more information about using the Internet Explorer Customization wizard and IEAK Profile Manager, see Chapter 15, "Running the Internet Explorer Customization Wizard" and Chapter 22, "Keeping Programs Updated."
Important You can only configure Java custom settings if the Microsoft Virtual Machine is installed on your computer.
Configuring Java Custom Security
You can configure Java custom security by using the following methods:
- In Internet Explorer, click the Tools menu, click Internet Options, and then click the Security tab.
- You can use the Internet Explorer Customization wizard to create custom packages of Internet Explorer that include Java custom settings. If you are a corporate administrator, you can also lock down these settings to prevent users from changing them.
- After the browser is deployed, you can use the IEAK Profile Manager to manage Java custom settings through the automatic browser configuration feature of Internet Explorer. You can automatically push the updated security zone settings to each user's desktop computer, enabling you to manage security policy dynamically across all computers on the network.
You can view and change Java custom settings for each security zone. The following section describes how to configure Java custom settings.
 To view and edit Java custom settings
To view and edit Java custom settings
- On the Tools menu, click Internet Options.
- Click the Security tab.
- Click a security zone.
- Click Custom Level.
- In the Java Permissions area, select Custom.
- Click Java Custom Settings.
- As necessary, perform the following tasks:
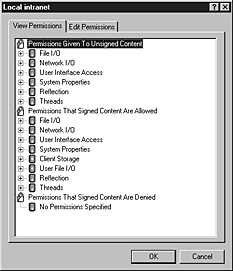
- To view Java permissions, click the View Permissions tab.
This tab displays permissions in a hierarchical tree that you can expand and collapse. Permissions are organized into the following categories:
Permissions Given To Unsigned Content - Unsigned Java applets that request these permissions can run without user prompting.
Permissions That Signed Content Are Allowed - Signed Java applets that request these permissions can run without user prompting.
Permissions That Signed Content Are Denied - Signed Java applets are denied these permissions.
The following illustration shows the Java permission categories.
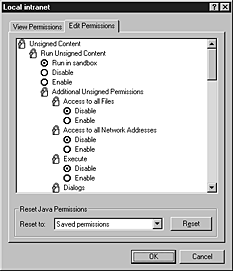
- To edit Java permissions, click the Edit Permissions tab, and then select the options you want for more precise control of Java permissions. At any time, you can click the Reset button to reset the Java custom settings to the last saved permissions or to the default high, medium, or low security settings. For more information about specific Java permissions, see "Selecting Java Custom Settings" later in this chapter.
The following illustration shows the options you can set for Java permissions.
Selecting Java Custom Settings
The Java Custom Settings button on the Security tab gives you additional control over Java permissions. You can enable or disable specific Java permissions depending on the needs of your organization and its users. For more information about how to use the Java custom settings, see "Configuring Java Custom Security" earlier in this chapter.
Java custom settings for Internet Explorer are grouped into two categories: Unsigned Content and Signed Content. The following tables identify the default value for each option and the level of security.
Unsigned Content
Java custom option |
High
security |
Medium security |
Low
security |
| Run Unsigned Content |
| Run Unsigned Content |
Run in sandbox |
Run in sandbox |
Run in sandbox |
| Additional Unsigned Permissions |
| Access to all files |
Disable |
Disable |
Disable |
| Access to all network addresses |
Disable |
Disable |
Disable |
| Execute |
Disable |
Disable |
Disable |
| Dialog |
Disable |
Disable |
Disable |
| System information |
Disable |
Disable |
Disable |
| Printing |
Disable |
Disable |
Disable |
| Protected scratch space |
Disable |
Disable |
Disable |
| User-selected file access |
Disable |
Disable |
Disable |
Signed Content
Java custom option |
High
security |
Medium security |
Low
security |
| Run Signed Content |
| Run Signed Content |
Prompt |
Prompt |
Prompt |
| Additional Signed Permissions |
| Access to all files |
Prompt |
Prompt |
Disable |
| Access to all network addresses |
Prompt |
Prompt |
Disable |
| Execute |
Prompt |
Prompt |
Disable |
| Dialog |
Prompt |
Prompt |
Disable |
| System information |
Prompt |
Prompt |
Disable |
| Printing |
Prompt |
Prompt |
Disable |
| Protected scratch space |
Prompt |
Enable |
Disable |
| User-selected file access |
Prompt |
Enable |
Disable |
The following sections describe the settings for the Unsigned Content and Signed Content groups.
Unsigned Content
The Run Unsigned Content group determines whether unsigned applets can run in the zone. This group has the following settings:
- Run in sandbox, which runs unsigned Java applets for this zone in a Java sandbox that you specify. You can enable or disable individual options in the Additional Unsigned Permissions category.
- Disable, which disables running unsigned applets for this zone. All options in the Additional Unsigned Permissions category are disabled and shaded.
- Enable, which enables running unsigned applets for this zone. All options in the Additional Unsigned Permissions category are enabled.
The Additional Unsigned Permissions option determines whether unsigned applets can have additional permissions, such as access to network addresses and the ability to run other applications. If you disable the ability to Run Unsigned Content, Internet Explorer automatically disables all of these options.
- Access to all files - This option determines whether unsigned applets can have read access to all the files on the users' systems. This option has these settings:
- Disable, which prevents unsigned applets from having read access to all the files on the users' systems.
- Enable, which allows unsigned applets to have read access to all the files on the users' systems.
- Access to all network addresses - This option determines whether unsigned applets can access network addresses. This option has these settings:
- Disable, which prevents unsigned applets from having access to network addresses.
- Enable, which allows unsigned applets to have access to network addresses.
- Execute - This option determines whether unsigned applets can run other applications. This option has these settings:
- Disable, which prevents unsigned applets from running other applications.
- Enable, which allows unsigned applets to run other applications.
- Dialogs - This option determines whether unsigned applets can create file dialog boxes. This option has these settings:
- Disable, which prevents unsigned applets from creating file dialog boxes.
- Enable, which allows unsigned applets to create file dialog boxes.
- System information - This option determines whether unsigned applets can read system properties. This option has these settings:
- Disable, which prevents unsigned applets from reading system properties.
- Enable, which allows unsigned applets to read system properties.
- Printing - This option determines whether unsigned applets can access printer resources. This option has these settings:
- Disable, which prevents unsigned applets from accessing printer resources.
- Enable, which allows unsigned applets to access printer resources.
- Protected scratch space - This option determines whether unsigned applets can use storage space on the hard drive. This option has these settings:
- Disable, which prevents unsigned applets from using storage area on the hard disk.
- Enable, which allows unsigned applets to use storage area on the hard disk.
- User-selected file access - This option determines whether unsigned applets can access selected files. This option has these settings:
- Disable, which prevents unsigned applets from accessing any files (users are not prompted for permission).
- Enable, which prompts users about whether unsigned applets can access selected files.
Signed Content
The Run Signed Content option determines whether users can run signed applets. This option has these settings:
- Prompt, which sets individual options in the Additional Signed Permissions category to Prompt. You can disable or enable each individual option.
- Disable, which disables running signed applets for this zone. All options in the Additional Signed Permissions category are disabled and shaded.
- Enable, which enables running unsigned applets for this zone. All options in the Additional Signed Permissions category are enabled.
The Additional Signed Permissions options determine whether signed applets can have additional permissions, such as access to network addresses and the ability to run other applications. If you disable the ability to Run Signed Content, Internet Explorer automatically disables all of these options.
- Access to all files - This option determines whether signed applets can have read access to all the files on the users' systems. This option has these settings:
- Prompt, which prompts users before signed applets can have read access to all the files on the users' systems.
- Disable, which prevents signed applets from having read access to all the files on the users' systems.
- Enable, which allows signed applets to have read access to all the files on the users' systems.
- Access to all network addresses - This option determines whether signed applets can access network addresses. This option has these settings:
- Prompt, which prompts users about whether signed applets can access network addresses.
- Disable, which prevents signed applets from accessing network addresses.
- Enable, which allows signed applets to access network addresses.
- Execute - This option determines whether signed applets can run other applications. This option has these settings:
- Prompt, which prompts users about whether signed applets can run other applications.
- Disable, which prevents signed applets from running other applications.
- Enable, which allows signed applets to run other applications.
- Dialogs - This option determines whether signed applets can create file dialog boxes. This option has these settings:
- Prompt, which prompts users about whether signed applets can create file dialog boxes.
- Disable, which prevents signed applets from creating file dialog boxes.
- Enable, which allows signed applets to create file dialog boxes.
- System information - This option determines whether signed applets can read system properties. This option has these settings:
- Prompt, which prompts users about whether signed applets can read system properties.
- Disable, which prevents signed applets from reading system properties.
- Enable, which allows signed applets to read system properties.
- Printing - This option determines whether signed applets can access printer resources. This option has these settings:
- Prompt, which prompts users about whether signed applets can access printer resources.
- Disable, which prevents signed applets from accessing printer resources.
- Enable, which allows signed applets to access printer resources.
- Protected scratch space - This option determines whether signed applets can use storage space on the hard drive. This option has these settings:
- Prompt, which prompts users about whether signed applets can use storage area on the hard disk.
- Disable, which prevents signed applets from using storage area on the hard disk.
- Enable, which allows signed applets to use storage area on the hard disk.
- User-selected file access - This option determines whether signed applets can access selected files. This option has these settings:
- Prompt, which prompts users about whether signed applets can access selected files.
- Disable, which prevents signed applets from accessing any files (users are not prompted for permission).
- Enable, which prompts users about whether signed applets can access selected files.




