The following table shows the functions applications can use to compute secure digests of data and to create and verify digital signatures.
Function |
Description |
| CryptCreateHash | Creates an empty hash object |
| CryptDestroyHash | Destroys a hash object |
| CryptGetHashParam | Retrieves a hash object parameter |
| CryptHashData | Hashes a block of data, adding it to the specified hash object |
| CryptHashSessionKey | Hashes a session key, adding it to the specified hash object |
| CryptSetHashParam | Sets a hash object parameter |
| CryptSignHash | Signs the specified hash object |
| CryptVerifySignature | Verifies a digital signature, given a handle to the hash object that was signed |
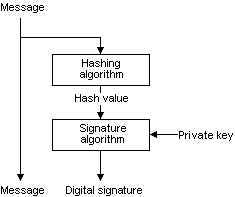
To create a digital signature from a message, create a hash value, also known as a message digest, from the message. Then, use the signer's private key to sign the hash value. The following illustration shows the process for creating a digital signature.

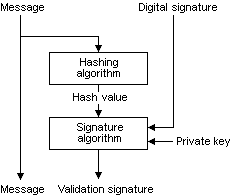
To verify a digital signature, both the message and the signature are required. First, a hash value must be created from the message in the same way as it was done when the signature was created. This hash value is then verified against the signature, using the public key of the signer. If the hash value and the signature match, you can be confident that the message is the one originally signed and that it has not been tampered with. The following illustration shows the process of verifying a digital signature.
A hash value consists of a small amount of binary data, typically 160 bits. It is produced using a hashing algorithm.
All hash values share the following properties, regardless of the algorithm used: