Security
|


|
An End-to-End Troubleshooting Example
In the following scenario, a travel site called Exploration Air has developed a Web-based employee benefits application that uses IIS 5.0. The application can be accessed from the Internet and corporate intranet. Because the application is open to the Internet, security must be high.
All employees are validated before gaining access to the server and all data is encrypted to prevent people from “sniffing” the data as it moves across the Internet. The benefits application in this scenario deals with medical, dental, and legal assistance, as well as stock options, stock purchase plans, investment, and relocation benefits.
To access these resources, the Web application requires data from several sources:
- A Microsoft® SQL Server 7.0 database that contains all the corporate online benefits data. This is a complex database schema including 181 tables, 27 stored procedures, and 12 triggers. The database is approximately 6.5 gigabytes (GB) in size and grows about 250 MB per month.
- A legacy Oracle database on UNIX that contains the original Human Resources information, including payroll. For the purposes of this application, it is read-only and is used to verify the user.
- The IIS Configuration Store that is used to gather configuration details about the server, which it then displays on the benefits homepage.
- A “hit count” file that lists the number of times the home page has been accessed.
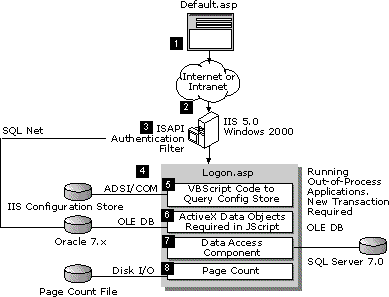
This scenario describes eight main steps, which are depicted in Figure the figure above:
- The user logs on.
- An ISAPI authentication filter is called.
- IIS 5.0 attempts to authenticate the user.
- IIS 5.0 loads the logon page Logon.asp.
- Logon.asp attempts to read data from the configuration store.
- ADO performs a lookup on the Human Resources page.
- A data access component written in Microsoft® Visual Basic® 5.0 performs a complex update.
- The page count is updated using a Page Count component.
In each step, issues that could prevent you from proceeding to the next step are outlined.
See the following:
© 1997-1999 Microsoft Corporation. All rights reserved.
