Security |
Practically all data held on computers has some value. Sometimes this value is small, such as simple e-mail messages between friends saying “Hi!” Other times the value is great, such as documents pertaining to military secrets or to business tactics and strategies.
When determining the appropriate level of security for your Web servers, you need to consider the following:
Note The cost to the organization if data is leaked also includes the intangible cost involving loss of client or shareholder faith.
As shown in the figure below, as a system becomes more secure, it also becomes less usable. At some point you might realize that a system is so secure that your intended audience cannot access your service.
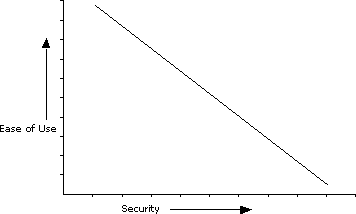
Also note that there is a point at which it is not worth further securing the system, as the cost of deploying the security becomes greater than the cost associated with the risk of a security attack. Is it worth spending $100,000 to secure data valued at only $25,000?
Once you understand the value of your data, the deployment cost, and the usability tradeoffs, you can begin planning how to secure your system. This is a very large field and is beyond the scope of this book. For more information about assessing values and costs, see “Additional Resources” at the end of this section.