Security |
The Windows operating system is configured to accept only valid users. Because the Internet is extremely anonymous—in that very few Web sites prompt visitors for a user name and password—IIS 5.0 creates the IUSR_computername account so that real Windows accounts can be used in an anonymous Internet. This account is granted to anonymous users who then use a random password, defined when IIS 5.0 is set up, on the local computer. This account gives anonymous users the right to log on locally. Anonymous user access can be reset to use any valid Windows account.
Note With IIS 5.0 you can set up different anonymous accounts for different Web sites, virtual directories, directories, and files. This provides a great deal of flexibility and fine control, telling what accounts will be used where within the site.
If the computer running Windows is a stand-alone server, the IUSR_computername account is on the local server. If the server is a Domain Controller, the IUSR_computername account is defined for the domain.
Windows uses IUSR_computername when a user is authenticated by IIS 5.0 with Anonymous authentication. In other words, a real Windows user account is being used for all nontrusted anonymous access.
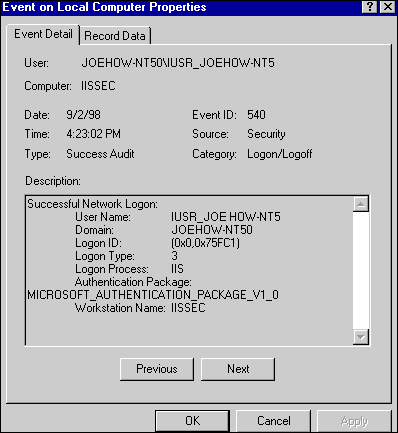
The figure below shows an example of what is entered into the Event Viewer in Windows 2000 when Anonymous authentication is used. Note that the logon process is performed by IIS 5.0 itself and that the logon is a network logon (the logon type is 3 in the audit log entry). This is because the Allow IIS to control password option is enabled. If this option were disabled, the logon would be interactive (the logon type would be 2 in the audit log entry).
See the following: